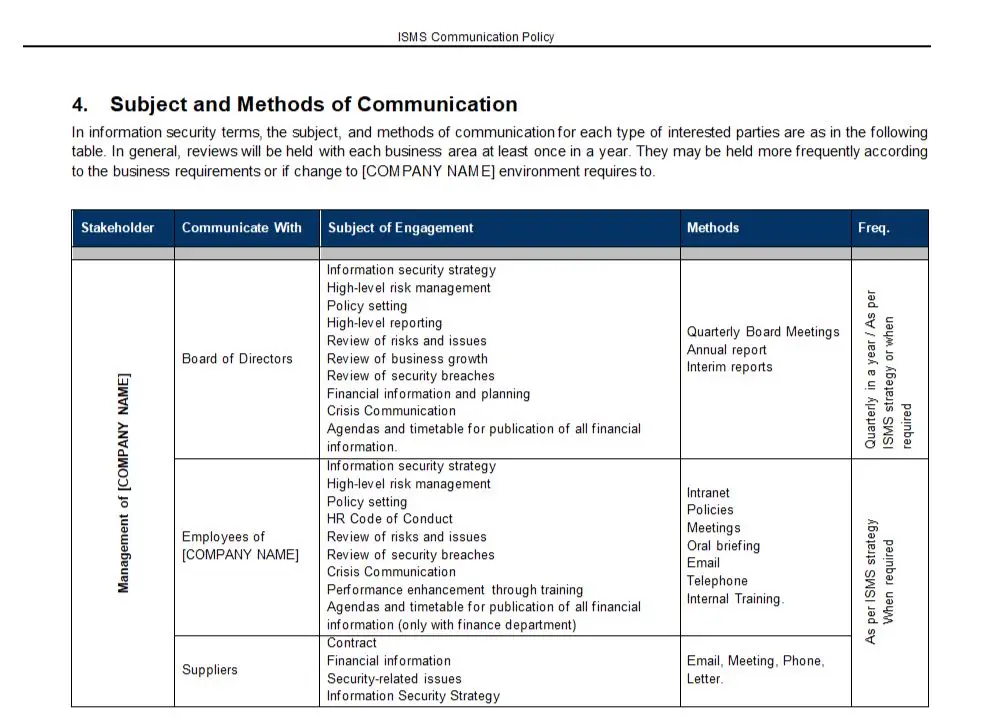
Access Control Policy
In the ever-evolving landscape of information security, where the stakes are higher than ever, the Access Control Policy emerges as a beacon of protection and assurance. This comprehensive policy is meticulously crafted to govern access to systems containing Protected Health Information (PHI), a critical component in the healthcare sector where privacy and security are paramount.
At the heart of the Access Control Policy is its unwavering commitment to safeguarding sensitive information. It is not merely a set of guidelines but a robust framework that ensures only authorized individuals have access to PHI. This policy is a cornerstone for organizations striving to comply with the Health Insurance Portability and Accountability Act (HIPAA), which mandates stringent measures to protect patient information.
One of the key features of the Access Control Policy is its adaptability across various product categories, including All Products, HIPAA, and Information Security. This versatility ensures that the policy is not confined to a single domain but can be seamlessly integrated into diverse systems and environments. Whether it’s a small clinic or a large hospital network, the Access Control Policy provides a scalable solution that meets the unique needs of each organization.
The policy is identified by the attribute number 8022, a testament to its specificity and precision. This identifier allows for easy reference and implementation, ensuring that organizations can quickly align their access control measures with industry standards. The Access Control Policy is not just a document; it is a dynamic tool that evolves with the changing landscape of information security.
The benefits of implementing the Access Control Policy are manifold. First and foremost, it provides peace of mind to both healthcare providers and patients, knowing that sensitive information is protected by a comprehensive and effective security measure. It also enhances the organization’s reputation, demonstrating a commitment to privacy and security that can set it apart in a competitive market.
Moreover, the Access Control Policy streamlines the process of access management, reducing the risk of unauthorized access and potential data breaches. By clearly defining roles and responsibilities, it minimizes confusion and ensures that all personnel understand their part in maintaining the security of PHI. This clarity not only enhances operational efficiency but also fosters a culture of accountability and vigilance.
The value proposition of the Access Control Policy lies in its ability to transform how organizations approach information security. It is not just about compliance; it is about building a resilient defense against the myriad threats that loom in the digital age. By adopting this policy, organizations are not only protecting their data but also fortifying their future against unforeseen challenges.
In conclusion, the Access Control Policy is more than a regulatory requirement; it is a strategic asset that empowers organizations to navigate the complexities of information security with confidence. Its comprehensive nature, coupled with its adaptability and precision, makes it an indispensable tool for any entity handling Protected Health Information. As the digital landscape continues to evolve, the Access Control Policy stands as a testament to the enduring importance of security and privacy in the healthcare industry.
All GovernanaceDocs documents are developed based on well-known standards such as NIST CSF, ISO 27001, ISO 22301, PCI-DSS and HIPAA.
Hence, You just need to download and selected document and add your company name and logo.








Reviews
There are no reviews yet