Product Description
This NCA Cybersecurity Toolkit is a comprehensive, ready-to-use resource for implementing and maintaining cybersecurity controls in alignment with the requirements and guidance issued by the Saudi Arabia National Cybersecurity Authority (NCA) (nca.gov.sa). It is designed to help organizations operating in or with the Kingdom of Saudi Arabia establish, enhance, and demonstrate compliance with NCA cybersecurity frameworks and regulations.
Developed in Microsoft Office format, all documents are fully customizable to address your organization’s specific context, sector, and risk profile. Each template is pre-structured with standard content and clearly highlighted example text to guide users in inserting organization-specific details. Full example documents are also included to support a smooth and efficient implementation, assessment, and ongoing governance process.
This toolkit not only simplifies your NCA cybersecurity compliance journey but also serves as a vital resource for awareness, governance, and training on cybersecurity best practices. Designed for business leaders, CISOs, cybersecurity practitioners, risk and compliance professionals, and consultants, it provides structured guidance to:
-
Interpret NCA cybersecurity requirements and controls;
-
Translate them into practical policies, procedures, and records;
-
Evidence compliance during internal reviews and regulatory assessments.
Whether you are establishing a cybersecurity governance framework from scratch or enhancing existing controls to meet NCA expectations, this toolkit gives you a solid foundation for a consistent, auditable, and efficient compliance process.
Why Compliance with NCA Cybersecurity Requirements Matters?
The Saudi National Cybersecurity Authority (NCA) is the primary government body responsible for overseeing and regulating cybersecurity in the Kingdom of Saudi Arabia. Its frameworks, controls, and mandates set the baseline requirements that organizations must meet to protect national interests, critical infrastructure, and sensitive information assets. Compliance with NCA cybersecurity requirements is not only a regulatory expectation, but also a strategic necessity to reduce cyber risk, avoid penalties, and maintain the trust of regulators, customers, and partners. By aligning your policies, processes, and technical controls with NCA guidance, your organization demonstrates due diligence, strengthens its overall security posture, and supports the Kingdom’s broader vision for a resilient and secure digital economy.
Who Must Comply with NCA Cybersecurity Requirements?
NCA cybersecurity requirements apply to a broad range of entities operating in or with the Kingdom of Saudi Arabia. This includes government ministries and agencies, critical national infrastructure operators, financial institutions, telecom and technology providers, as well as private sector organizations that process, store, or transmit sensitive or regulated information. Service providers, outsourcing partners, and third parties connected to these entities are also expected to align with NCA controls as part of the wider supply-chain security mandate. In practice, any organization that supports national services, digital infrastructure, or key economic sectors in Saudi Arabia should treat NCA compliance as a core obligation, integrating its requirements into governance, risk management, and day-to-day cybersecurity operations.
What is included in the toolkit?
- 80+ NCA Cybersecurity Documentation Templates – including policies, procedures, standards, registers, controls, checklists, tools, and other supporting documents mapped to NCA cybersecurity requirements.
- Available as an instant download after purchase
NCA Cybersecurity Documentation Pack
A complete and comprehensive documentation package designed to assist organizations, consultants, and service providers in successfully implementing and evidencing compliance with Saudi Arabia National Cybersecurity Authority requirements.
Content of NCA Cybersecurity Toolkit:
-
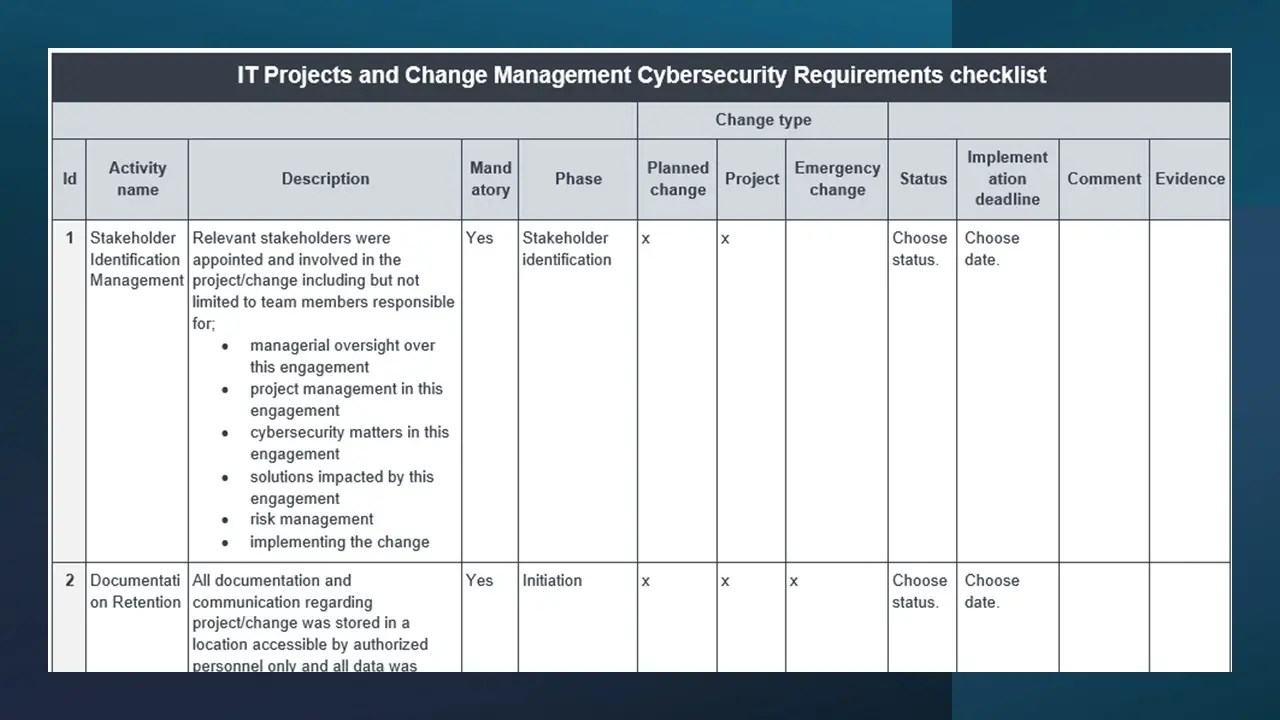
Checklist – Cybersecurity Requirements in IT Projects and Change Management (Template).docx
-
Checklist – Cybersecurity Requirements in Software Development (Template).docx
-
Cybersecurity Organizational Structure (Template).docx
-
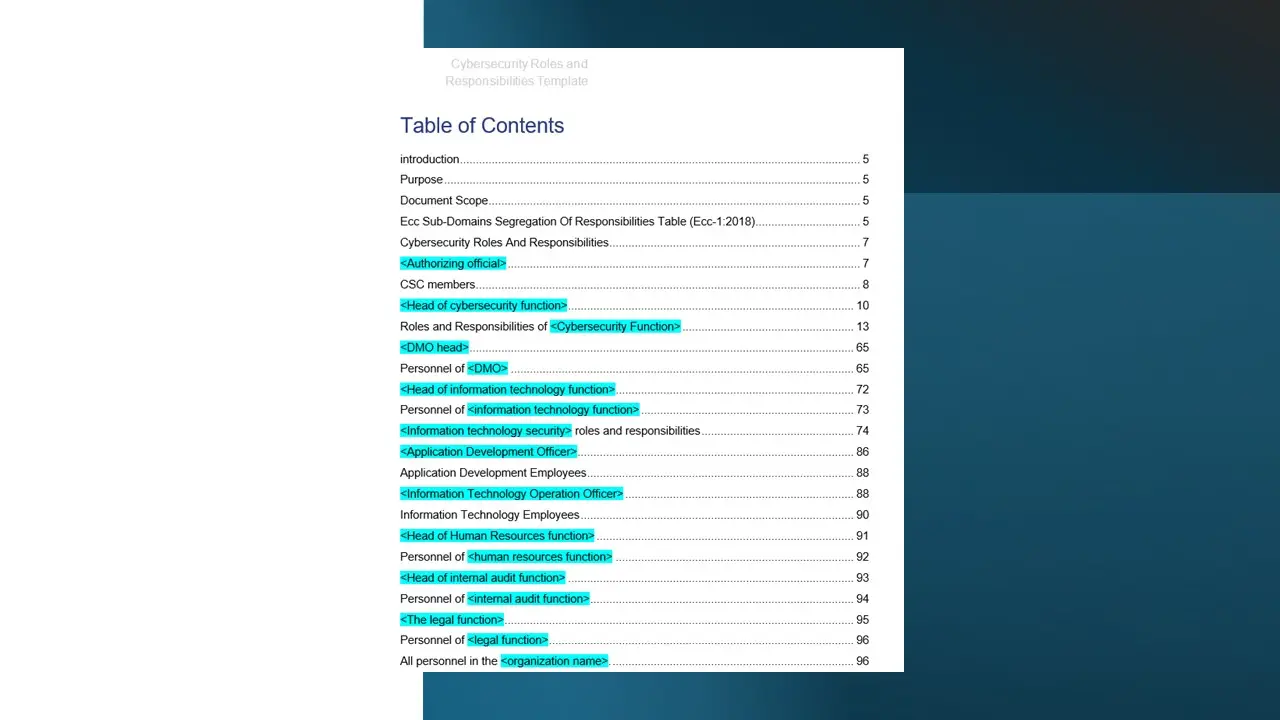
Cybersecurity Roles and Responsibilities (Template).docx
-
Cybersecurity Steering Committee Regulating Document (Template).docx
-
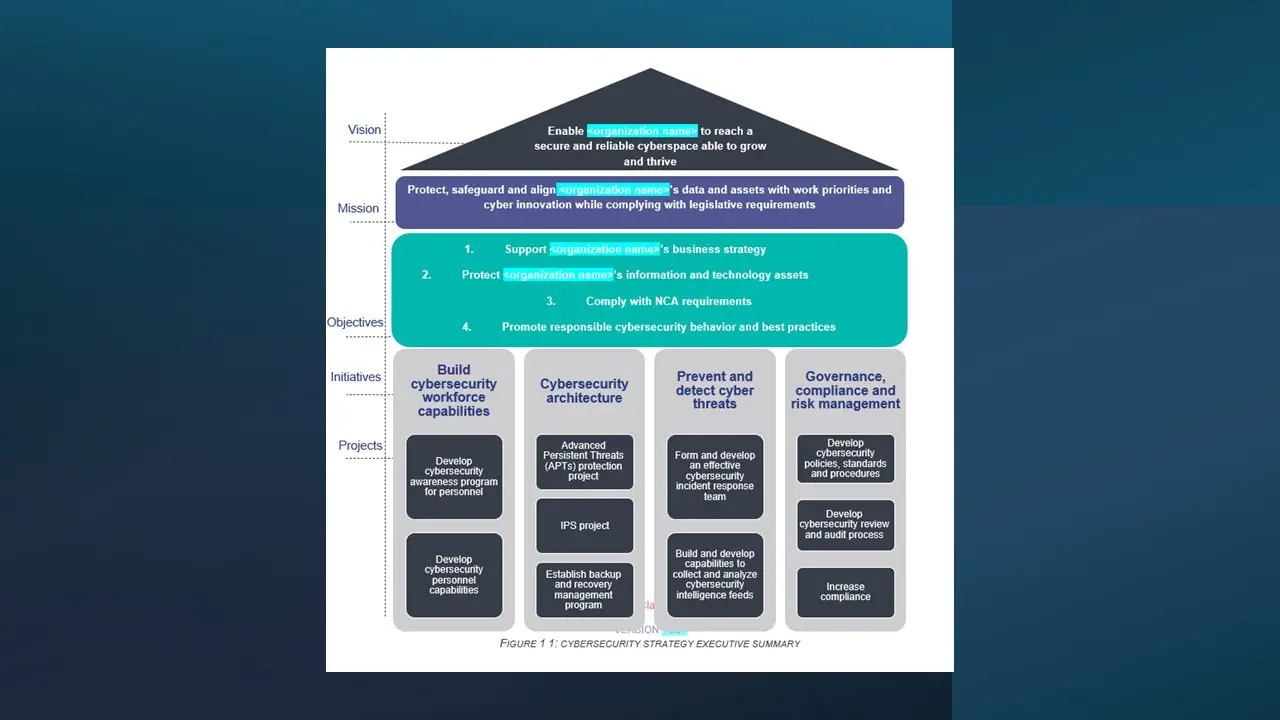
Cybersecurity Strategy and Roadmap (Template).docx
-
Form – Confidentiality Agreement (Template).docx
-
Form – Policy Undertaking (Template).docx
-
Policy – Anti-Malware Protection (Template).docx
-
Policy – Asset Acceptable Use (Template).docx
-
Policy – Asset Management (Template).docx
-
Policy – Backup and Recovery (Template).docx
-
Policy – Cloud Computing and Hosting Cybersecurity (Template).docx
-
Policy – Compliance with Cybersecurity Legislation and Regulations (Template).docx
-
Policy – Configuration and Hardening (Template).docx
-
Policy – Corporate Cybersecurity (Template).docx
-
Policy – Cryptography (Template).docx
-
Policy – Cybersecurity Business Continuity (Template).docx
-
Policy – Cybersecurity Event Logging and Monitoring Management (Template).docx
-
Policy – Cybersecurity Incident and Threat Management (Template).docx
-
Policy – Cybersecurity Industrial Control Systems (Template).docx
-
Policy – Cybersecurity Review and Audit (Template).docx
-
Policy – Cybersecurity Risk Management (Template).docx
-
Policy – Database Security (Template).docx
-
Policy – Data Cybersecurity (Template).docx
-
Policy – Email Security (Template).docx
-
Policy – Human Resources (Template).docx
-
Policy – Identity and Access Management (Template).docx
-
Policy – Network Security (Template).docx
-
Policy – Patch Management (Template).docx
-
Policy – Penetration Testing (Template).docx
-
Policy – Physical Security (Template).docx
-
Policy – Server Security (Template).docx
-
Policy – Secure Software Development Life Cycle (SSDLC) (Template).docx
-
Policy – Storage Media (Template).docx
-
Policy – Third-Party Cybersecurity (Template).docx
-
Policy – Vulnerability Management (Template).docx
-
Policy – Web Application Protection (Template).docx
-
Policy – Workstations, Mobile Devices and BYOD Security (Template).docx
-
Procedure – Cybersecurity Audit (Template).docx
-
Procedure – Cybersecurity Document Development (Template).docx
-
Procedure – Cybersecurity Risk Management (Template).docx
-
Procedure – Vulnerability Management (Template).docx
-
Program – Cybersecurity Awareness Program (Template).docx
-
Register – Cybersecurity Audit Plan (Template).xlsx
-
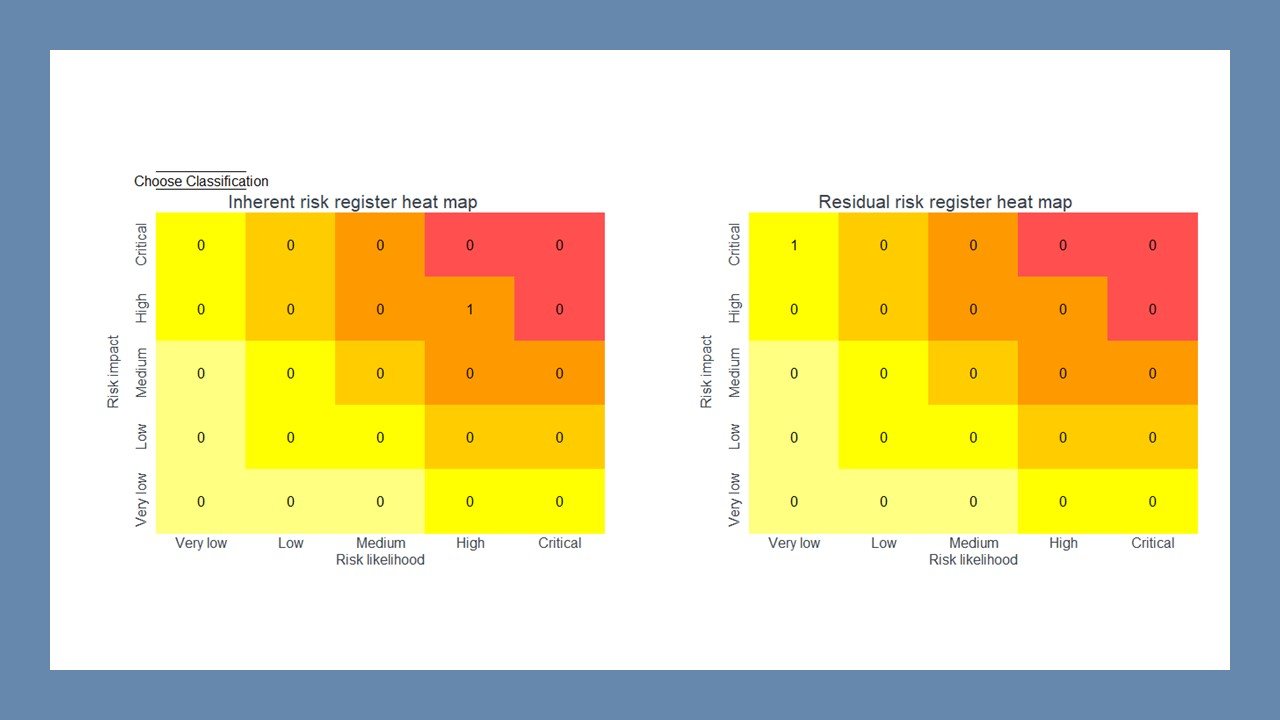
Register – Cybersecurity Risk Management (Template).xlsx
-
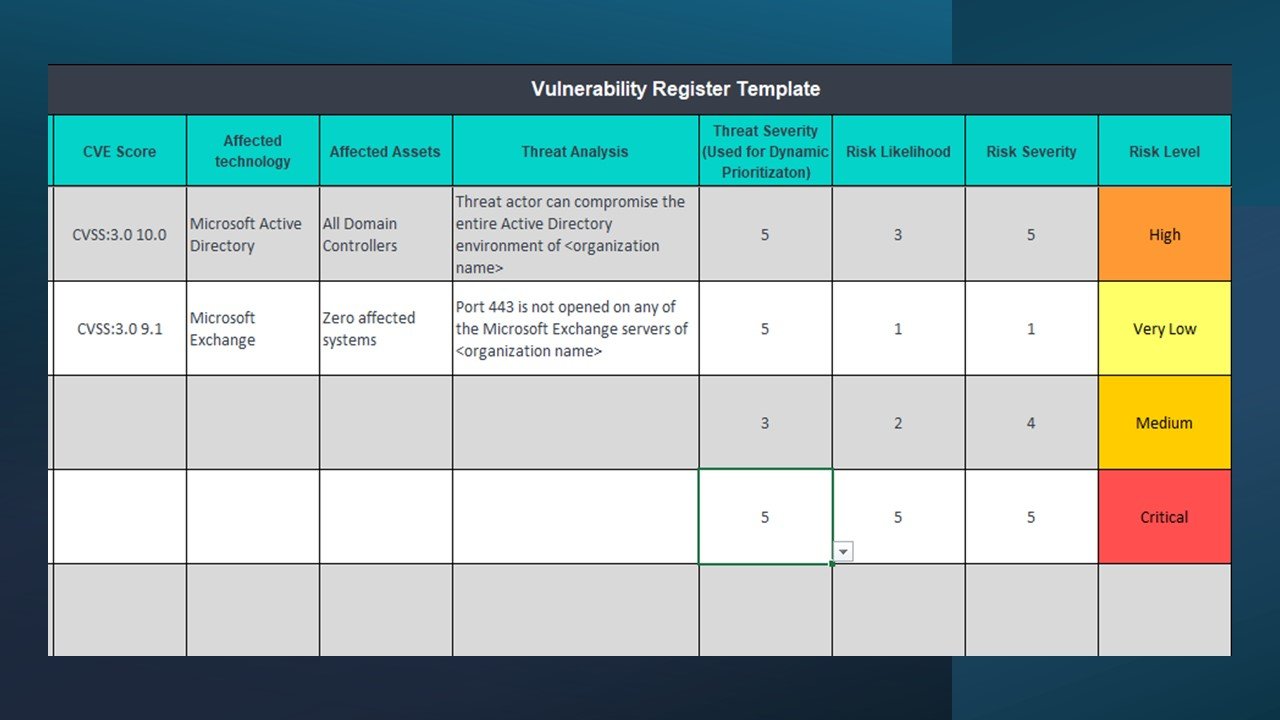
Register – Vulnerability Register (Template).xlsx
-
Report – Cybersecurity Audit (Template).docx
-
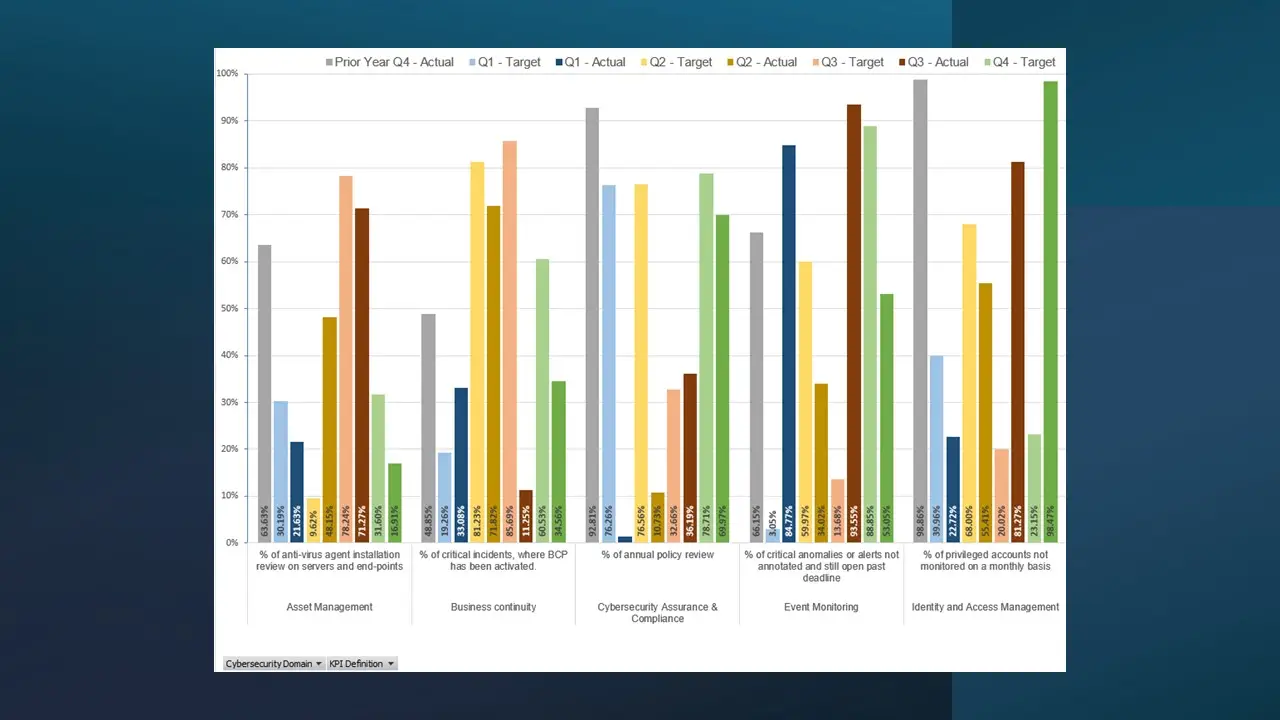
Report – Key Performance Indicator Report (Template).xlsx
-
Standard – Advanced Persistent Threat (APT) (Template).docx
-
Standard – Asset Classification (Template).docx
-
Standard – Asset Management (Template).docx
-
Standard – Backup and Recovery (Template).docx
-
Standard – Cryptography (Template).docx
-
Standard – Cybersecurity Event Logging and Monitoring Management (Template).docx
-
Standard – Data Diode (Template).docx
-
Standard – Data Loss Prevention (Template).docx
-
Standard – Data Protection (Template).docx
-
Standard – Database Security (Template).docx
-
Standard – DDoS Protection (Template).docx
-
Standard – Endpoint Detection and Response (EDR) (Template).docx
-
Standard – Email Protection (Template).docx
-
Standard – Identity and Access Management (Template).docx
-
Standard – Key Management (Template).docx
-
Standard – Malware Protection (Template).docx
-
Standard – Mobile Device Security (Template).docx
-
Standard – Network Detection and Response (NDR) (Template).docx
-
Standard – Network Security (Template).docx
-
Standard – OT and ICS Security (Template).docx
-
Standard – Patch Management (Template).docx
-
Standard – Penetration Testing (Template).docx
-
Standard – Physical Security (Template).docx
-
Standard – Privileged Access Workstation (Template).docx
-
Standard – Proxy (Template).docx
-
Standard – Secure Configuration and Hardening (Template).docx
-
Standard – Secure Coding Controls (Template).docx
-
Standard – Server Security (Template).docx
-
Standard – Social Media Security (Template).docx
-
Standard – Virtualization Security (Template).docx
-
Standard – Vulnerability Management (Template).docx
-
Standard – Web Application Protection (Template).docx
-
Standard – Wireless Network Security (Template).docx
-
Standard – Workstation Security (Template).docx
NCA Compliance
All documents in this Toolkit are developed based on the Saudi Arabia National Cybersecurity Authority (NCA) cybersecurity requirements and controls.
You simply need to download the selected document and insert your organization’s name, logo, and relevant details.