ISO27001 Premium Toolkit
This is the most comprehensive ISO 27001:2022 document toolkit currently available.
The documents are created in Microsoft Office format and are ready to be tailored to your organization’s specific needs. As well as standard format and contents, the ISO 27001 template documents include example text that is clearly highlighted to illustrate the type of information that needs to be given regarding your organization. Full example documents are also included to help you with your implementation.
Written by a CISSP qualified auditor with over 30 years’ experience in Information Security, our toolkit provides years of experience and knowledge in an easy to implement format.
With quality and quantity included, this award-winning toolkit covers everything an organization will need, so you can use it first to become certified to the standard, and then to develop and continually improve your ISMS.
This pack has been created by GovernanceDocs to comply with ISO27001:2022 standard.
What is included with in the ISO 27001:2022 toolkit?
- 119 template documents – including policies, procedures, controls, checklists, tools, presentations and other useful documentation
- Available as an instant download after purchase
120+ Templates
Information Security Management System (ISMS) Documentation pack
A full and comprehensive documentation pack to help clients, consultants and service providers achieve ISO 27001:2022 successfully.
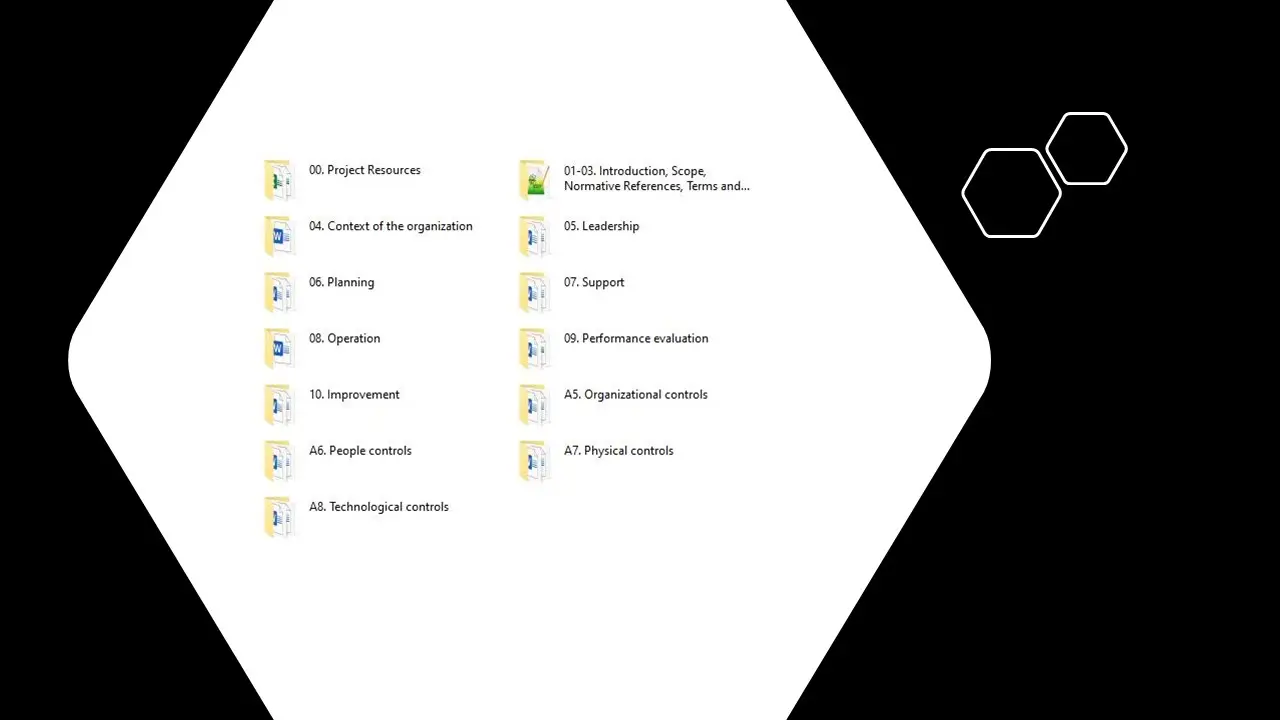
Pack folder structure:
- 0.0 Project Resources (6 Documents)
- 01-03. Introduction, Scope, Normative References, Terms and Definitions
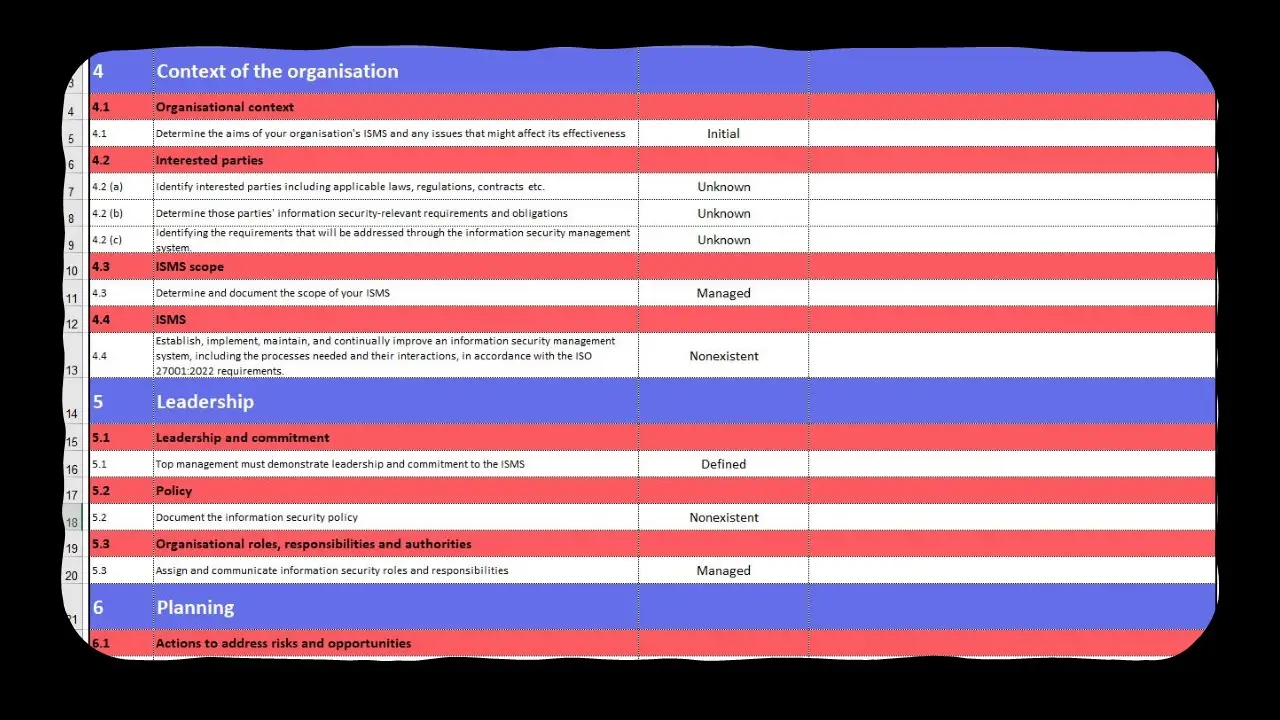
- 04. Context of the organization (1 Document)
- 05. Leadership (5 Documents)
- 06. Planning (4 Documents)
- 07. Support (4 Documents)
- 08. Operation (1 Document)
- 09. Performance evaluation (6 Documents)
- 10. Improvement (3 Documents)
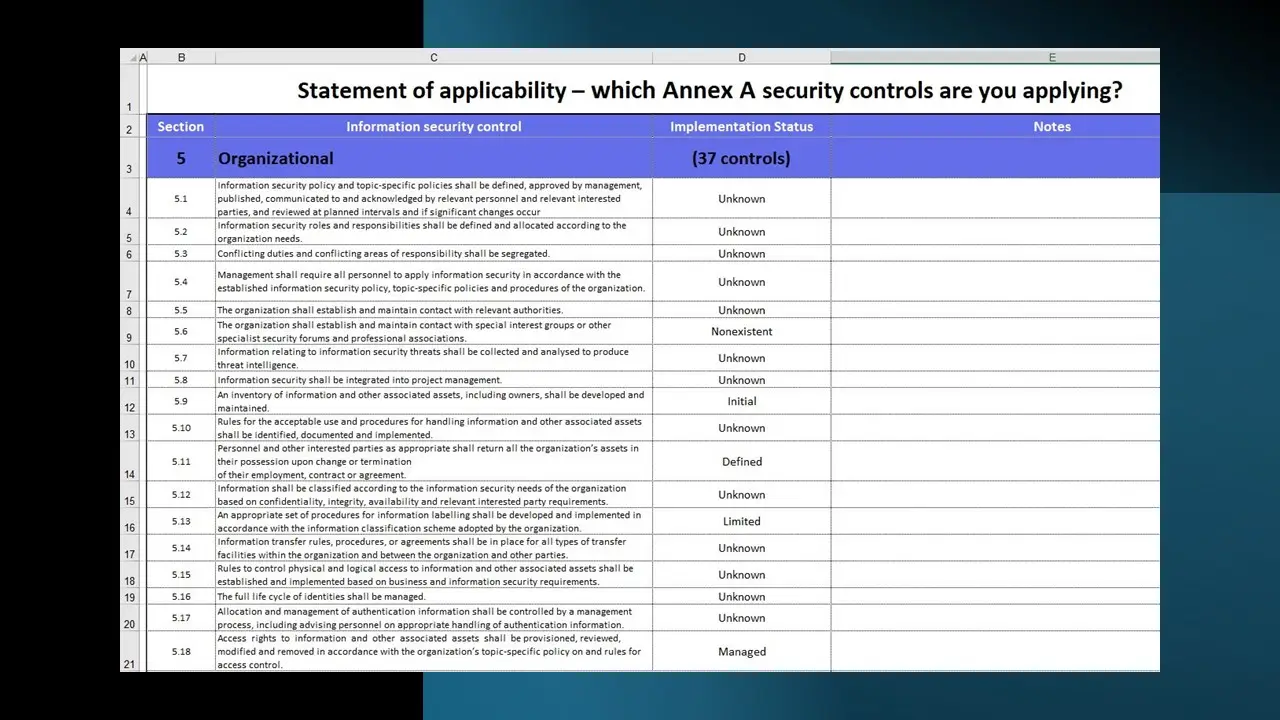
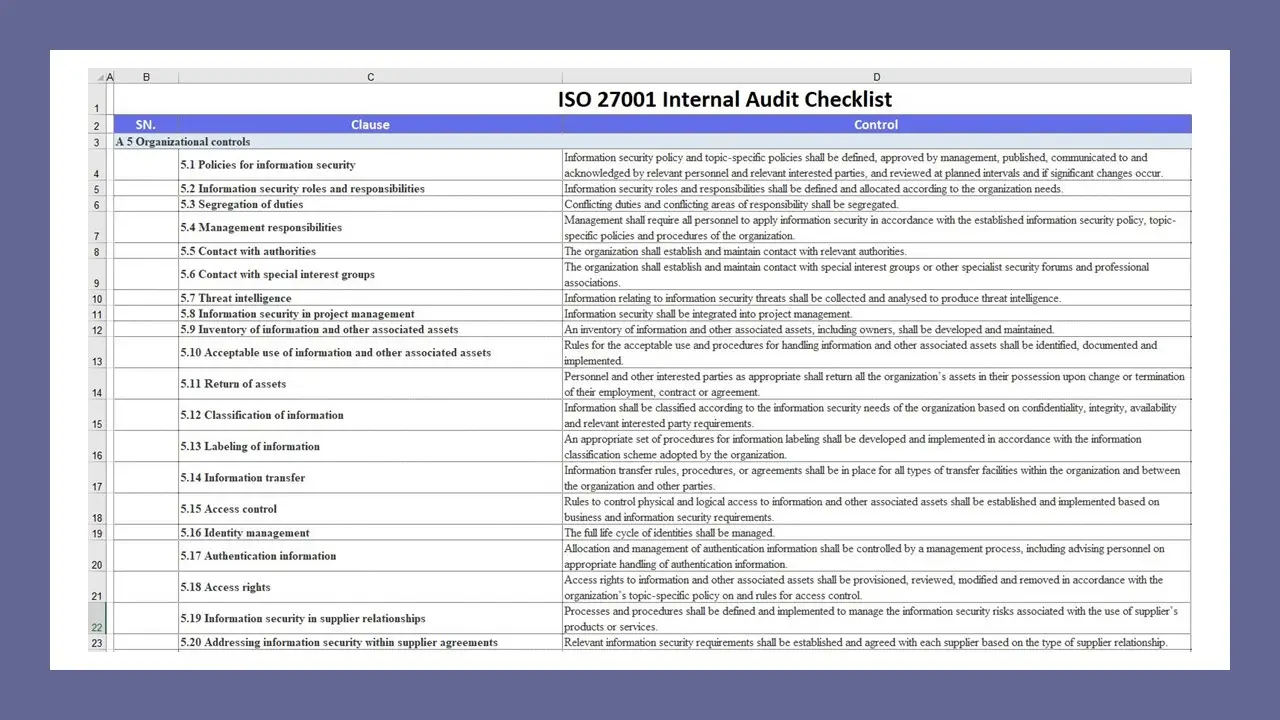
- A5. Organizational controls (33 Documents)
- A6. People controls (11 Documents)
- A7. Physical controls (9 Documents)
- A8. Technological controls (36 Documents)
List of all documents:
- Information Security Management System PID.docx
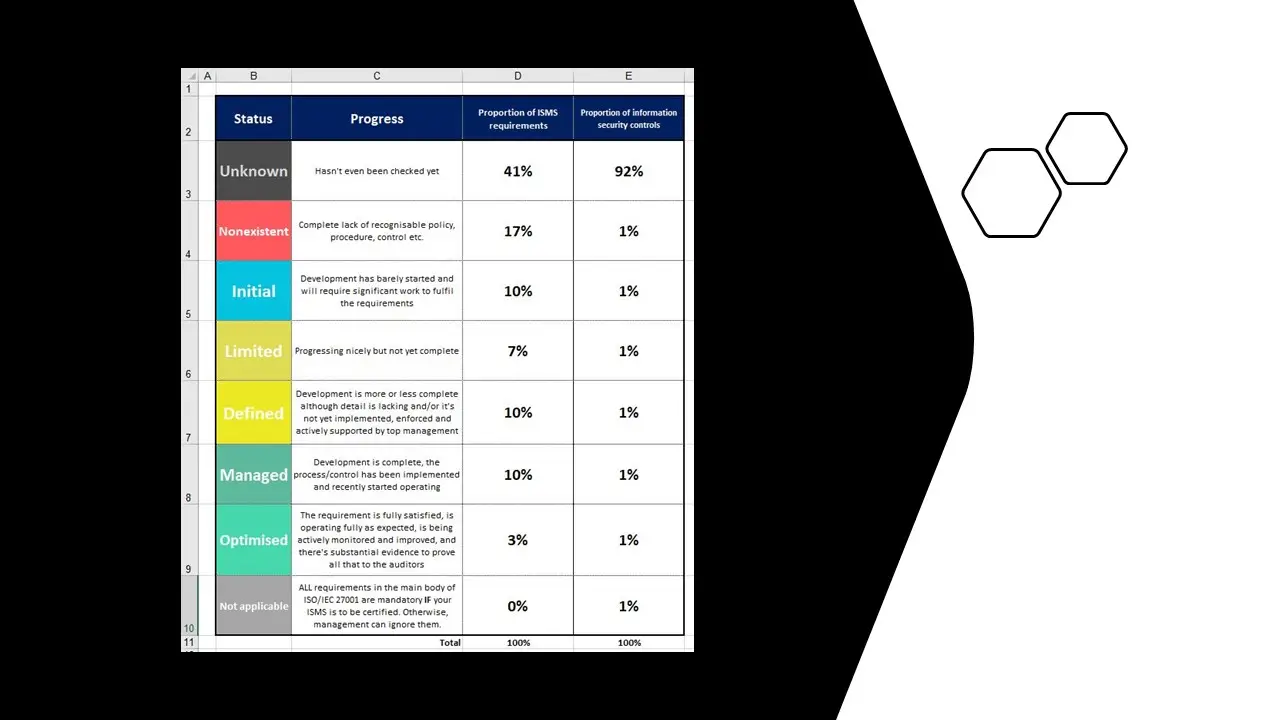
- ISO 27001-2022 Assessment Tool.xlsx
- ISO-IEC 27001 Benefits Presentation.pptx
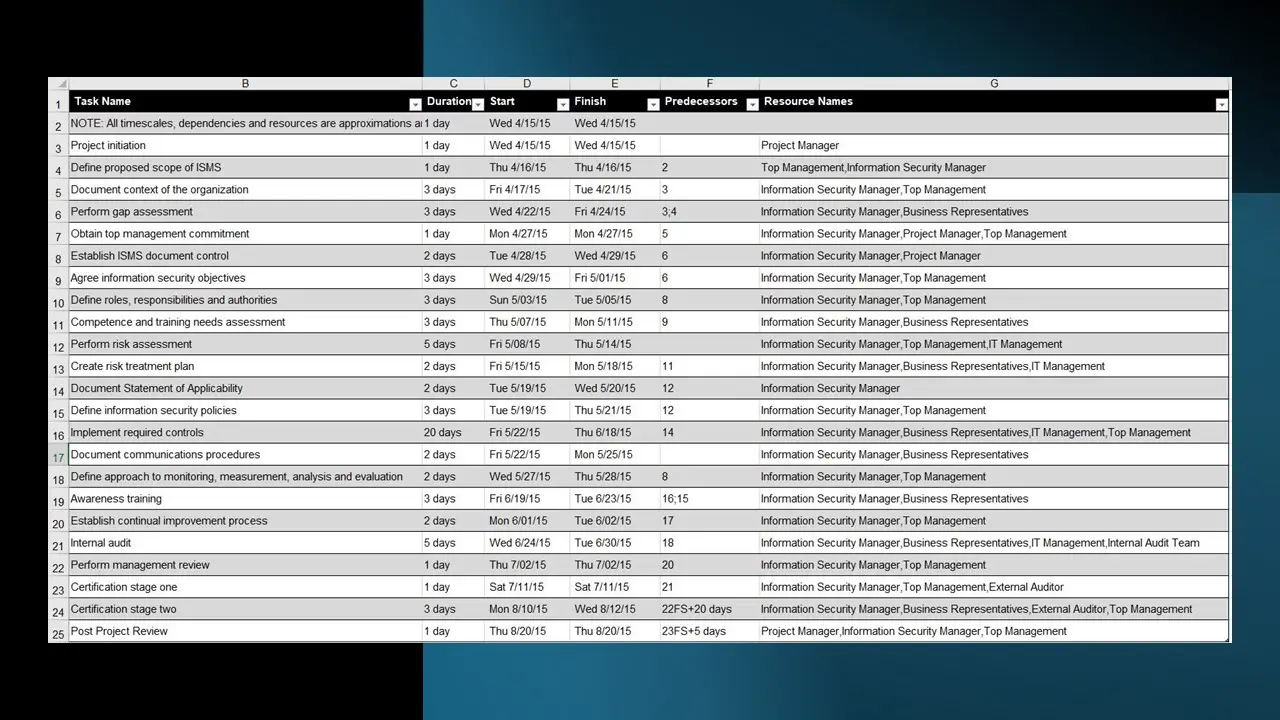
- ISO-IEC 27001 Project Plan.xlsx
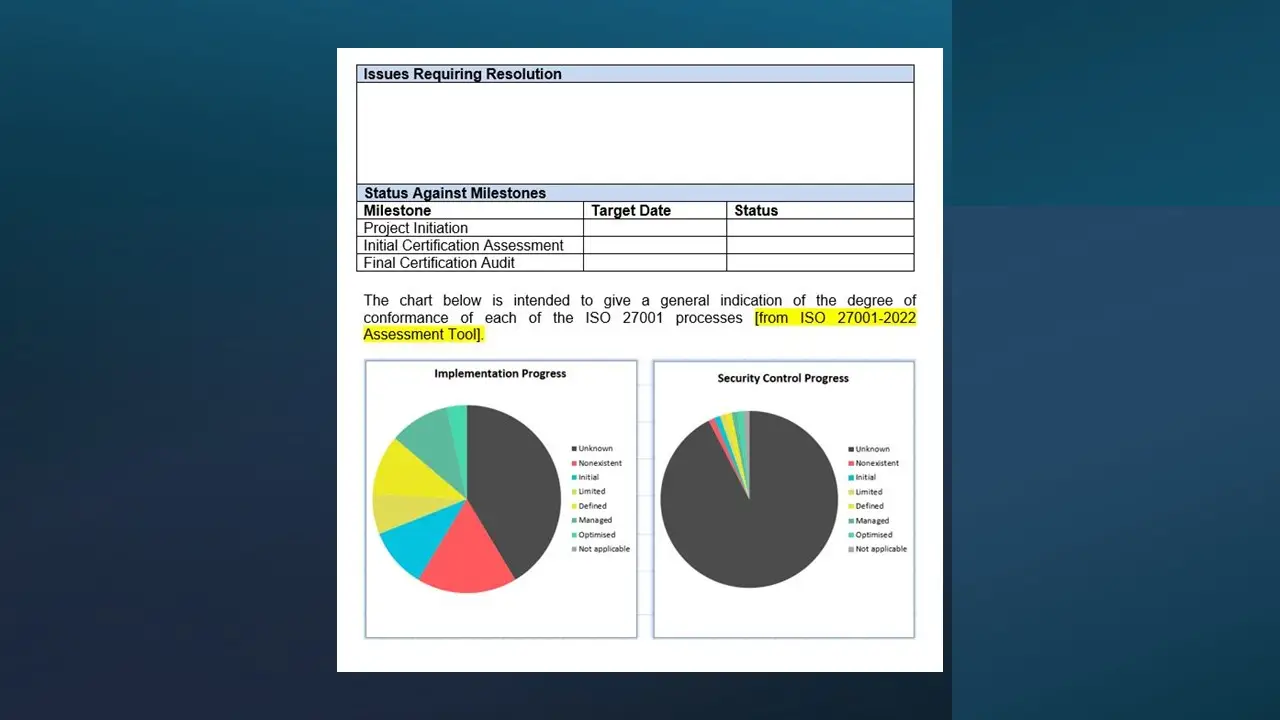
- ISO27001 Highlight Report.docx
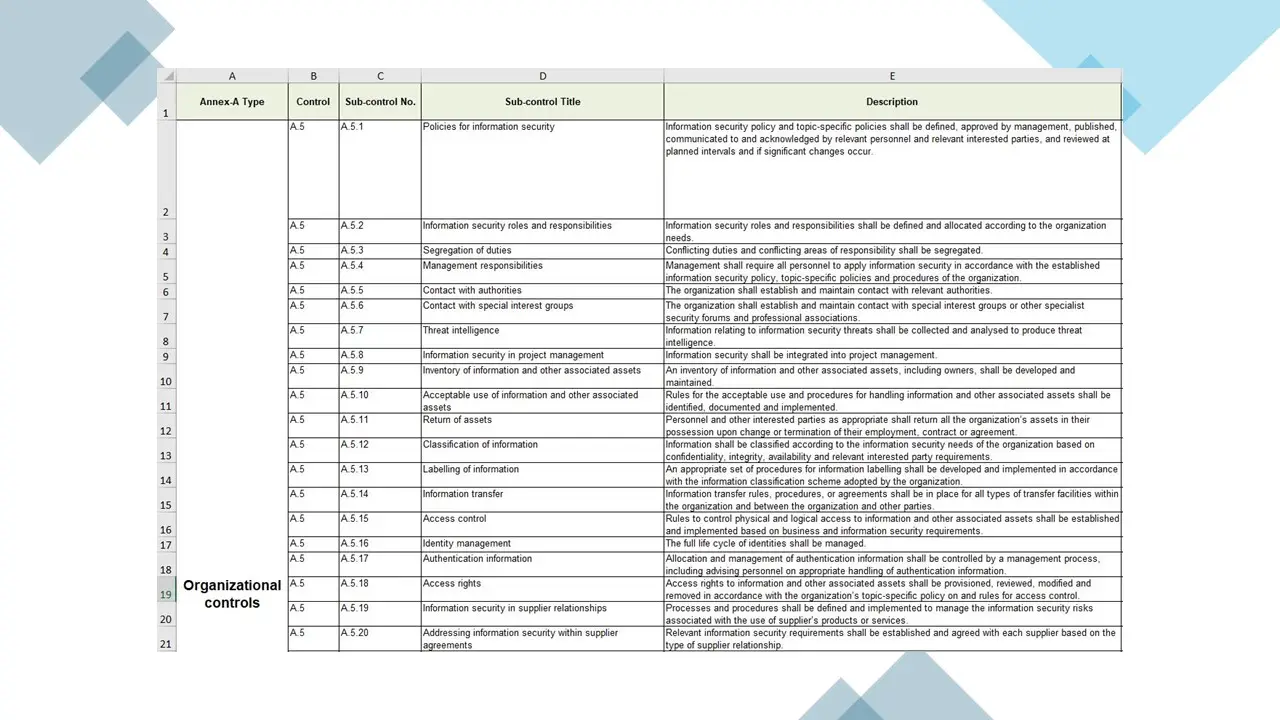
- ISO27001-2022 Statement of Applicability.xlsx
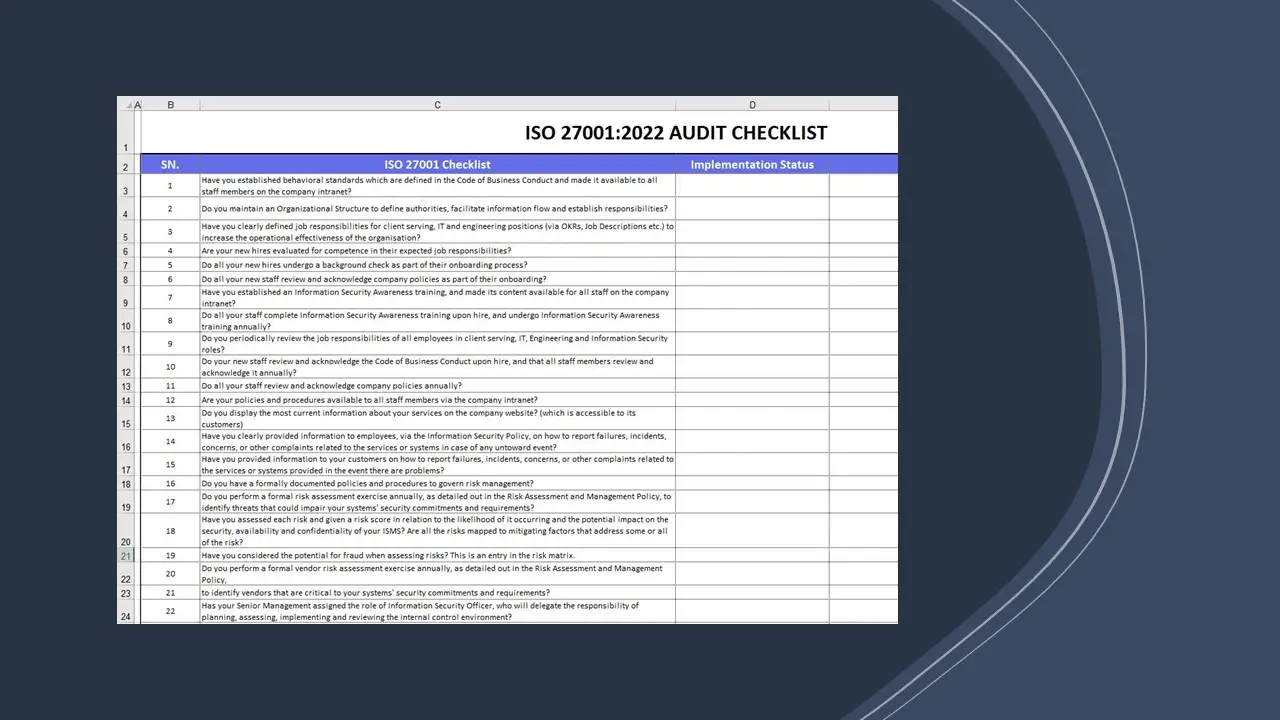
- ISO 27001 Audit Checklist.xlsx
- Information Security Context, Requirements and Scope.docx
- Executive Support Letter.docx
- Information Security Management System Policy.docx
- Information Security Roles Responsibilities and Authorities.docx
- Top Management Communication Programme.docx
- Meeting Minutes Template.docx
- Information Security Management Plan.docx
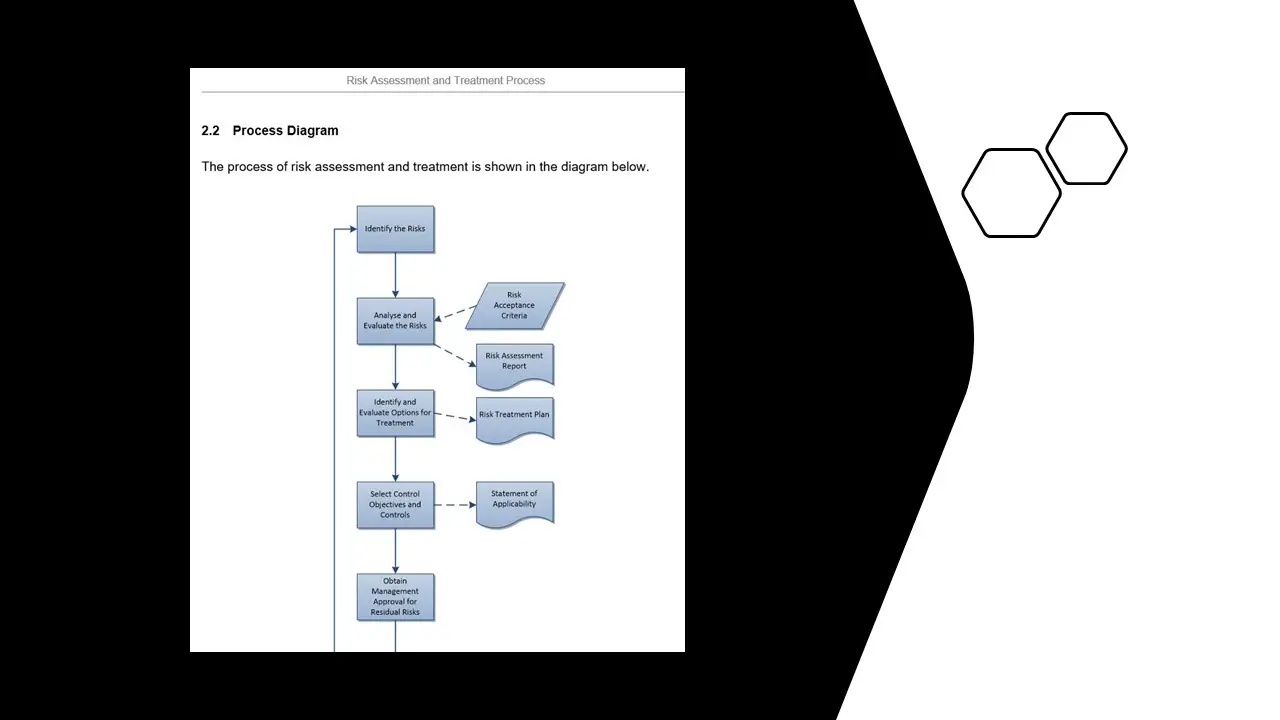
- Risk Assessment and Treatment Process.docx
- Information Security Risk Assessment Report.docx
- Information Security Risk Treatment Plan.docx
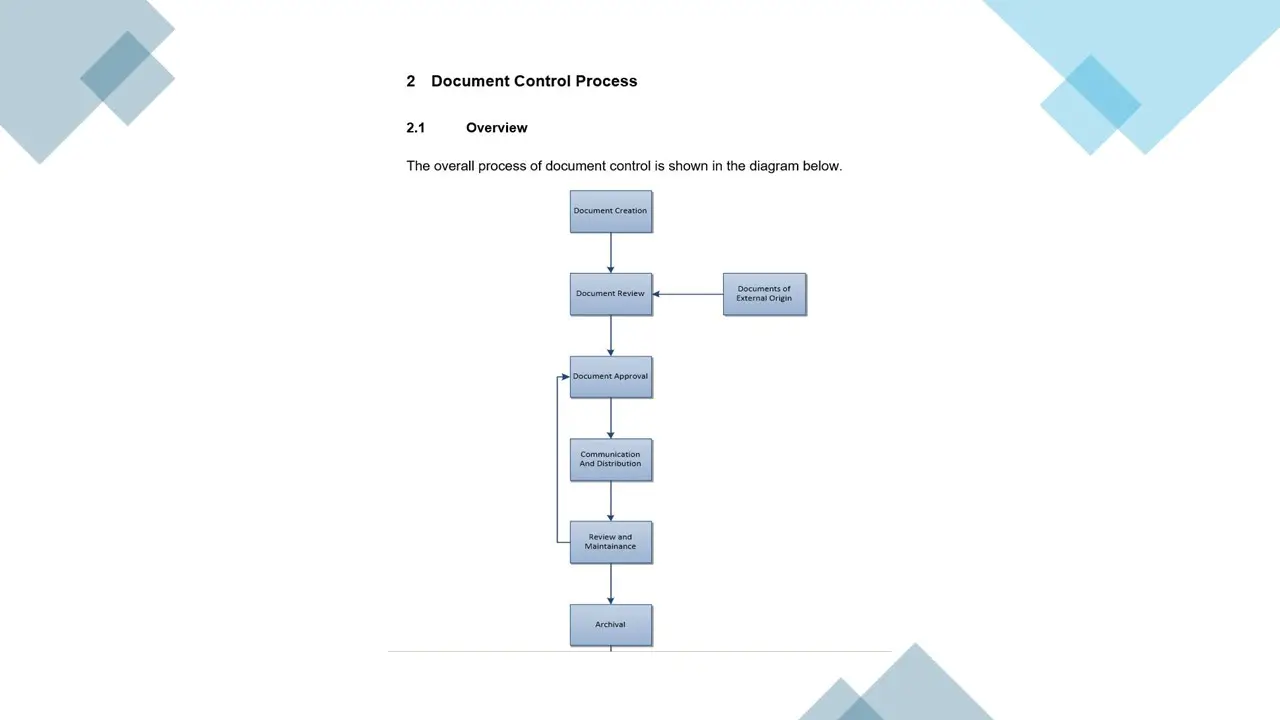
- Procedure for the Control of Documented Information.docx
- Procedure for the Control of Records.docx
- Information Security Communication Plan.docx
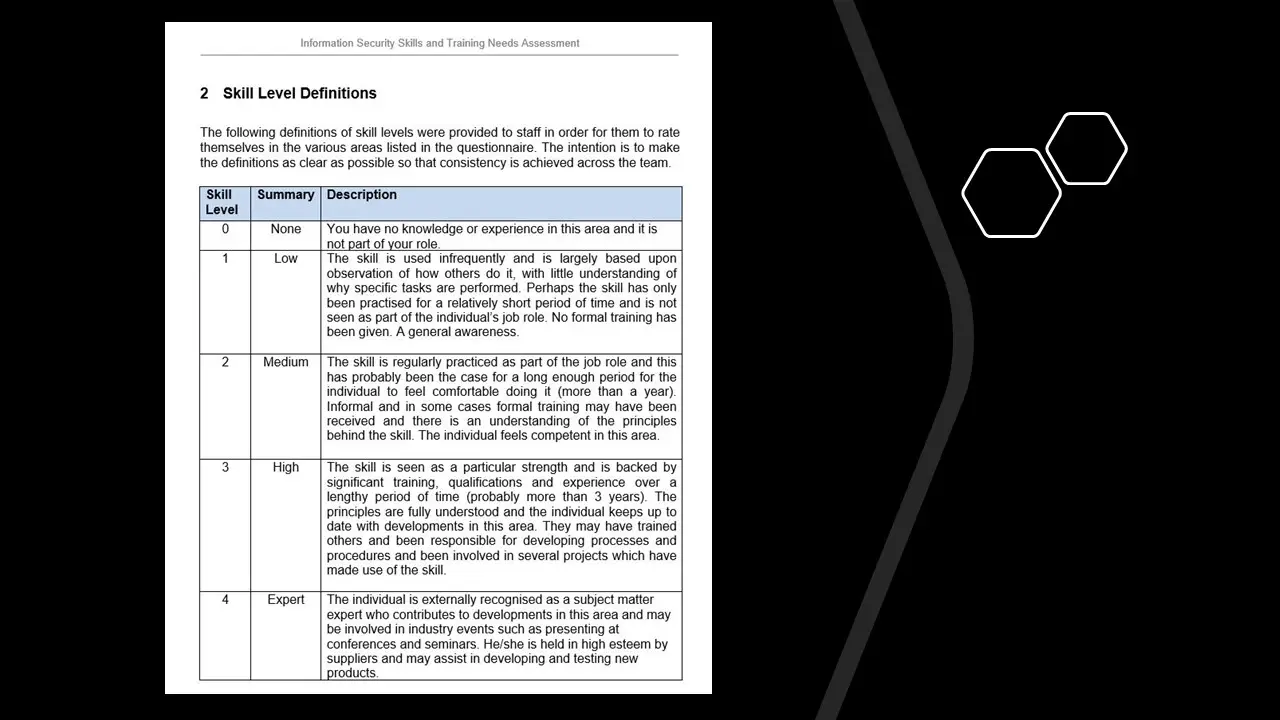
- Information Security Skills and Training Needs Assessment.docx
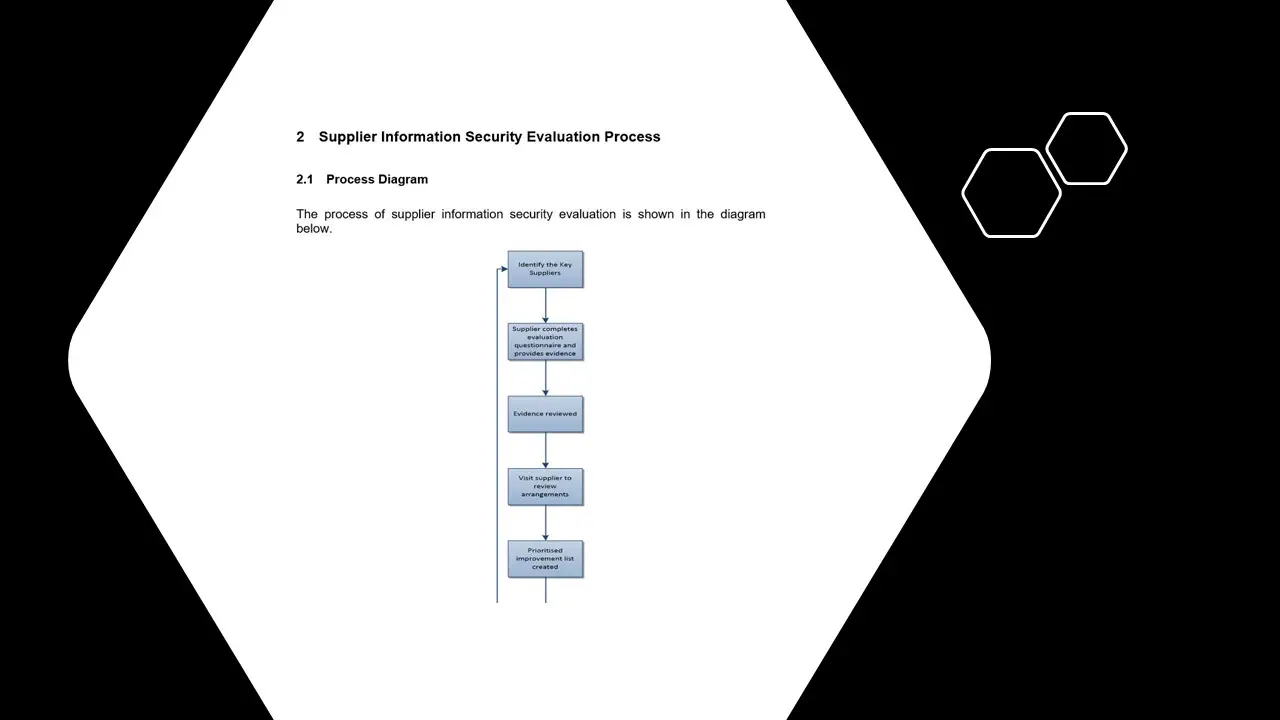
- Supplier Information Security Evaluation Process.docx
- Procedure for Information Security Management System Audits.docx
- Internal Audit Action Plan.docx
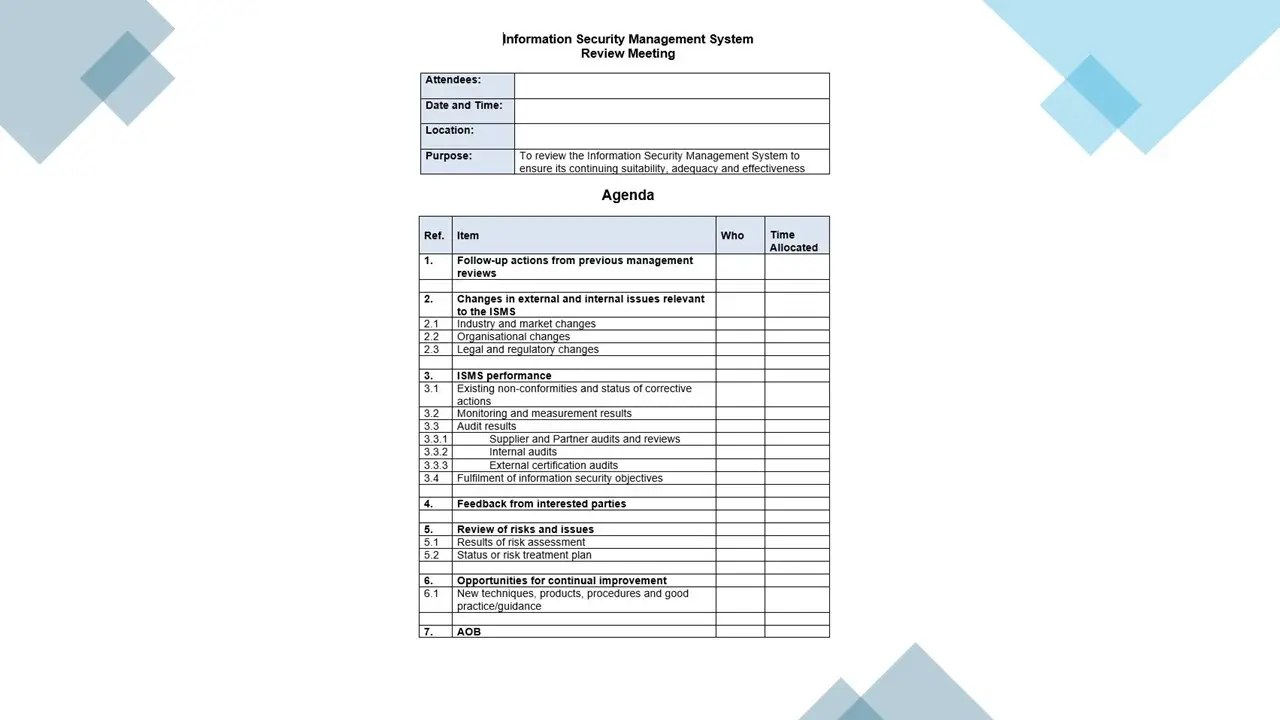
- Information Security Review Meeting Agenda.docx
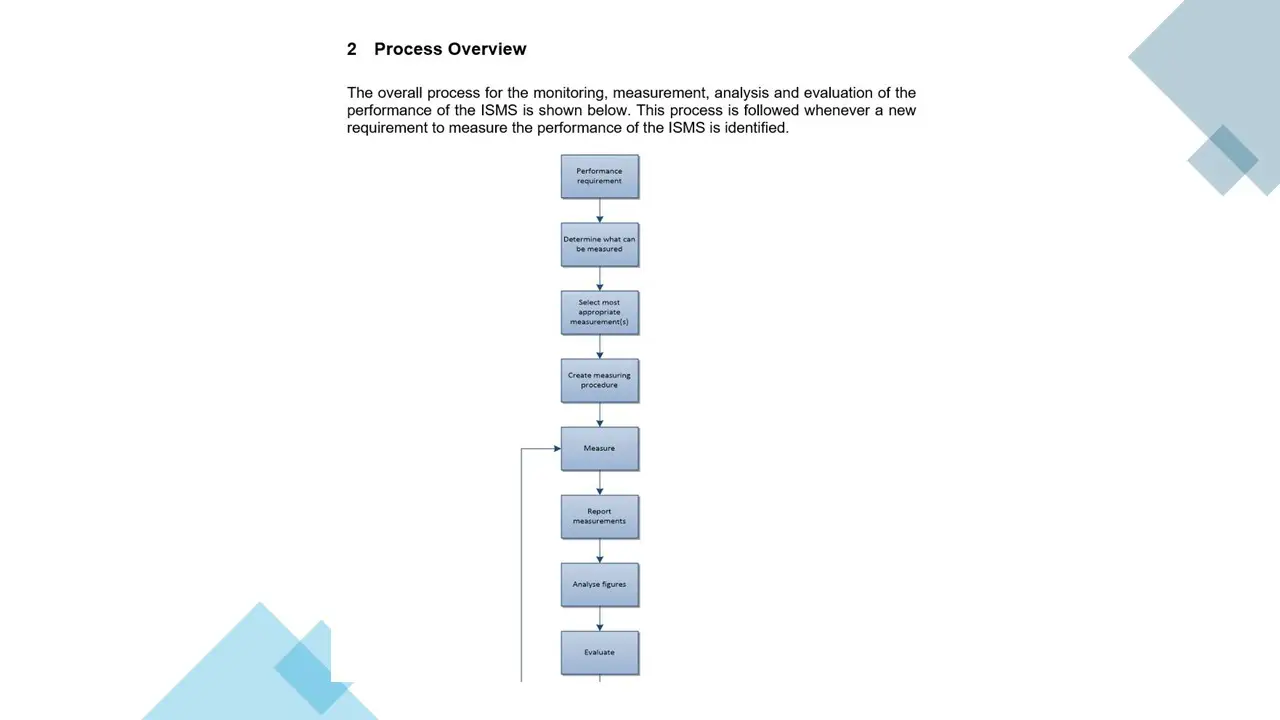
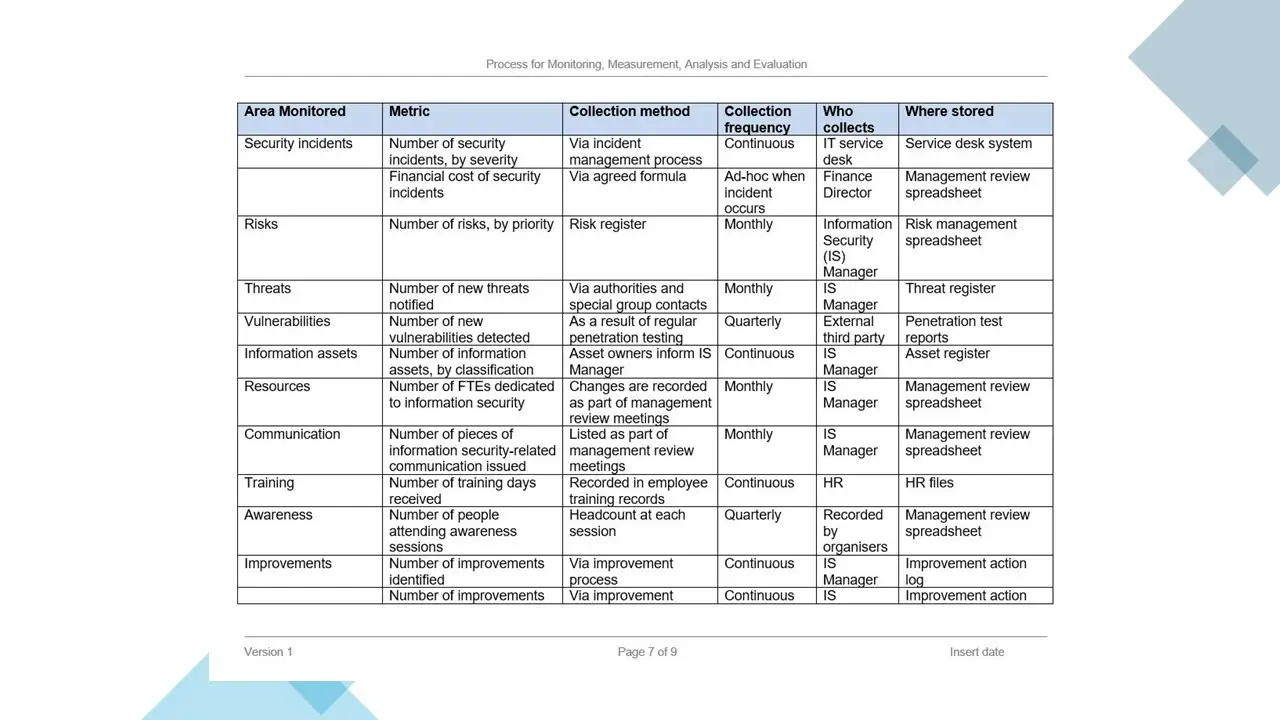
- Process for Monitoring, Measurement, Analysis and Evaluation.docx
- Information Security Management System Audit Plan.docx
- ISMS Audit Programme Schedule.docx
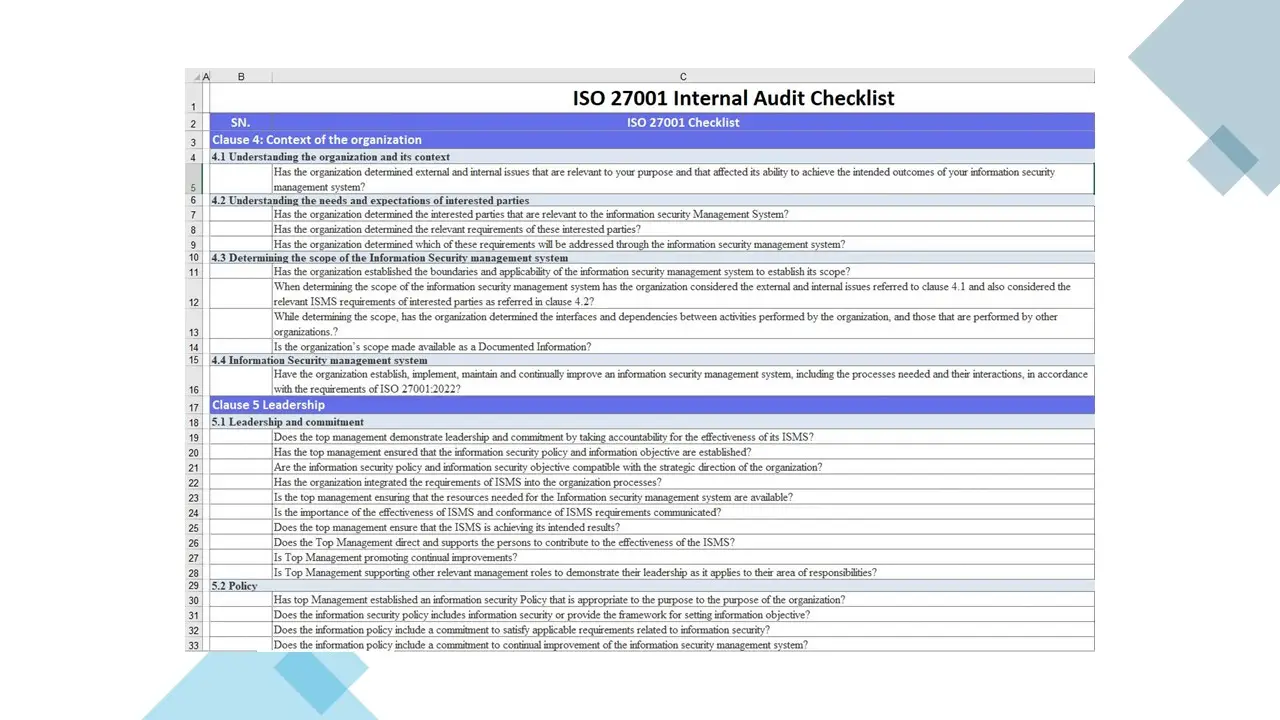
- ISO 27001 Internal Audit Checklist
- Procedure for Continual Improvement.docx
- Procedure for the Management of Nonconformity.docx
- ISMS Continual Improvement Action Log.xlsx
- Information Security Policy.docx
- Information Security Guidelines for Project Management.docx
- Segregation of Duties Guidelines.docx
- Information Security Classification Guidelines.docx
- Information Security Labelling Procedure.docx
- Procedure for the Disposal of Media.docx
- Asset Handling Procedure.docx
- Access Control Policy.docx
- User Access Management Process.docx
- Procedure for Remote Supplier Access to Systems.docx
- Procedure for the Reset of User Passwords.docx
- Operating Procedure.docx
- Information Transfer Agreement.docx
- Information Transfer Procedure.docx
- Network Services Agreement.docx
- Supplier Management Policy.docx
- Supplier Information Security Agreement.docx
- Information Security Incident Management Procedure.docx
- Incident Management Process.docx
- Major Incident Management Process.docx
- Business Continuity Exercising and Testing Schedule.docx
- Business Continuity Plan.docx
- Business Continuity Test Plan.docx
- Business Continuity Test Report.docx
- Business Impact Analysis Process.docx
- Incident Response Procedure.docx
- Post Incident Report Template.docx
- Legal Responsibilities Policy.docx
- Legal and Regulatory Requirements Procedure.docx
- IP and Copyright Compliance Policy.docx
- Records Retention and Protection Policy.docx
- Threat Intelligence Policy.docx
- Information Security Policy for the use of Cloud Service.docx
- Remote Working Policy.docx
- AUP and Personal Commitment Statement.docx
- Email Policy.docx
- Internet Acceptable Use Policy.docx
- Employee Termination and Change of Employment Checklist.docx
- Employee Recruitment and New Starter Checklist.docx
- Employee Screening Checklist.docx
- Guidelines for Inclusion in Employment Contracts.docx
- Employee Disciplinary Process.docx
- Non-Disclosure Agreement.docx
- Leavers Letter.docx
- Procedure for the Management of Removable Media.docx
- Removable Media Assessment Guidelines.docx
- Physical Media Transfer Procedure.docx
- Configuration Management Process.docx
- Configuration Management Procedure.docx
- Guidelines for Working in Secure Areas.docx
- Physical Security Design Standards.docx
- Procedure for Taking Assets Offsite.docx
- Physical Security Policy.docx
- Change Request Form.docx
- Mobile Computing Policy.docx
- Bring Your Own Device Policy.docx
- Cryptographic Policy.docx
- Backup Policy.docx
- Procedure for Monitoring the Use of IT Systems.docx
- Capacity Management Process.docx
- Change Management Policy.docx
- Change Management Process.docx
- Service Level Agreement.docx
- Capacity Plan.docx
- Software Policy.docx
- Anti-Malware Policy.docx
- Release and Deployment Management Policy.docx
- Release and Deployment Management Process.docx
- Release and Deployment Plan.docx
- Technical Vulnerability Management Policy.docx
- Information Systems Audit Plan.docx
- Technical Vulnerability Assessment Procedure.docx
- Network Security Policy.docx
- Design and Transition of New or Changed Services Process.docx
- Business Requirements Specification.docx
- Project Initiation Document.docx
- Project Highlight Report.docx
- Project Post Implementation Review.docx
- Service Acceptance Checklist.docx
- Secure Development Policy.docx
- Secure Development Environment Guidelines.docx
- Principles for Engineering Secure Systems.docx
- Availability Management Plan.docx
- Secure Informtion Deletion Policy.docx
- Data Masking Policy.docx
- Data Leakage Prevention Policy.docx
- Event Logging and Monitoring Policy.docx
- Safe Browsing and Web Filtering Policy.docx
- Secure Coding Policy.docx
All GovernanaceDocs documents are developed based on well-known standards such as NIST CSF, ISO 27001, ISO 22301, PCI-DSS and HIPAA.
Hence, You just need to download and selected document and add your company name and logo.


















































John Doe –
The ISO 27001:2022 Premium Documentation Toolkit was a game-changer for our organization. It provided all the necessary documents and templates, which saved us countless hours of work. Achieving ISO 27001 certification was much smoother thanks to this comprehensive toolkit.
Jane Smith –
This toolkit is a must-have for anyone serious about ISO 27001 certification. The documentation was clear, detailed, and easy to customize for our needs. Highly recommended!
Alice Brown –
I was overwhelmed by the ISO 27001 requirements until I found this toolkit. It made the whole process manageable and less stressful. Great value for the price!
Bob Johnson –
The ISO 27001:2022 Premium Documentation Toolkit is very thorough. We particularly appreciated the step-by-step guidance and the quality of the templates provided. A bit pricey, but worth every penny.
Chris Lee –
Absolutely fantastic resource! The toolkit included everything we needed to get our ISO 27001 certification. The support team was also very responsive and helpful.
Dana White –
This toolkit provided a solid foundation for our ISO 27001 certification efforts. The templates were easy to use and adapt. Highly recommended for organizations of any size.
Edward Green –
The ISO 27001:2022 Premium Documentation Toolkit exceeded our expectations. It was incredibly detailed and covered all aspects of the certification process. We couldn’t have done it without this product.
Fiona Black –
As a small business, we found the toolkit invaluable. It saved us significant time and effort, making the ISO 27001 certification process much simpler and more straightforward.
George King –
The toolkit was very comprehensive and provided everything we needed to meet ISO 27001 standards. The templates were easy to modify, and the guidance notes were extremely helpful.
Helen Scott –
This documentation toolkit is a lifesaver! It made the complex process of ISO 27001 certification much more manageable. The documents are professional and easy to follow.
Ian Wright –
We achieved our ISO 27001 certification thanks to this toolkit. The documentation was comprehensive and well-structured, making it easy for our team to implement the necessary measures.
Jenny Hill –
The ISO 27001:2022 Premium Documentation Toolkit was instrumental in our certification process. The templates and guidelines provided were top-notch. Highly recommended!
Kevin Martin –
Very pleased with this product. It provided clear and concise documentation that made our ISO 27001 certification journey much easier. A bit expensive, but worth it for the peace of mind.
Laura Adams –
An excellent resource for any organization aiming for ISO 27001 certification. The toolkit was detailed, easy to use, and saved us a lot of time and effort.
Mark Davis –
This toolkit was exactly what we needed. It covered all the bases and provided comprehensive documentation that was easy to understand and implement. We highly recommend it!
Nancy Wilson –
The ISO 27001:2022 Premium Documentation Toolkit provided a clear roadmap for our certification process. The templates were easy to customize and very thorough.
Oliver Harris –
Achieving ISO 27001 certification was much easier with this toolkit. The documentation was very detailed, and the templates were a huge time-saver. Highly recommend!
Patricia Baker –
The toolkit was incredibly helpful in our ISO 27001 certification journey. The templates and guidance notes were very detailed and easy to follow. Great value for money!
Quentin Young –
This product provided everything we needed to comply with ISO 27001 standards. The templates were easy to adapt, and the guidance was clear and comprehensive.
Rachel Campbell –
We successfully achieved ISO 27001 certification thanks to the ISO 27001:2022 Premium Documentation Toolkit. It provided us with all the necessary documentation and support to make the process smooth and efficient.
NoahSmith –
These document templates are worth every penny. They’re comprehensive and easy to use.
EmmaJohnson –
Exceptional document templates! They’ve made our compliance process so much smoother, and the end results look fantastic. Great job!
EmmaJohnson –
Exceptional document templates! They’ve made our compliance process so much smoother, and the end results look fantastic. Great job!
AvaDavis –
These templates are a game-changer for our organization.
HarperBrown –
We can’t thank the creators enough for these templates. They’ve streamlined our document creation process, and the end results look fantastic. Great job!
HarperClark –
These templates are a true gem. Well-structured and easy to use. They cover all the necessary details and have made our lives easier.
LiamMiller –
I couldn’t be happier with these document templates. They’ve made a significant difference in our efficiency and document quality.