Product Description
This ISO 27001 Toolkit is the most comprehensive resource currently available for implementing an Information Security Management System (ISMS) in accordance with the standard.
Developed in Microsoft Office format, the documents are fully customizable to address your organization’s unique requirements. Each template is structured with standard content and includes clearly highlighted example text to guide users in providing the necessary organization-specific details. Additionally, full example documents are included to support a smooth and effective implementation process.
This toolkit not only simplifies your ISO 27001 implementation but also serves as a vital resource for awareness and training in cybersecurity best practices. Designed for business leaders, compliance professionals, and expert GDPR consultants, it provides structured guidance to streamline your journey toward certification. Whether you’re seeking to establish a solid ISMS foundation or enhance existing controls, this toolkit ensures you have the right toolkits and support for a seamless compliance process. Enhance Your ISO 27001 Implementation with Expert Support and Training.
ISMS Toolkit Author
Authored by a CISSP-certified auditor with over 20 years of experience in Information Security, this ISO 27001 toolkit encapsulates decades of expertise and practical knowledge in a user-friendly, ready-to-use format.
This ISO 27001 complete ISMS Toolkit combines quality and completeness. It provides all the essential documentation required to achieve ISO 27001 certification. It serves as a robust foundation for certification and supports the continuous development and improvement of your ISMS.
Governance Docs have created this pack to comply with ISO IEC 27001:2022 standard and ISO 27002:2022
What is included in the toolkit?
- 175 ISO 27001 Documentation Templates – including policies, procedures, controls, checklists, tools, presentations, and other helpful documentation
- Available as an instant download after purchase
175 ISO 27001 Document Templates
Information Security Management System (ISMS) Documentation pack
A complete and comprehensive documentation package designed to assist clients, consultants, and service providers in successfully achieving compliance with ISO 27001:2022.
List of ISMS Documentation Toolkit:
-
Acceptable Use Policy.docx
-
Access Control Policy.docx
-
Anti-Malware Policy.docx
-
Asset Handling Policy.docx
-
Asset Inventory.xlsm
-
Asset Register.xlsx
-
Awareness Presentation.pptx
-
Backup Policy.docx
-
BCP Test Report.docx
-
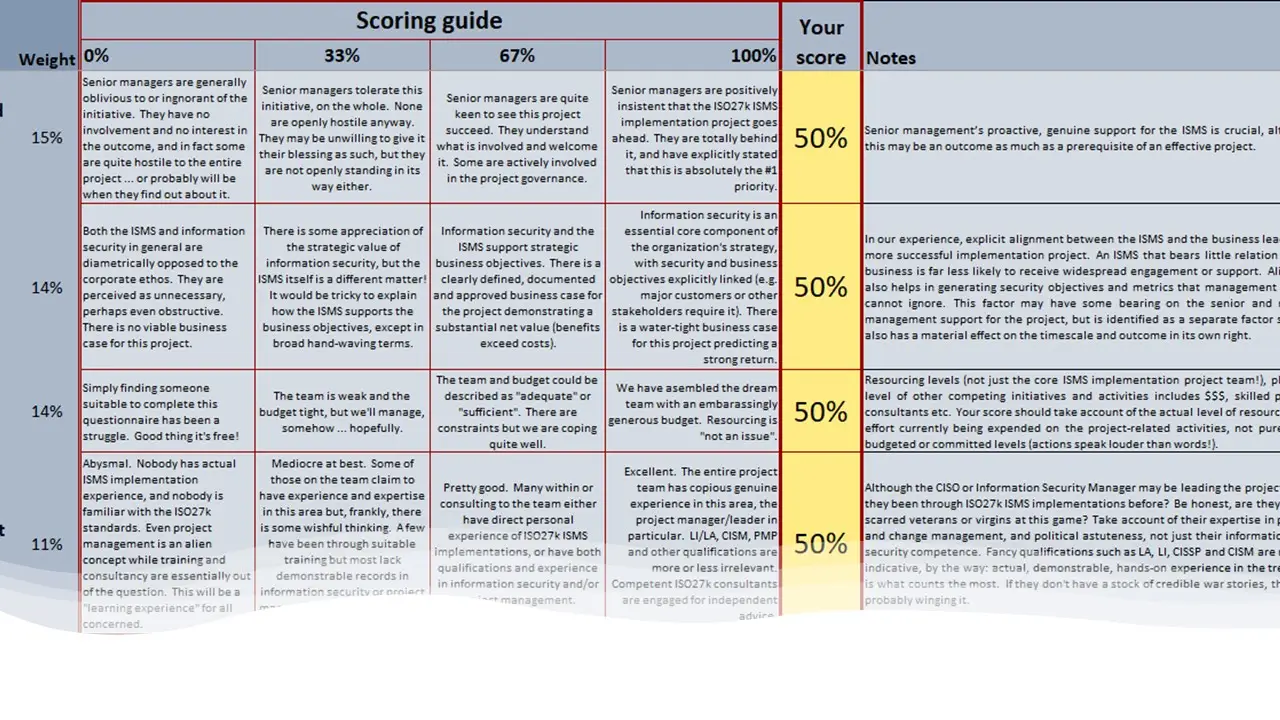
Business Case Template for ISO/IEC 27001 ISMS.docx
-
Business Continuity Manager JD.docx
-
Business Continuity Plan.docx
-
Business Continuity Test Plan.docx
-
Business Requirements Specification Procedure.docx
-
Business Value of ISO27001 Case Study.docx
-
BYOD Policy.docx
-
BYOD Security Manager JD.docx
-
Change Management Policy.docx
-
Chief Information Security Officer JD.docx
-
Cloud Services Security Policy.docx
-
Compliance Manager JD.docx
-
Configuration Management Procedure.docx
-
Continuous Improvement Procedure.docx
-
Control of Records Procedure.docx
-
Copyright Compliance Policy.docx
-
Corrective Action Procedure.docx
-
Counter-Espionage Manager JD.docx
-
Cryptographic Policy.docx
-
Data Masking Policy.docx
-
Data Restoration Form.docx
-
Data Retention Policy.docx
-
Database Security Manager JD.docx
-
Development Environment Policy.docx
-
Data Loss Prevention (DLP) Policy.docx
-
Documented Information Control Procedure.docx
-
Email Usage Policy.docx
-
Employee Disciplinary Process.docx
-
Employee Movement and Termination Checklist.docx
-
Employee Screening Checklist.docx
-
Employment Contract Clauses.docx
-
FMEA Spreadsheet.xlsx
-
Fraud Manager JD.docx
-
Guideline on Information Asset Valuation.docx
-
Incident Response Procedure.docx
-
Industrial Information Risk and Security Manager JD.docx
-
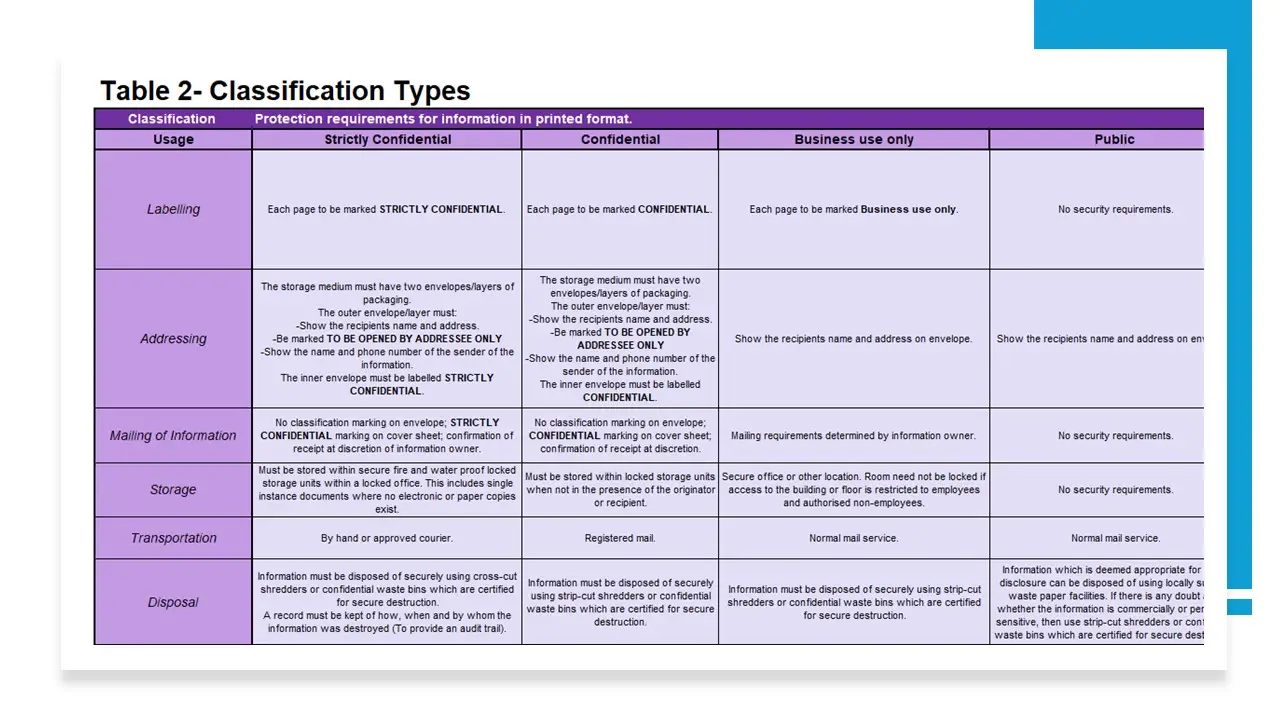
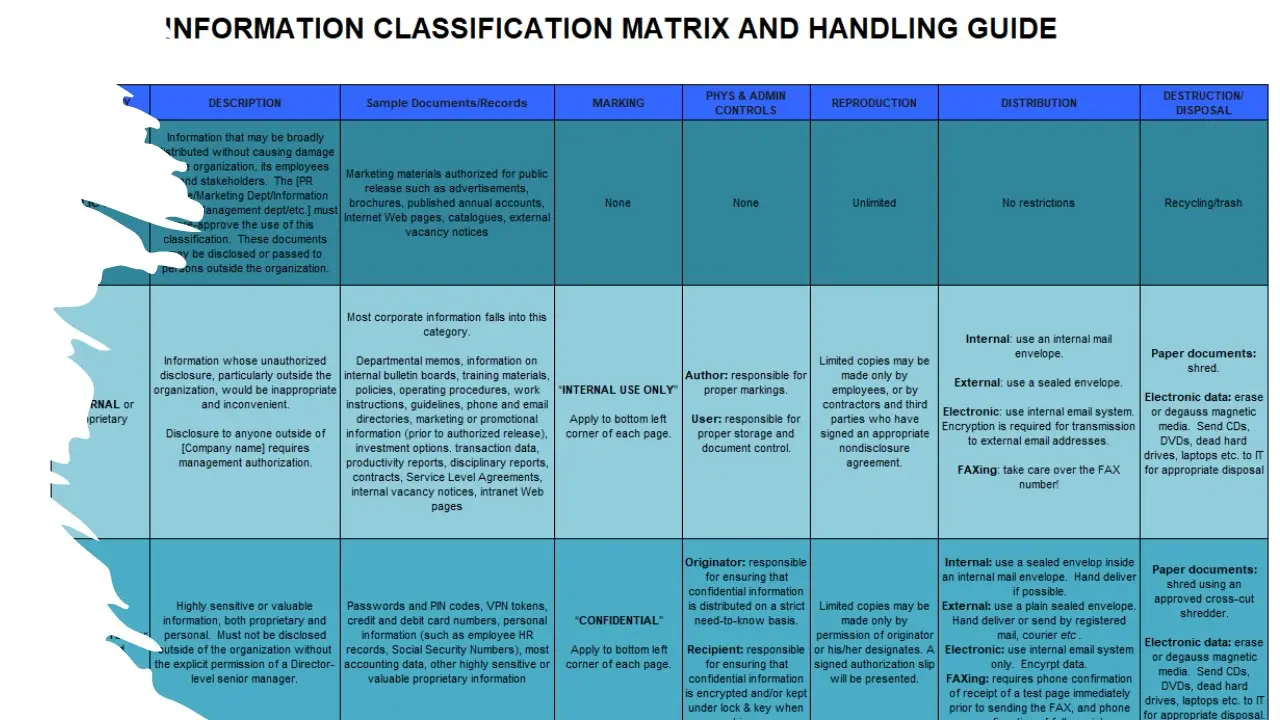
Information Classification Matrix.xlsx
-
Information Risk and Security Manager JD.docx
-
Information Security Classification Policy.docx
-
Information Security Incident Manager JD.docx
-
Information Security Labelling Procedure.docx
-
Information Security Policy.docx
-
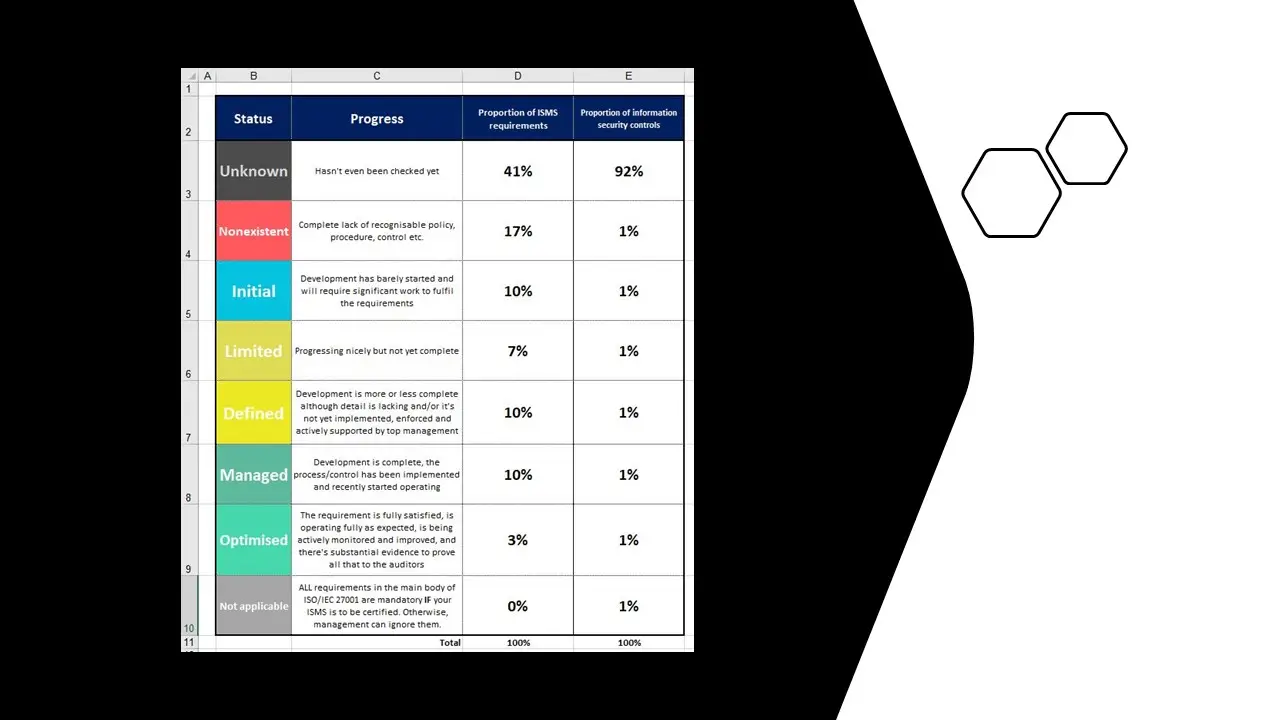
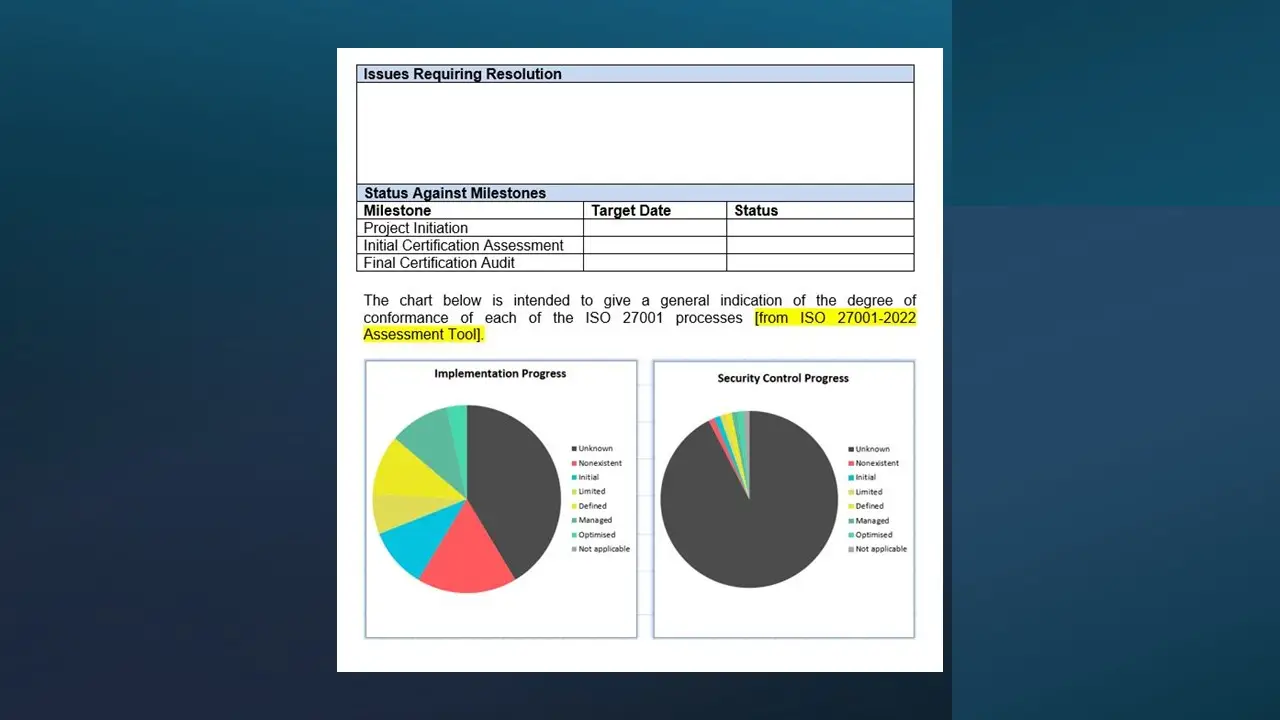
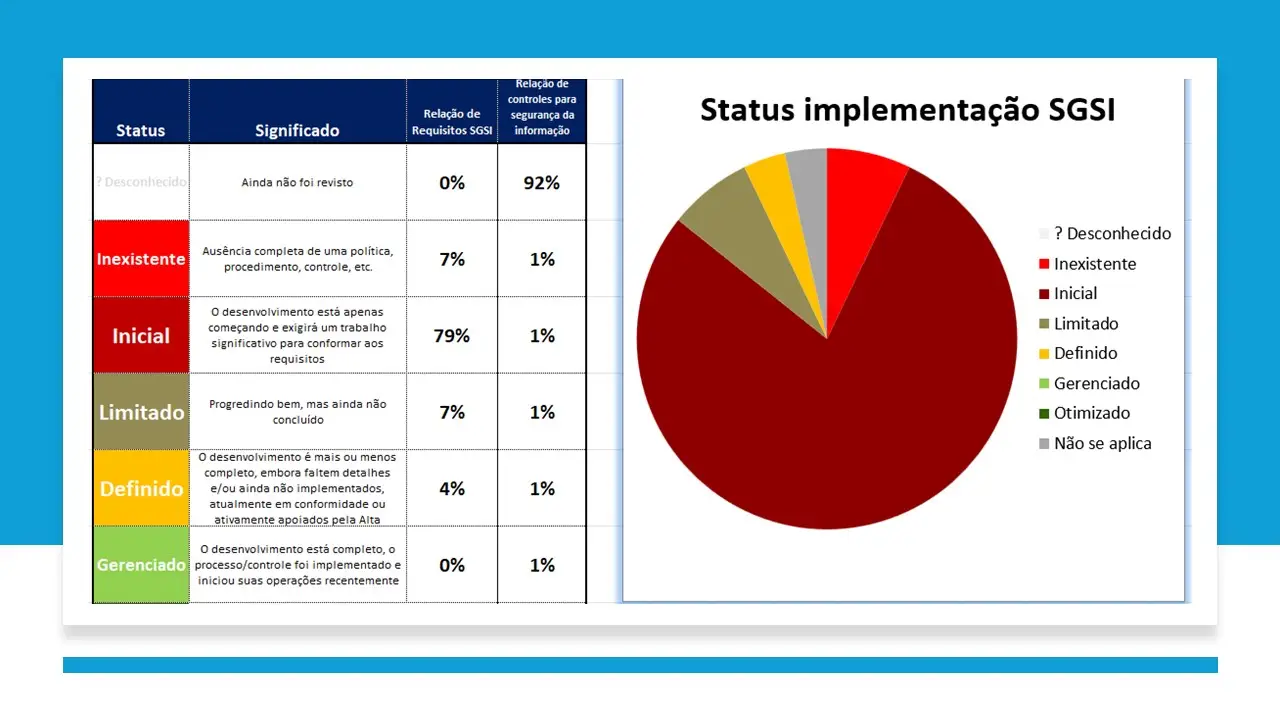
Information Security Program Maturity Assessment Tool.xlsx
-
Information Transfer Procedure.docx
-
Intellectual Property Manager JD.docx
-
Internet Acceptable Use Policy.docx
-
Internet Risk and Security Manager JD.docx
-
Intro and Gap Analysis Email Template.txt
-
IoT and BYOD Security Manager JD.docx
-
ISMS Organization Chart Data.xlsx
-
ISMS Audit Plan.docx
-
ISMS Audit Schedule.docx
-
ISMS Auditing Guideline.docx
-
ISMS Audits Procedure.docx
-
ISMS Business Impact Analysis (BIA) Procedure.docx
-
ISMS Communication Plan.docx
-
ISMS Context and Scope.docx
-
ISMS Continuous Improvement Log.xlsx
-
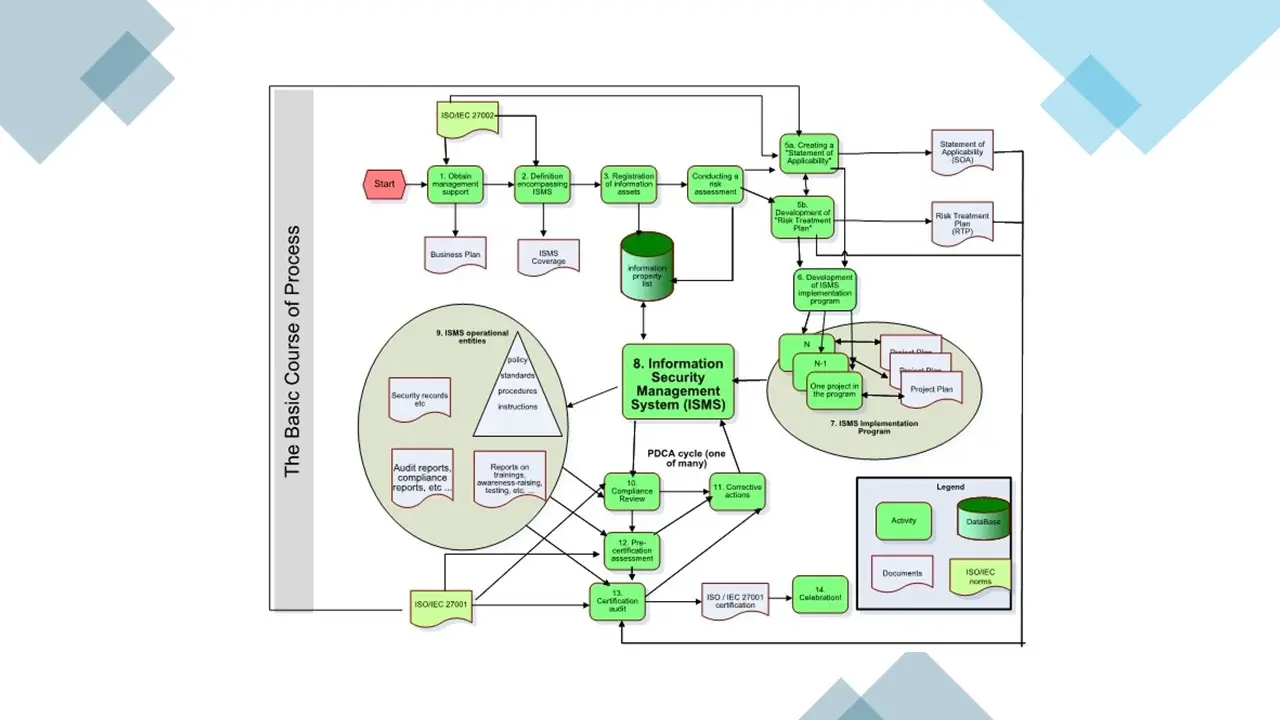
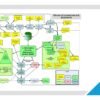
ISMS Implementation and Certification – Basic Process (Croatian).png
-
ISMS Implementation and Certification – Basic Process (Italian).png
-
ISMS Implementation and Certification – Basic Process (Polish).png
-
ISMS Implementation and Certification – Basic Process (Spanish).png
-
ISMS Implementation and Certification – Detailed Process (Croatian).png
-
ISMS Implementation and Certification – Detailed Process (Italian).png
-
ISMS Implementation and Certification – Detailed Process (Polish).png
-
ISMS Implementation and Certification – Detailed Process (Spanish).png
-
ISMS Implementation and Certification Overview.pptx
-
ISMS Implementation and Certification – Basic Process 4v1.jpg
-
ISMS Implementation and Certification Process 4v1 (French).vsdx
-
ISMS Implementation and Certification Process 4v1 (German).vsdx
-
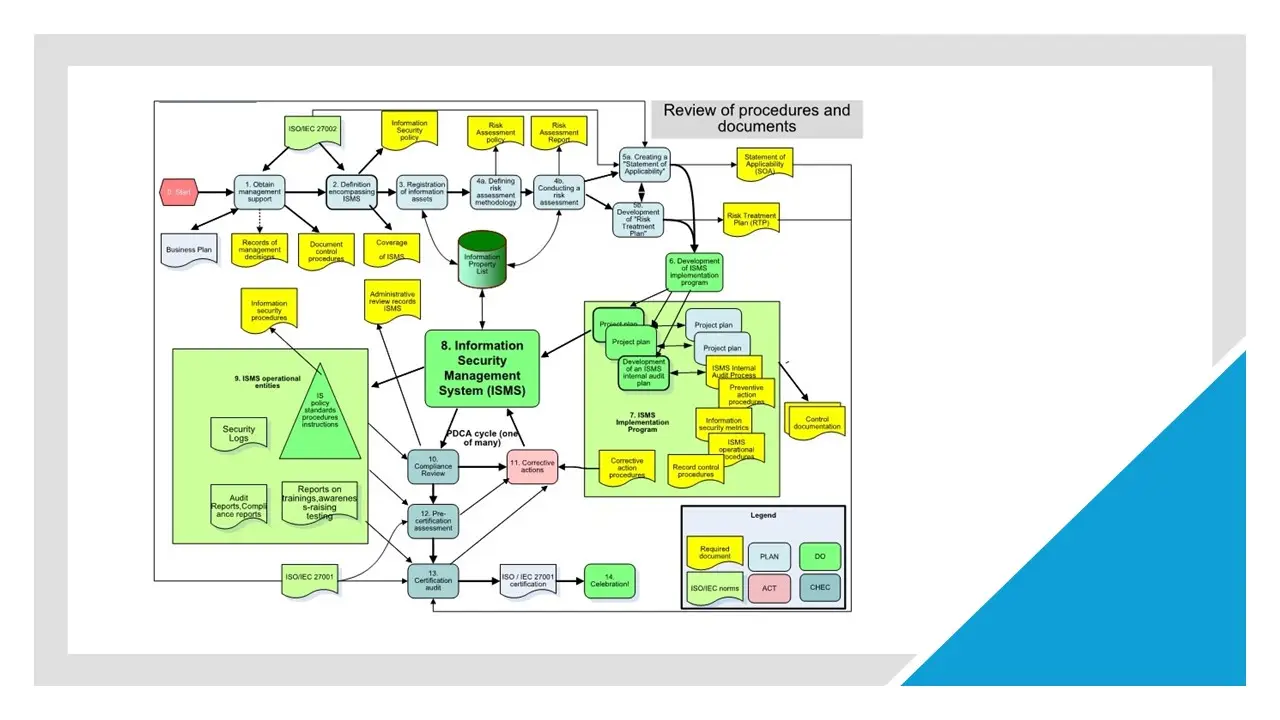
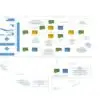
ISMS Implementation and Certification Process 4v1 – Procedures and Documents.jpg
-
ISMS Implementation and Certification Process 4v1.vsdx
-
ISMS Implementation and Certification Process v3.vsdx
-
ISMS Implementation Project Estimator.xlsx
-
ISMS Information Asset Inventory.xlsx
-
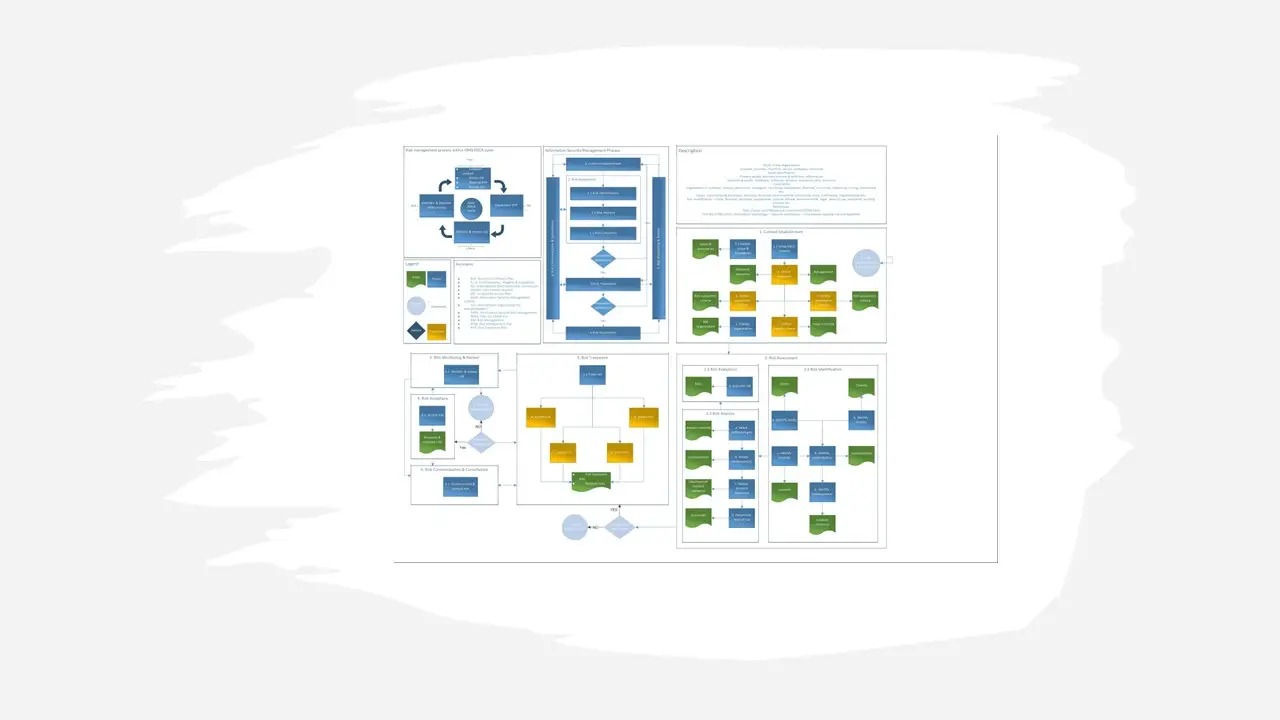
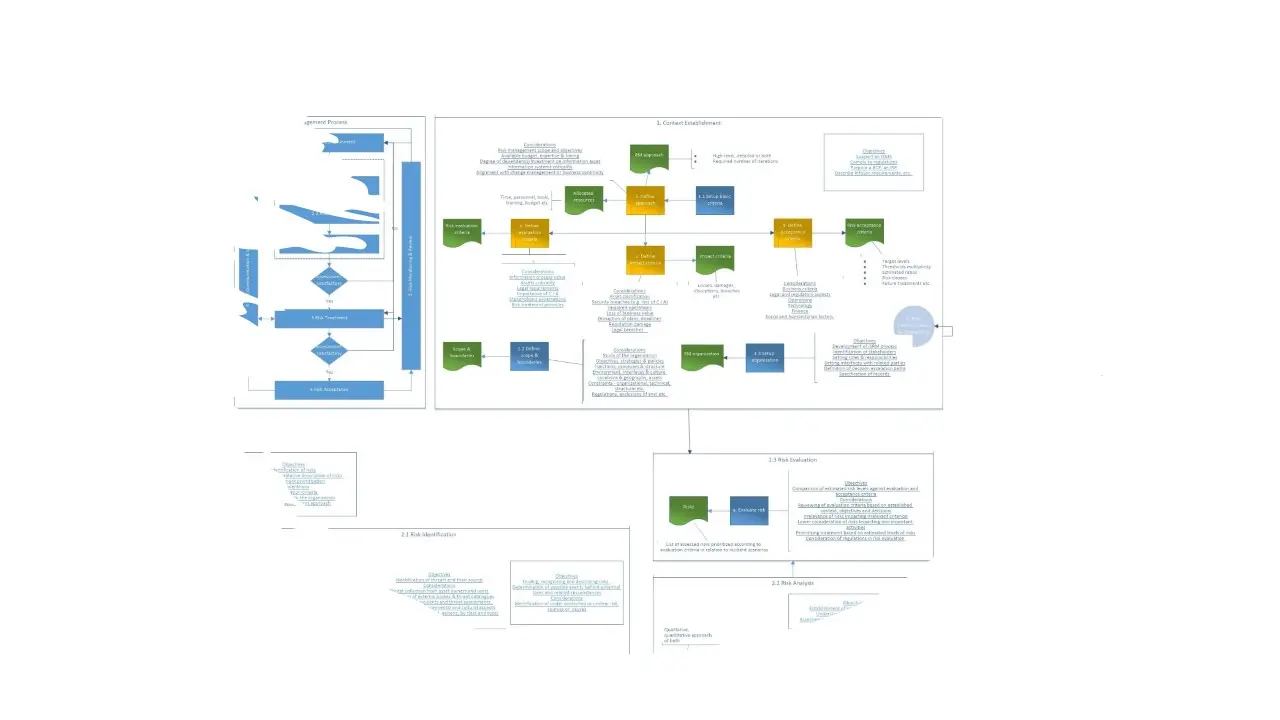
ISMS Information Risk Management Process v1 – Basic RM Process Flowchart.jpg
-
ISMS Information Risk Management Process v1 – Detailed Process Flowchart.jpg
-
ISMS Information Risk Management Process v1.vsdx
-
ISMS Information Risk Register.xlsm
-
ISMS Internal Audit Plan.docx
-
ISMS Internal Audit Procedure.docx
-
ISMS Management Plan.docx
-
ISMS Management Review Meeting Agenda.docx
-
ISMS Monitoring and Evaluation.docx
-
ISMS MRM Agenda.docx
-
ISMS Nonconformity Management Procedure.docx
-
ISMS Operating Procedure.docx
-
ISMS Policy.docx
-
ISMS Project Highlight Report.docx
-
ISMS Project Initiation Document.docx
-
ISMS Project Plan.mpp
-
ISMS Project Plan.xlsx
-
ISMS Risk Assessment and Treatment.docx
-
ISMS Risk Assessment Report.docx
-
ISMS Risk Assessment Worksheet.xlsx
-
ISMS Risk Treatment Plan.docx
-
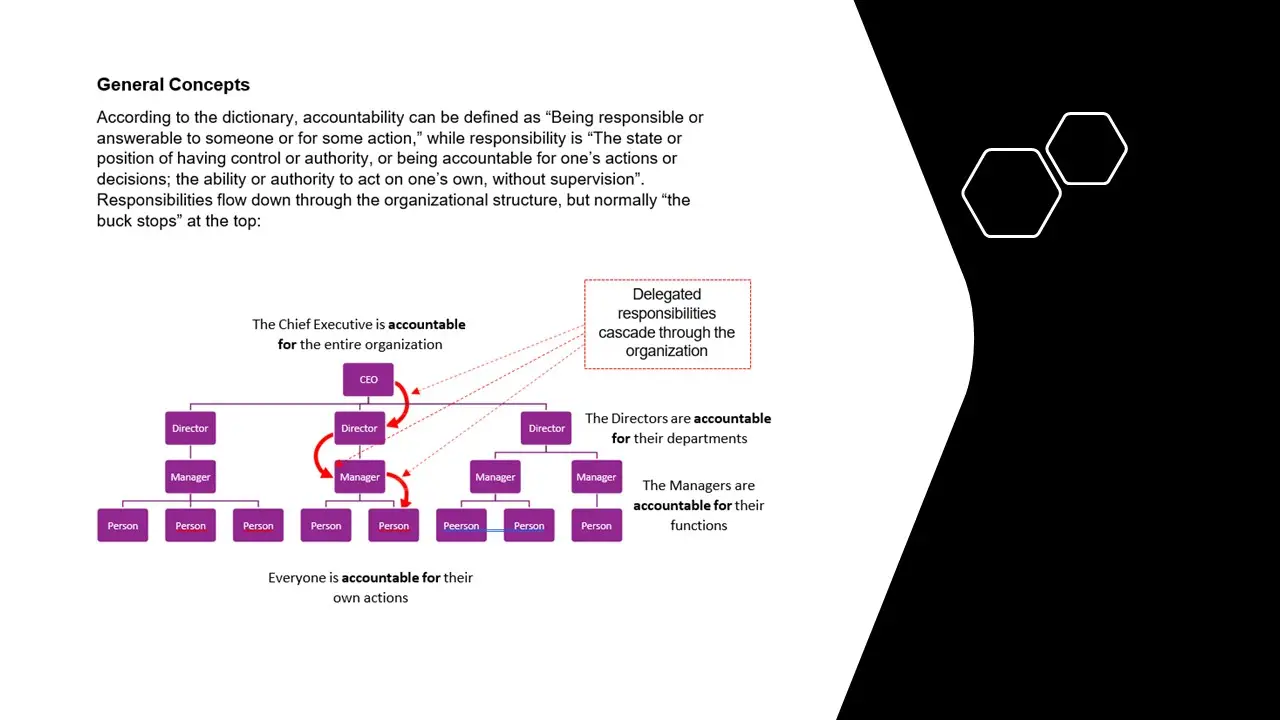
ISMS Roles and Responsibilities.docx
-
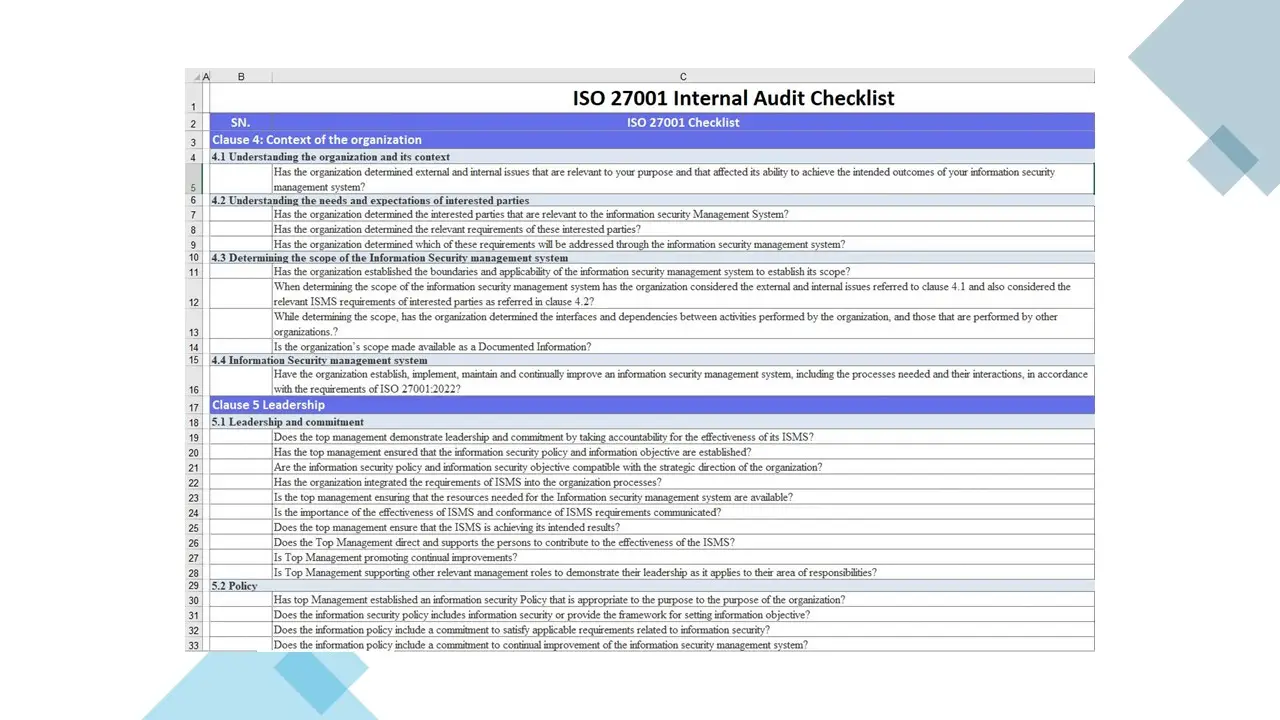
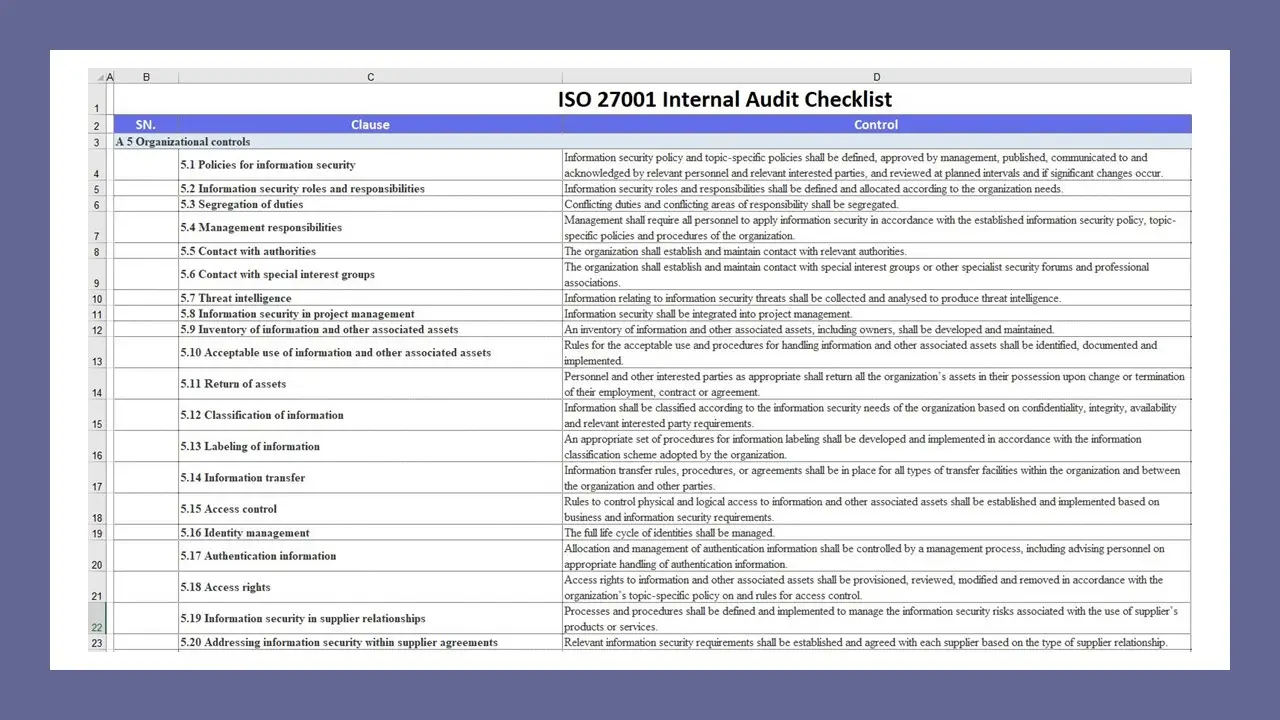
ISO 27001 Audit Checklist.xlsx
-
ISO 27001 Internal Audit Checklist.xlsx
-
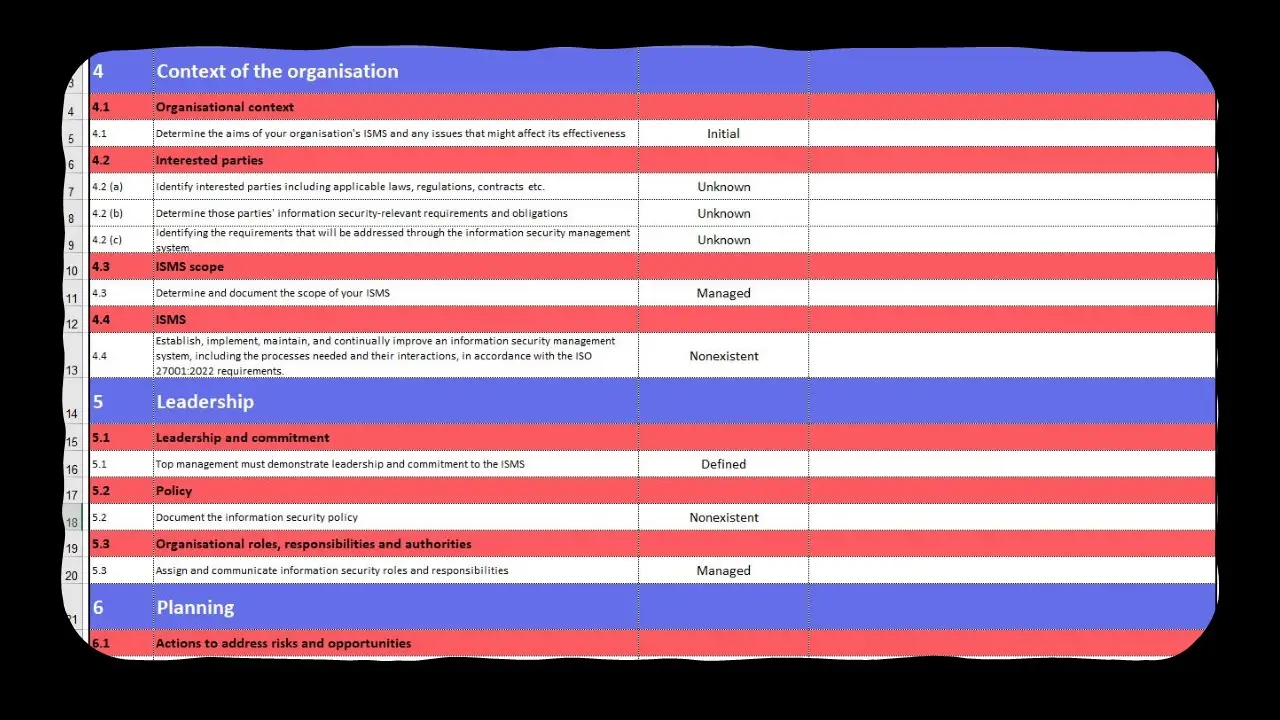
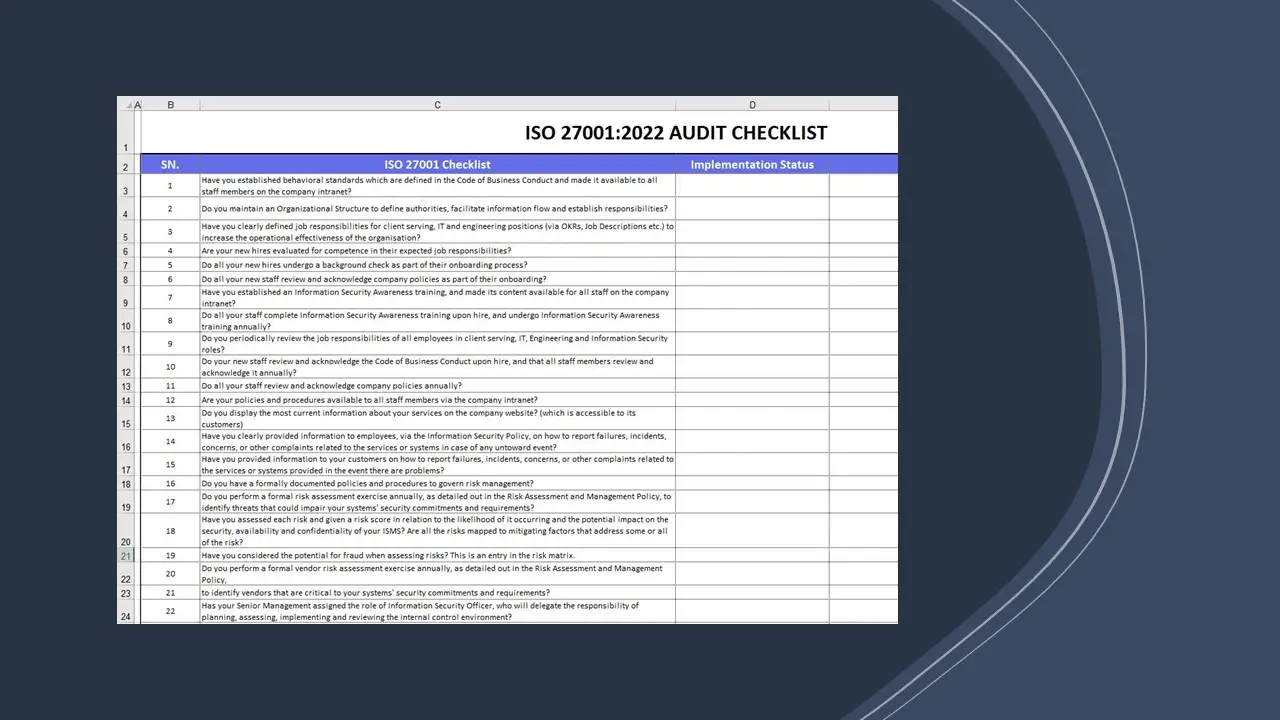
ISO 27001:2022 Assessment Tool.xlsx
-
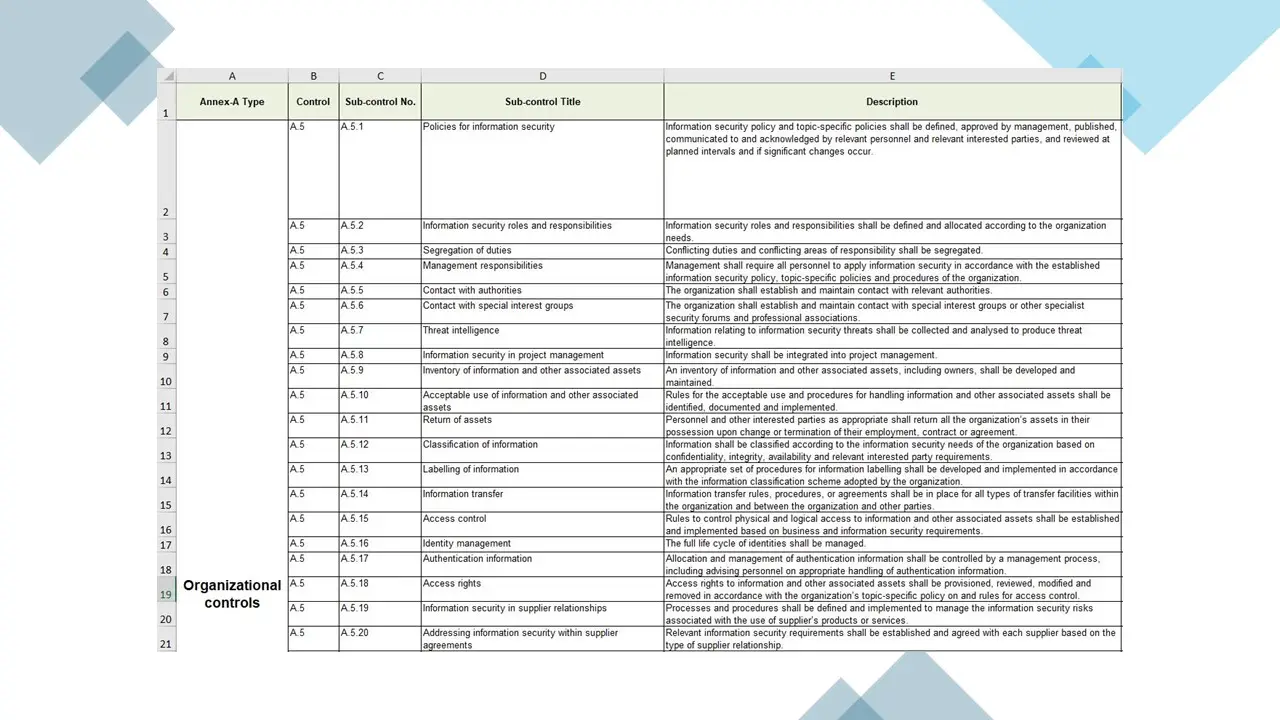
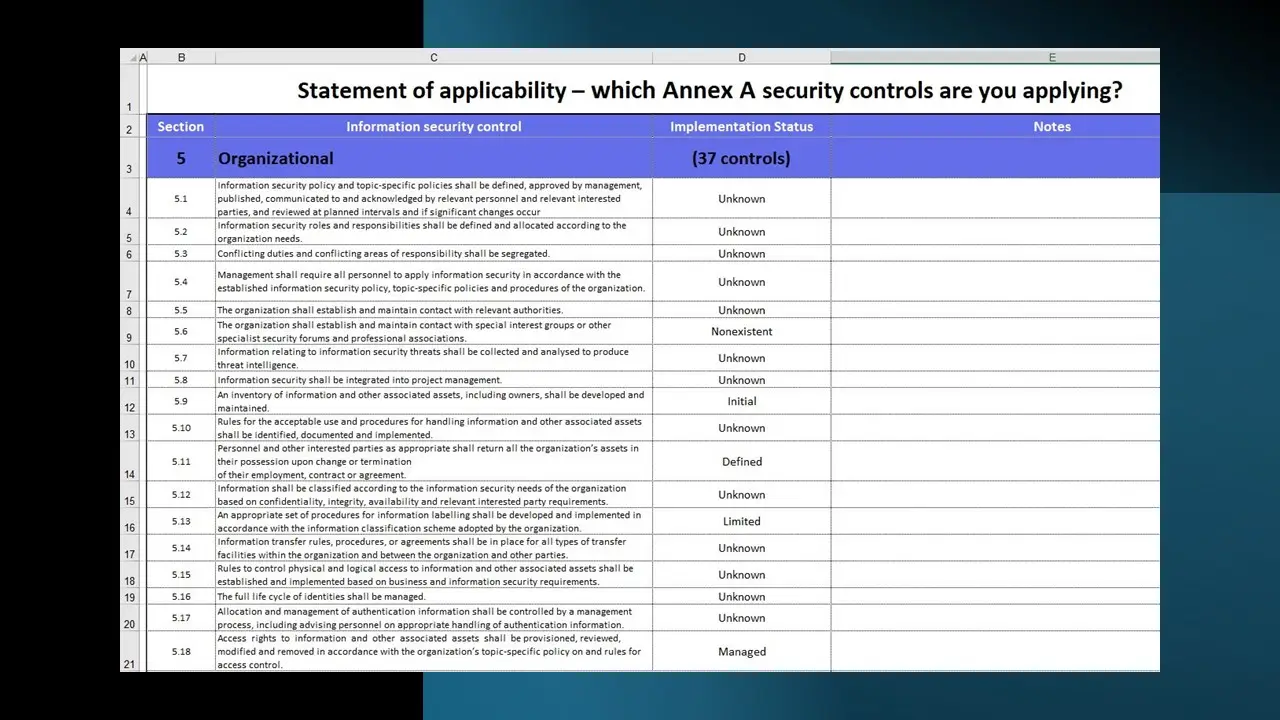
ISO 27001:2022 Statement of Applicability.xlsx
-
IT Audit Manager JD.docx
-
IT Auditor JD.docx
-
IT Systems Monitoring Procedure.docx
-
Legal and Regulatory Requirements Policy.docx
-
Legal Responsibilities Policy.docx
-
Log Monitoring Policy.docx
-
Malware Analyst JD.docx
-
Management Support Letter.docx
-
Media Disposal Procedure.docx
-
Mobile Computing Policy.docx
-
Model Policy on Change Management and Control.docx
-
Model Policy on Information Classification.docx
-
Model Policy on Information Security.docx
-
Model Policy on Malware.docx
-
Model Policy on Outsourcing.docx
-
Model Policy on Security Awareness and Training.docx
-
Network Risk Analyst JD.docx
-
Network Risk Manager JD.docx
-
Network Security Policy.docx
-
Offsite Assets Procedure.docx
-
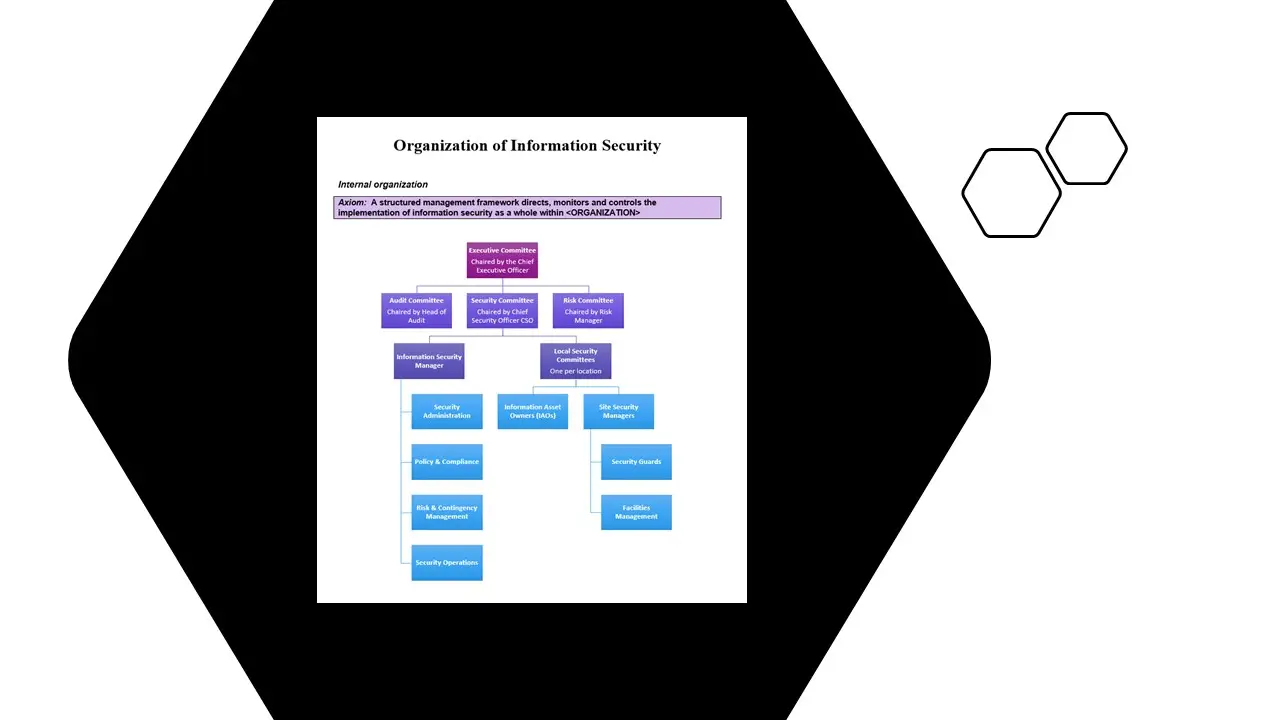
Organization of Information Security.docx
-
Password Reset Procedure.docx
-
Permissions Manager JD.docx
-
Physical Media Transfer Procedure.docx
-
Physical Security Design Policy.docx
-
Physical Security Manager JD.docx
-
Physical Security Policy.docx
-
Preventive Action Procedure.docx
-
Privacy Officer JD.docx
-
Project Management Security Policy.docx
-
Recruitment and New Joiner Checklist.docx
-
Release Management Policy.docx
-
Remote Working Policy.docx
-
Removable Media Management Procedure.docx
-
Roles and Responsibilities for Contingency Planning.docx
-
Secure Areas Policy.docx
-
Secure Coding Policy.docx
-
Secure Data Disposal Policy.docx
-
Secure Development Policy.docx
-
Secure Systems Engineering Policy.docx
-
Security Administration Team Leader JD.docx
-
Security Administrator JD.docx
-
Security Awareness Contact JD.docx
-
Security Awareness Manager JD.docx
-
Security Awareness Officer JD.docx
-
Security Incident Procedure.docx
-
Segregation of Duties Policy.docx
-
SGSI 6.1 SoA 2022 Español.xlsx
-
SGSI 6.1 SoA 2022 Português.xlsx
-
Software Policy.docx
-
Standard NDA.docx
-
Standard SLA.docx
-
Technical Briefing on Security Roles and Responsibilities Matrix.docx
-
Technology Risk Manager JD.docx
-
Threat Intelligence Policy.docx
-
Vendor Access Procedure.docx
-
Vendor Evaluation Process.docx
-
Vendor Management Policy.docx
-
Vendor Security Agreement.docx
-
Vulnerability Assessment Procedure.docx
-
Vulnerability Management Policy.docx
-
Web Filtering Policy.docx
-
Whistleblowers’ Hotline Case Handler JD.docx
-
Whistleblowers’ Hotline Manager JD.docx
-
Workplace Information Security Representative JD.docx
ISO Compliance
All documents of this Toolkit are developed based on ISO 27001:2022 Standard
Hence, You just need to download and selected document and add your company name and logo.