Product Description
DORA Toolkit is used to help organizations enhance business resilience and ensure compliance with the Digital Operational Resilience Act (DORA).
This toolkit is specifically designed for organizations operating in the financial sector. DORA Toolkit equips you with the essential documentation and processes to meet DORA’s stringent operational resilience requirements.
DORA Toolkit provides an all-encompassing package of meticulously crafted documents covering every critical element of digital operational resilience. From creating incident response procedures to managing ICT risk assessments and third-party service provider oversight, this Assured Toolkit ensures your organization is prepared for both regulatory scrutiny and operational challenges.
Each document is developed by industry experts and aligns with DORA requirements to ensure precision and compliance. The templates are fully customizable, making it simple to adapt them to your organization’s unique structure and needs, saving you valuable time and resources.
Ensure regulatory compliance, mitigate operational risks, and build trust with stakeholders. Invest in this Premium Toolkit today and create a robust framework for digital operational resilience that reinforces your organization’s stability and reputation.
Why Do Organizations Need to Comply with DORA?
The Digital Operational Resilience Act (DORA) mandates financial entities to strengthen their digital operational resilience by ensuring their ICT systems are secure, reliable, and capable of withstanding potential threats. Compliance with DORA is not just a regulatory requirement but a business imperative to safeguard against cyberattacks, system failures, and operational disruptions.
DORA compliance helps organizations maintain trust with customers and regulatory bodies by demonstrating accountability and preparedness. It mitigates the financial and reputational damage caused by ICT-related incidents and ensures uninterrupted business operations. Adopting DORA-aligned practices enhances organizational resilience, improves risk management, and positions businesses as leaders in digital security and reliability within the financial sector.
Additionally, adhering to DORA enables organizations to address broader global regulatory trends, fostering cross-border compliance and operational consistency. Compliance is a competitive advantage that strengthens customer confidence and positions your organization as a trusted, resilient player in the financial industry.
This toolkit consists of the following documents:
- Acceptable Use Policy.docx
- Access Control Policy.docx
- Anti-Malware Policy.docx
- Asset Handling Policy.docx
- Audit Schedule.docx
- Audits Procedure.docx
- Backup Policy.docx
- BIA Procedure.docx
- BIA Tool.xlsx
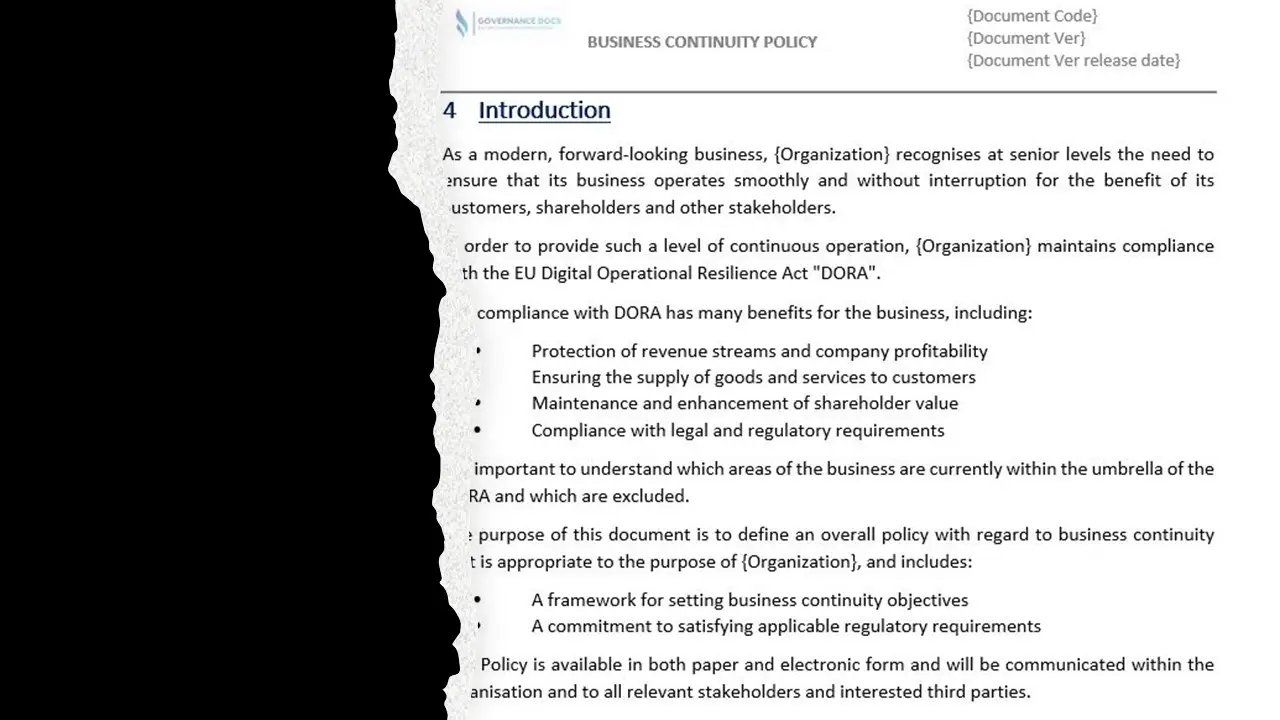
- Business Continuity Policy.docx
- Business Continuity Test Plan.docx
- Businesss Continuity and Disaster Recovery Plan.docx
- BYOD Policy.docx
- Change Management Policy.docx
- Configuration Management Procedure.docx
- Cryptographic Policy.docx
- Data Masking Policy.docx
- DLP Policy.docx
- DORA Roles Responsibilities.docx
- Email Usage Policy.docx
- Employee Disciplinary Process.docx
- Employee Movement and Termination Checklist.docx
- Employee Screening Checklist.docx
- Employment Contracts Clauses.docx
- ICT Systems Monitoring Procedure.docx
- Incident Log Form.xlsx
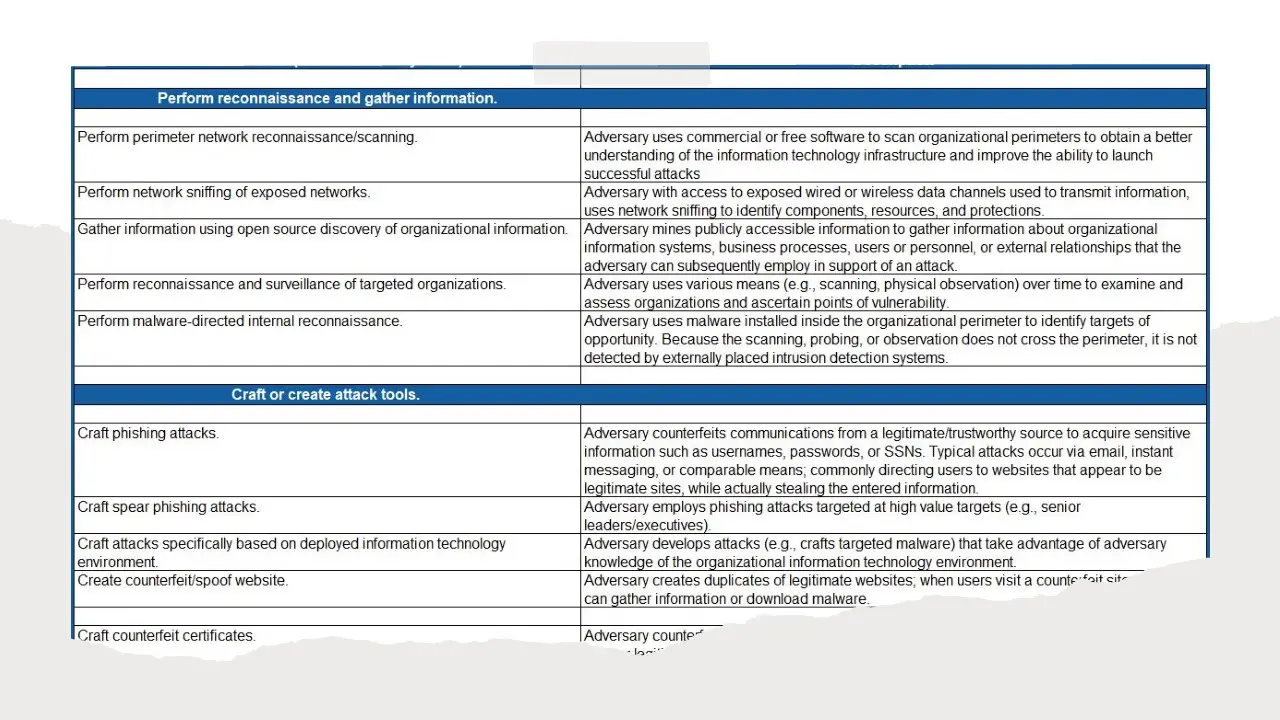
- Incident Response Procedure.docx
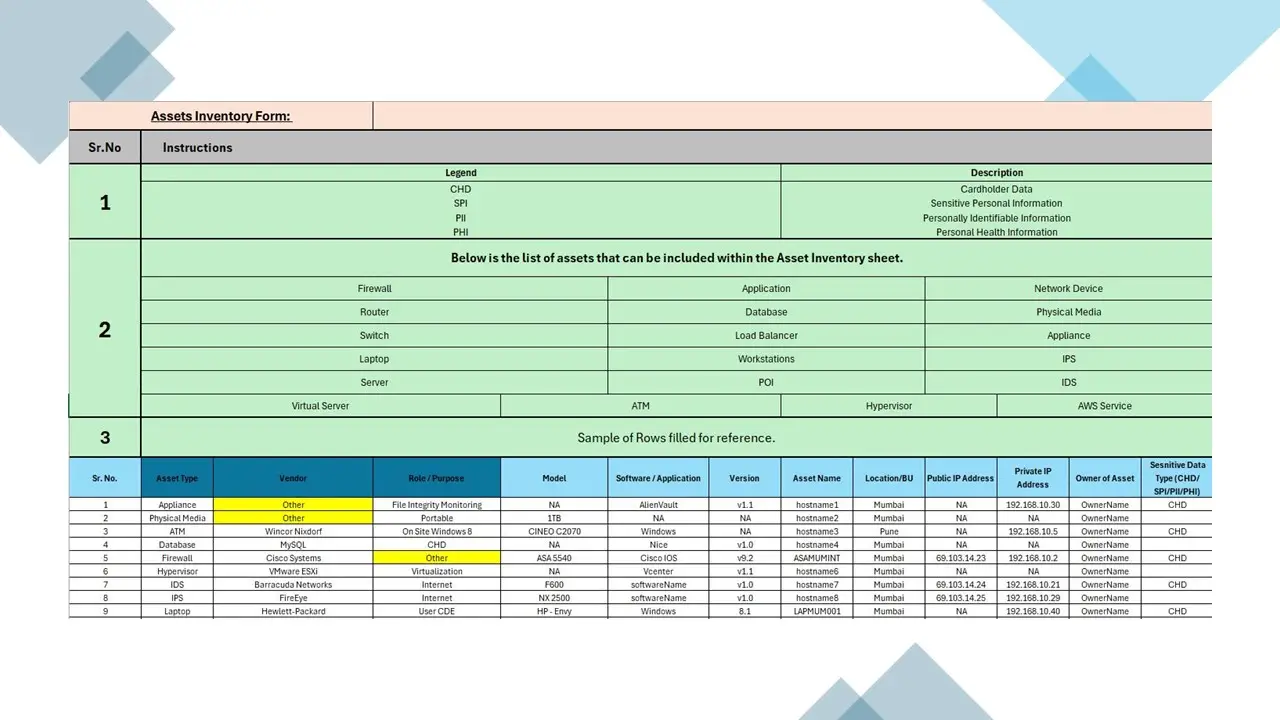
- Information Asset Inventory.xlsx
- Information Security Classification Policy.docx
- Information Security Policy.docx
- Internal Audit Plan.docx
- Internet Acceptable Use Policy.docx
- Legal and Regulatory Requirements Policy.docx
- Legal Responsibilities Policy.docx
- Legal, Regulatory and Contractual Requirements Procedure.docx
- Log Monitoring Policy.docx
- Network Security Policy.docx
- Nonconformity Management Procedure.docx
- Offsite Assets Procedure.docx
- Physical Security Policy.docx
- Post Incident Report.docx
- Recruitment and New Joiner Checklist.docx
- Risk Assessment and Treatment.docx
- Risk Assessment Report.docx
- Risk Assessment Worksheet.xlsx
- Risk Treatment Plan.docx
- Secure Areas Policy.docx
- Secure Coding Policy.docx
- Segregation of Duties Policy.docx
- Training and Awareness Procedure.docx
- Vendor Access Procedure.docx
- Vendor Evaluation Process.docx
- Vendor Management Policy.docx
- Vendor Security Agreement.docx
- Vulnerability Assessment Procedure.docx
- Vulnerability Management Policy.docx
How to Use This Toolkit?
Simply add your organization’s name and logo to the documents, and ensure the implementation of the documented policies and procedures within your operational framework.
Based on Which Regulation Are These Documents Written?
All documents in this Toolkit are developed based on the Digital Operational Resilience Act (DORA). However, they are adaptable for use in other jurisdictions with minimal adjustments, making them versatile and suitable for broader regulatory environments.
Ready to transform your digital resilience strategy? Invest in the DORA Toolkit and take the first step towards unwavering operational resilience and compliance.