Social Engineering Attack Procedure Template
Introducing our “Social Engineering Attack Procedure Template” – a powerful tool designed to help organizations enhance their security measures against social engineering attacks. This comprehensive digital product provides a structured framework to establish effective procedures and protocols for detecting, preventing, and responding to social engineering threats.
Social engineering attacks exploit human psychology to manipulate individuals into divulging sensitive information, granting unauthorized access, or performing actions that compromise security. With our template, you can proactively fortify your organization’s defenses against these sophisticated attacks.
Key Features:
1. Comprehensive Procedure Framework: Our template offers a comprehensive framework that covers all stages of a social engineering attack, from identification to mitigation and recovery. It guides you through the necessary steps to establish robust security protocols and countermeasures.
2. Awareness and Training: Enhance employee awareness and preparedness through targeted training programs. The template includes guidelines for educating personnel about the various forms of social engineering attacks, their indicators, and best practices for prevention.
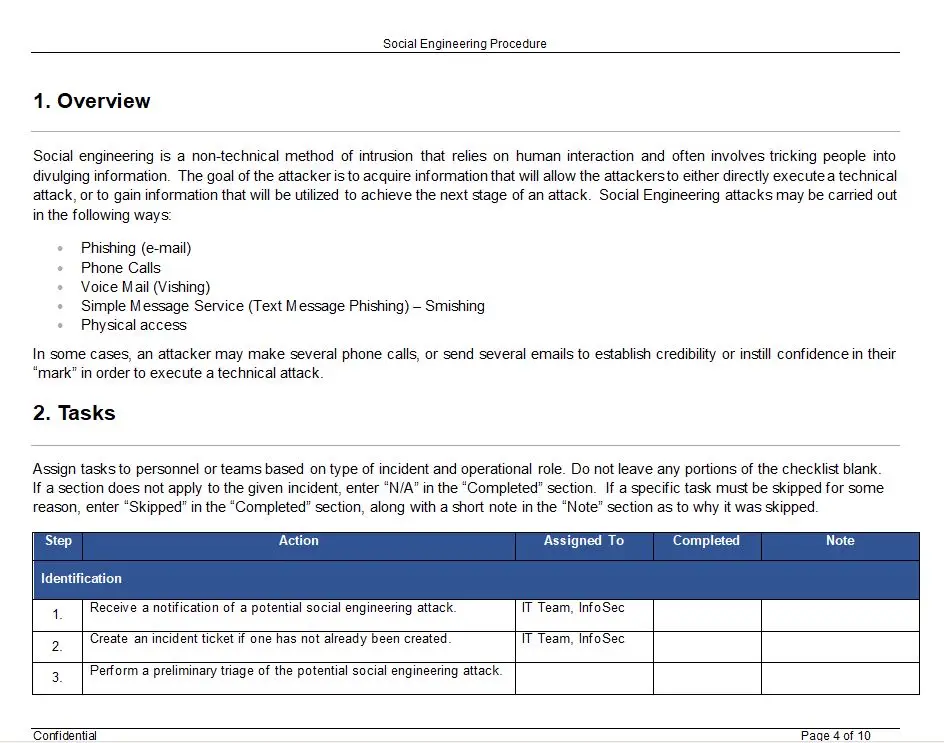
3. Incident Response and Reporting: Establish clear procedures for identifying and responding to social engineering incidents. The template provides guidelines for incident reporting, investigation, evidence collection, and documentation to ensure swift and effective response measures.
4. Security Controls and Countermeasures: Implement preventive measures and security controls to mitigate social engineering risks. The template offers guidance on measures such as multi-factor authentication, access controls, user awareness campaigns, and security awareness training to strengthen your defenses.
5. Social Engineering Simulation Exercises: Conduct simulated social engineering exercises to test the effectiveness of your security controls and personnel readiness. The template includes guidelines for planning, executing, and evaluating these exercises, allowing you to identify vulnerabilities and address them proactively.
6. Policy and Procedure Development: Develop robust policies and procedures specific to social engineering threats. The template assists you in creating guidelines for incident reporting, employee responsibilities, acceptable use of information, and access control protocols.
7. Compliance and Best Practice Alignment: Align your social engineering attack procedures with industry best practices and compliance standards. The template ensures adherence to recognized frameworks, such as ISO 27001, NIST SP 800-61, or industry-specific regulations.
8. Customizable and Adaptable: Tailor the template to your organization’s unique requirements. Customize sections, add additional guidelines, or modify procedures to align with your specific industry, size, and risk profile.
Invest in our Social Engineering Attack Procedure Template today and strengthen your organization’s resilience against social engineering threats. Empower your personnel, bolster your security measures, and safeguard your valuable information and assets from the growing menace of social engineering attacks.
Number of Pages: 10
A step by step procedure describes the step needed in the case of Social Engineering Attack
All GovernanaceDocs documents are developed based on well-known standards such as NIST CSF, ISO 27001, ISO 22301, PCI-DSS and HIPAA.
Hence, You just need to download and selected document and add your company name and logo.








I couldn’t be happier with these document templates. They’ve made a significant difference in our efficiency and document quality.
We’ve tried other templates, but these are in a league of their own. Highly recommended!
We can’t thank the creators enough for these templates. They’ve made document creation a breeze, and the variety of templates available is impressive.
These document templates have saved us an immense amount of time and effort. They cover all the necessary details and are regularly updated.