Product Description
The NIST Risk Management Toolkit is a set of professional collection of over 50 files covering every facet of information security risk management as per NIST Cybersecurity Framework (CSF) and NIST SP 800-30. This toolkit serves as a complete package to streamline the identification, assessment, treatment, and monitoring of security risks within an organization.
By leveraging NIST Toolkit, businesses, government agencies, and security teams can efficiently implement risk-based security controls, conduct thorough risk assessments, and achieve compliance with best practices and regulatory requirements.
Key Features:
- User-Friendly Formats: Includes Excel templates, Word documents, PDFs, and PowerPoint presentations to suit various needs.
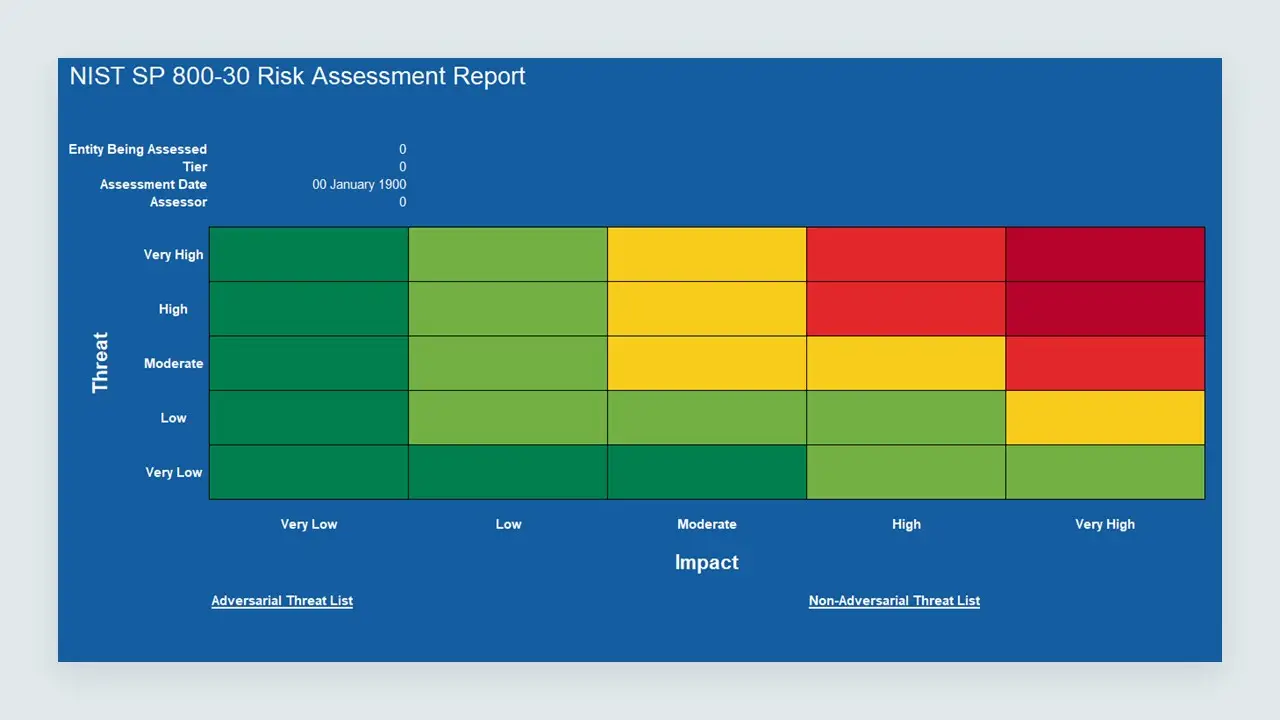
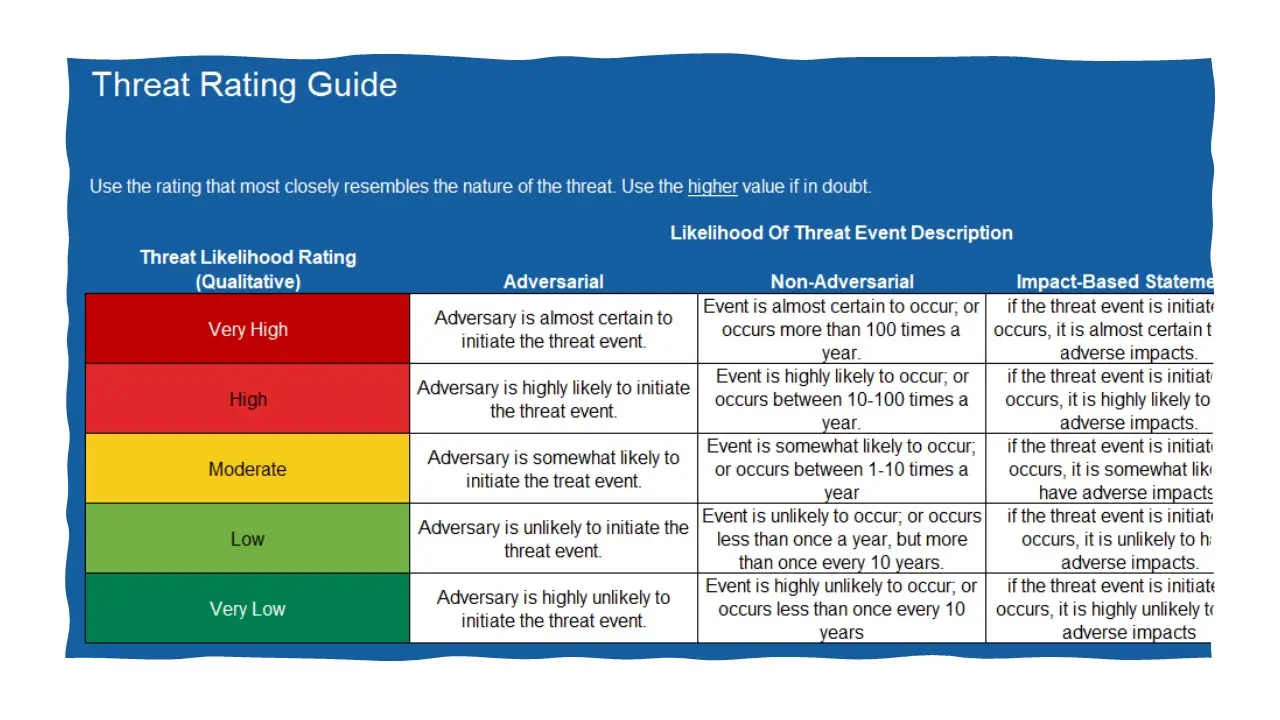
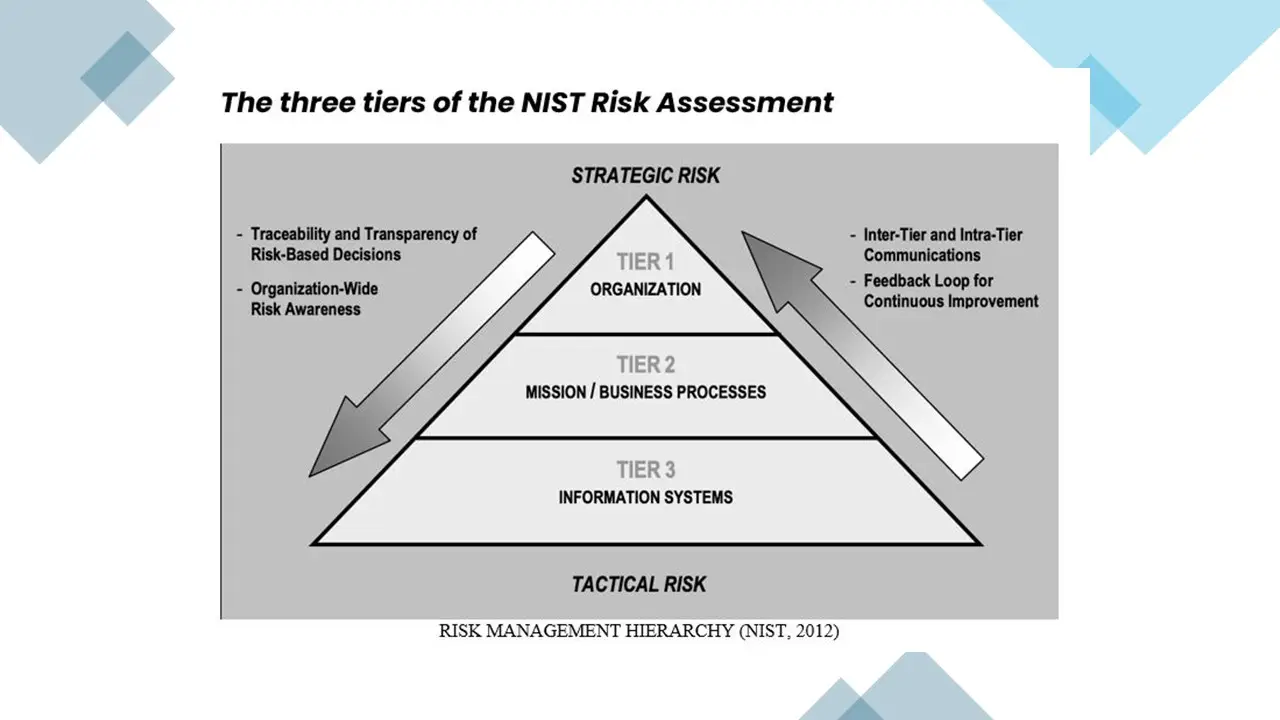
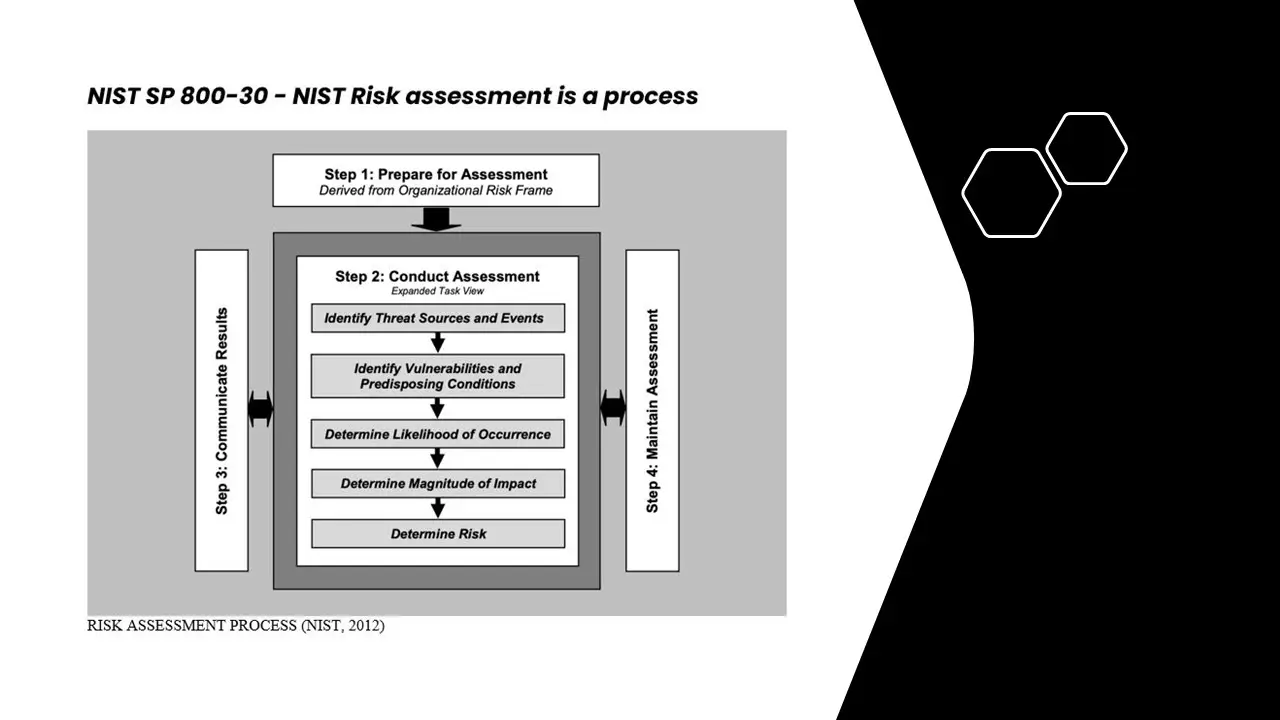
- NIST SP 800-30 Compliance: Fully aligned with the NIST Risk Assessment methodology, ensuring a structured and standardized approach to risk evaluation.
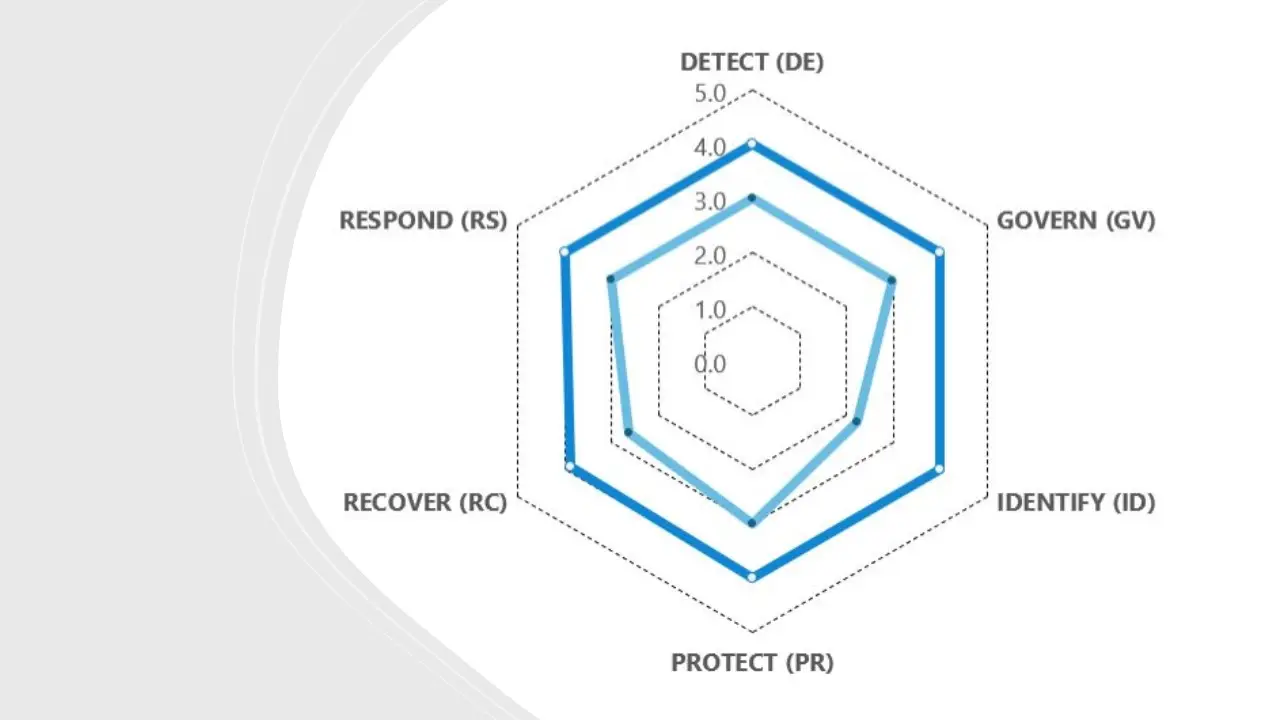
- NIST CSF Integration: Designed to align with the five core functions of NIST CSF (Identify, Protect, Detect, Respond, Recover).
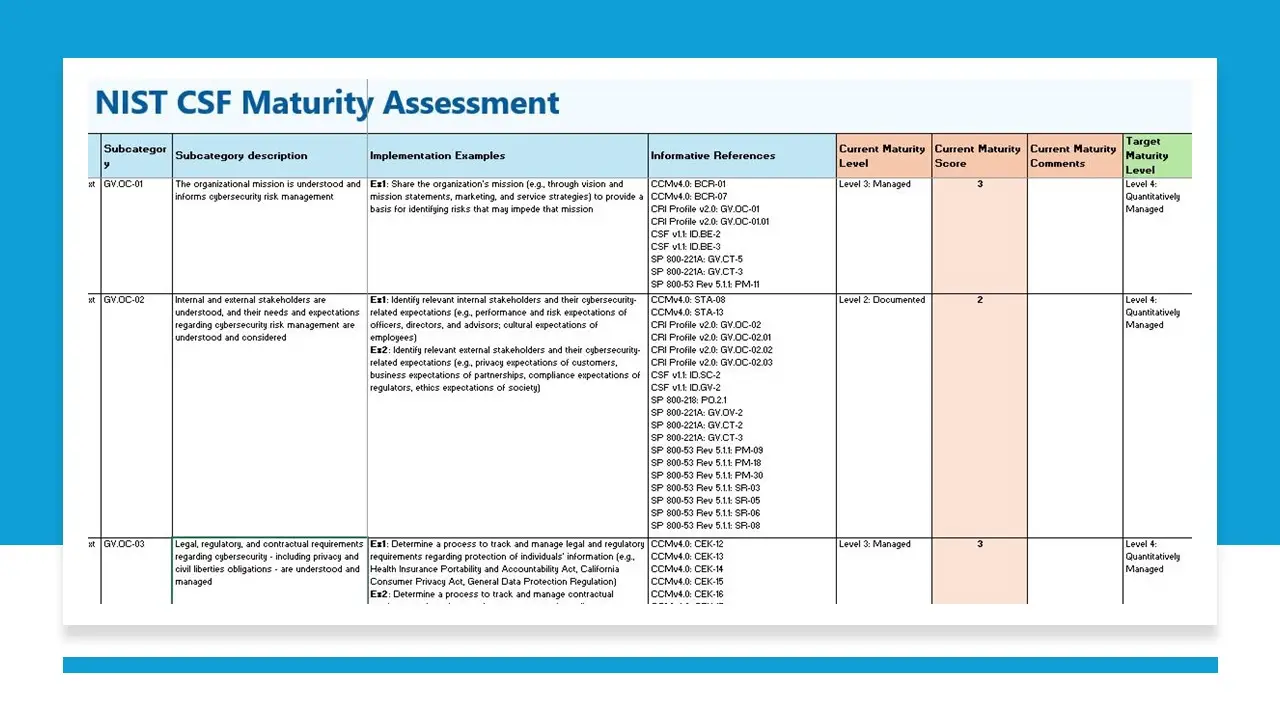
- Comprehensive Risk Questionnaires: Detailed, pre-configured risk assessment forms with automated scoring.
- Automated Risk Calculations: Excel-based tools for dynamic risk scoring, prioritization, and visualization of security posture.
- Gap Analysis & Remediation Plan: Helps organizations identify security weaknesses and develop structured mitigation strategies.
- Vendor Risk Management Toolkit: Dedicated templates to assess risks associated with third-party vendors.
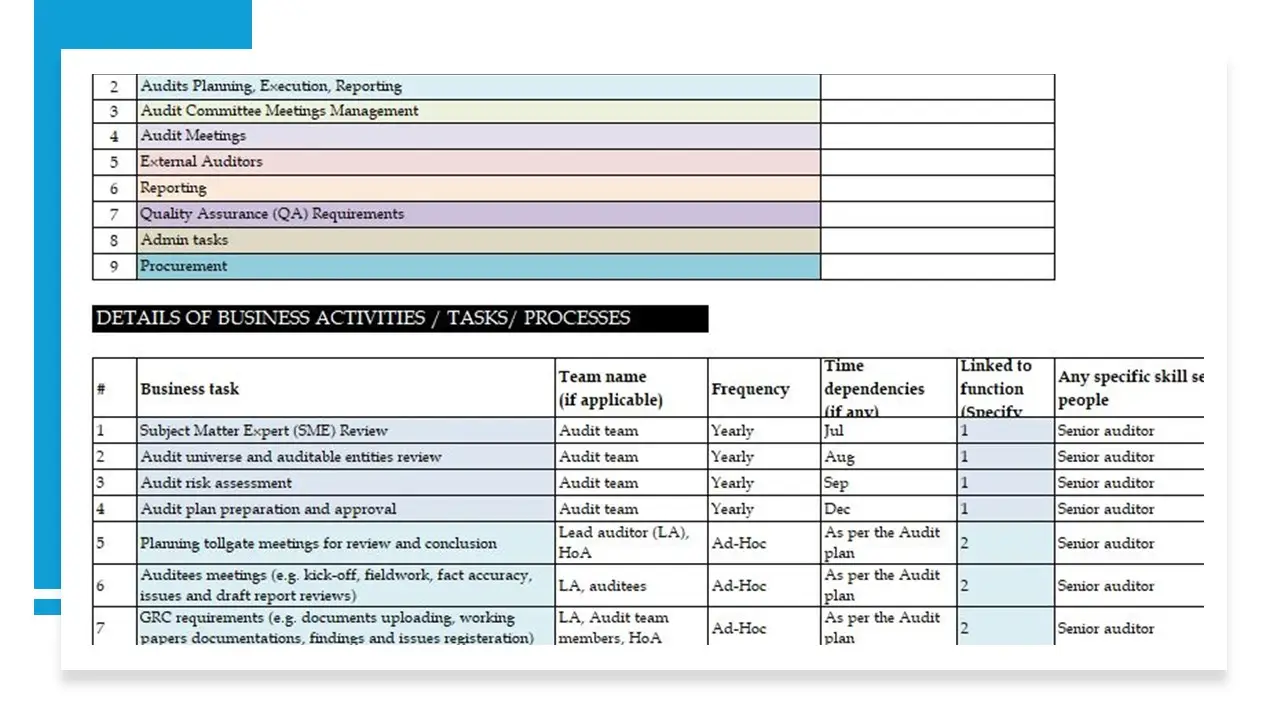
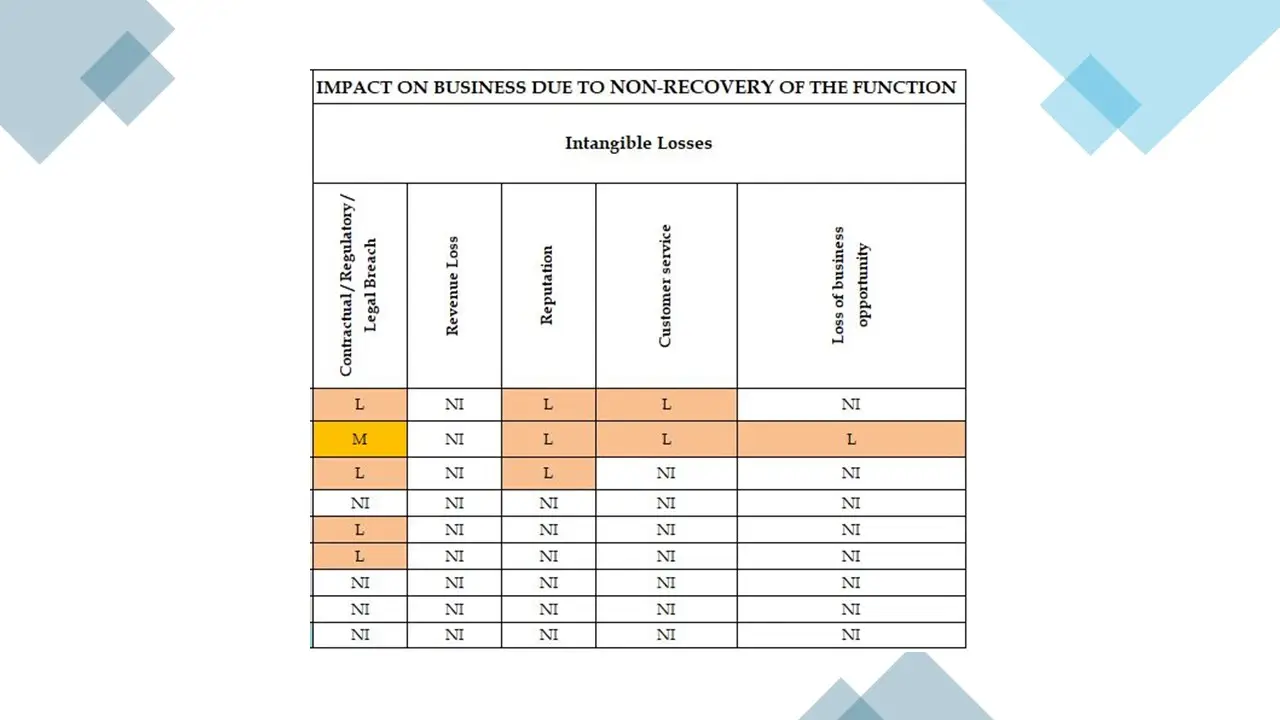
- Business Impact Analysis (BIA): Assess the potential consequences of risk events on business operations.
- Incident Response and Recovery Planning: Documentation templates for handling security incidents, breaches, and disaster recovery processes.
- Audit and Compliance Checklists: Step-by-step verification tools to ensure regulatory compliance.
- Policy and Procedure Templates: Pre-built security policies covering access control, encryption, incident management, and more.
- Risk Treatment Plan: Pre-defined controls and mitigation measures mapped to NIST standards.
NIST Toolkit consist of the following documents:
- BIA Assessment Tool
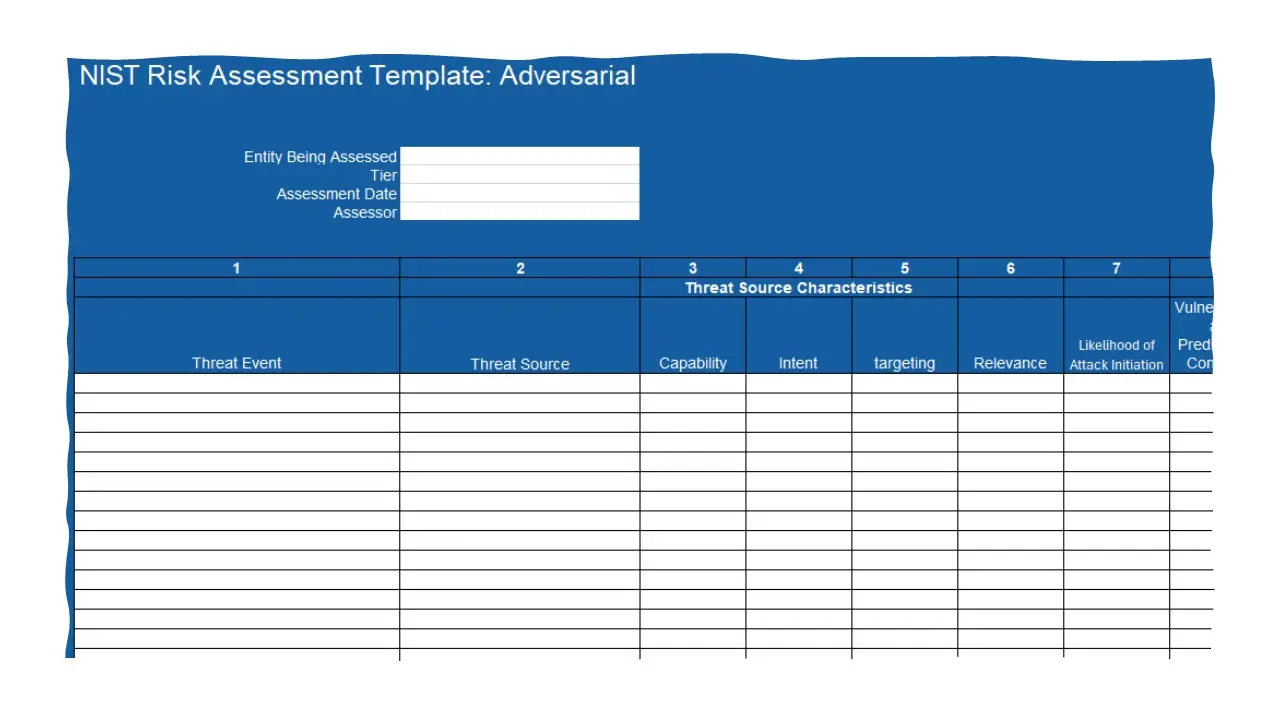
- NIST 800-30 Risk Assessment Template
- NIST CSF 2.0 Maturity Assessment Template
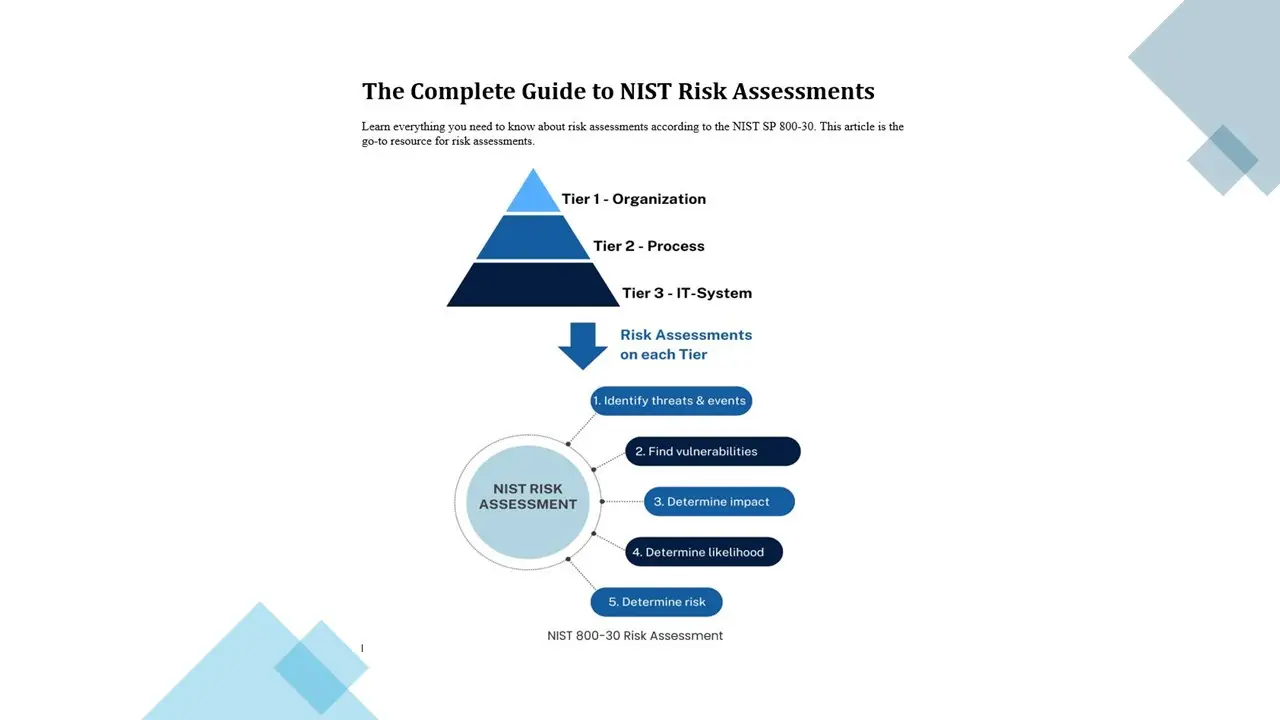
- The Complete Guide to NIST 800-30 Risk Assessments
- Acceptable Use Policy
- Access Control Policy
- Anti-Malware Policy
- Asset Handling Policy
- BIA Procedure
- BYOD Policy
- Change Management Policy
- Cloud Services Security Policy
- Configuration Management Procedure
- Copyright Compliance Policy
- Cryptographic Policy
- Cyber Security Risk Management Framework
- Data Masking Policy
- Data Retention Policy
- Development Environment Policy
- DLP Policy
- Email Usage Policy
- Employee Disciplinary Process
- Employee Movement and Termination Checklist
- Employee Screening Checklist
- Employment Contracts Clauses
- Incident Response Procedure
- Information Security Classification Policy
- Information Security Labelling Procedure
- Information Security Policy
- Information Security Roles and Responsibilities
- Internet Acceptable Use Policy
- Legal and Regulatory Requirements Procedure
- Management Support Letter
- Media Disposal Procedure
- Mobile Computing Policy
- Network Security Policy
- Physical Security Design Policy
- Physical Security Policy
- Recruitment and New Joiner Checklist
- Remote Working Policy
- Risk Assessment and Treatment
- Risk Assessment Report
- Risk Treatment Plan
- Secure Areas Policy
- Secure Coding Policy
- Secure Development Policy
- Segregation of Duties Policy
- Standard NDA
- Vendor Access Procedure
- Vendor Management Policy
- Vendor Security Agreement
- Vulnerability Assessment Procedure
- Vulnerability Management Policy
- Web Filtering Policy
Why Choose NIST Toolkit?
This toolkit provides a structured, repeatable, and comprehensive approach to risk assessment and cybersecurity governance, ensuring that your organization remains compliant, resilient, and secure. Designed for CISOs, risk managers, IT security teams, and compliance officers, this toolkit eliminates guesswork and accelerates NIST-aligned risk management implementation.
Get Your Security Risks Under Control Today!
Whether you’re looking to strengthen organizational risk management, achieve compliance, or enhance cybersecurity resilience, this toolkit is your ultimate resource to achieving effective information security governance under the NIST frameworks.
This Tool is developed based on NIST CSF and NIST 800-30 Special Publication.
Find More Products:
Documentation Toolkits
All Products
Frequently Asked Questions (FAQ)
What is the NIST Cyber Risk Management Toolkit?
The NIST Toolkit is a complete set of 50+ professional templates aligned with the NIST CSF and NIST SP 800-30. It helps businesses manage cybersecurity risks by providing ready-made tools for risk assessment, incident response, compliance checks, and vendor security evaluation.
Who should use the NIST Toolkit?
This toolkit is ideal for CISOs, IT managers, risk officers, consultants, and government agencies. It’s designed for anyone responsible for cybersecurity risk management, compliance, or implementing the NIST Cybersecurity Framework.
What’s included in the NIST Toolkit?
It includes editable Excel, Word, and PDF templates—risk assessment forms, policy documents, BIA tools, vendor risk procedures, gap analysis, audit checklists, incident response plans, and more. All are built to support structured risk governance under NIST standards.
Is the toolkit compliant with NIST SP 800-30 and CSF?
Yes. The toolkit strictly follows NIST SP 800-30 guidelines and is integrated with NIST CSF’s five core functions—Identify, Protect, Detect, Respond, and Recover. It’s built to help organizations meet NIST-aligned compliance goals.
Can I customize these NIST documents for my organization?
Absolutely. All templates are editable in Microsoft Office formats. You can easily insert your organization’s name, logo, and data. Automated scoring and built-in risk models make customization quick and effective.