Data Protection Policy
The documents are created in Microsoft Office format and are ready to be customized to your organization’s applicable law. The Cryptographic Key Management and PIN Security Policy template documents help you comply with the PCI-PIN and financial sector security requirements.
This document is written by a CISSP-qualified auditor with over 30 years of experience in Information Security, our template provides a wealth of expertise and knowledge in an easy-to-use format.
With an emphasis on quality and details, this template covers everything an organization needs to establish a robust PIN Security Policy. It serves as a critical tool for ensuring compliance with PCI Standards and fostering continuous improvement in your data management practices.
GovernanceDocs have created this document to align with the highest standards in PCI Council Security requirements.
Number of Pages: 23
Table of Content:
1. Introduction
1.1 Purpose
1.2 Scope
1.3 Audience
1.4 Policy Overview
1.5 Compliance and Regulatory Framework
2. Roles and Responsibilities
2.1 Key Custodians
2.2 Cryptographic Officer (CO)
2.3 System Administrators
2.4 Auditors
2.5 Third-Party Service Providers
3. Cryptographic Key Management Principles
3.1 Definition of Cryptographic Keys
3.2 Key Life Cycle
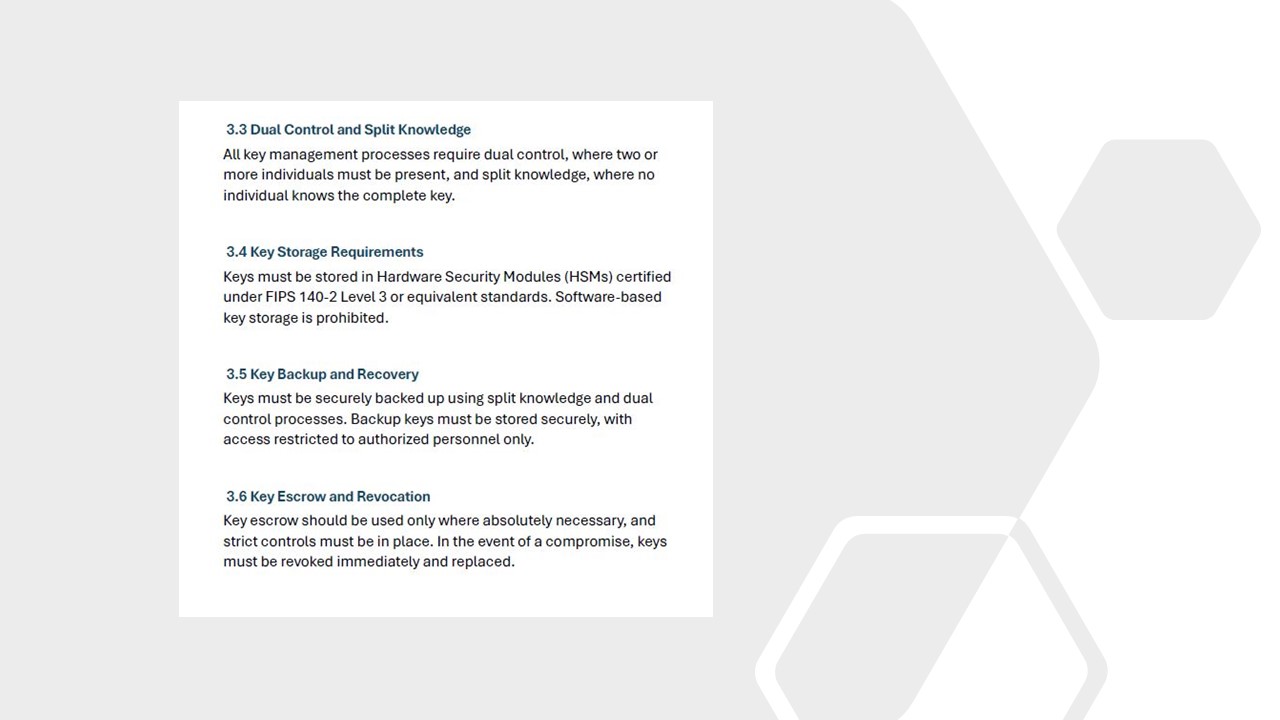
3.3 Dual Control and Split Knowledge
3.4 Key Storage Requirements
3.5 Key Backup and Recovery
3.6 Key Escrow and Revocation
3.7 Key Expiry and Rotation Policies
3.8 Key Inventory and Tracking
4. PIN Security Requirements
4.1 Secure PIN Generation
4.2 PIN Block Format and Usage
4.3 PIN Encryption Methods
4.4 PIN Transmission Protection
4.5 PIN Entry Device (PED) Requirements
4.6 PIN Verification Process
4.7 PIN Decryption and Handling
5. PCI-PIN Requirements Mapping
5.1 Alignment with PCI PIN Security Requirements
5.2 Key Management for PINs (Requirement 18)
5.3 PIN Translation and Distribution (Requirement 19)
5.4 PIN Processing Environment
5.5 Approved Cryptographic Algorithms (Requirement 20)
5.6 Secure Cryptographic Device (SCD) Usage
6. Hardware Security Module (HSM) Management
6.1 HSM Setup and Configuration
6.2 HSM Certification Requirements
6.3 HSM Key Generation and Storage
6.4 HSM Audit Logs
6.5 HSM Key Deletion and Re-keying
6.6 HSM Backup and Redundancy
7. Cryptographic Algorithm Usage
7.1 Approved Algorithms for PIN Encryption
7.2 Algorithm Strength and Usage Guidelines
7.3 Cryptographic Library Updates and Patches
7.4 Deprecated Algorithms and Transition Guidelines
8. Secure Key Distribution
8.1 Key Distribution Methods
8.2 Secure Electronic Distribution Mechanisms
8.3 Secure Transport for Key Material
8.4 Key Distribution to Third-Party Providers
8.5 Remote Key Loading (RKL) Requirements
9. Monitoring and Auditing of Key and PIN Management
9.1 Key Usage Monitoring
9.2 Log Management and Audit Trails
9.3 Audit Requirements
9.4 Incident Response for Key Management Breache
9.5 Reporting of Cryptographic and Key Events
10. Incident Response and Key Compromise Procedures
10.1 Key Compromise Protocol
10.2 Procedures for Cryptographic Breach
10.3 Reporting of Incidents to Regulators
10.4 Incident Analysis and Mitigation
11. Compliance and Risk Management
11.1 PCI-DSS and PCI-PIN Compliance Requirements
11.2 Key Management Risk Assessments
11.3 Third-Party Risk Assessment
11.4 Compliance Monitoring
11.5 Periodic Review and Policy Updates
12. Training and Awareness
12.1 Training Requirements for Key Custodians and Officers
12.2 Cryptographic Awareness Training
12.3 Annual Compliance and Refresher Training
13. Policy Review and Maintenance
13.1 Frequency of Review
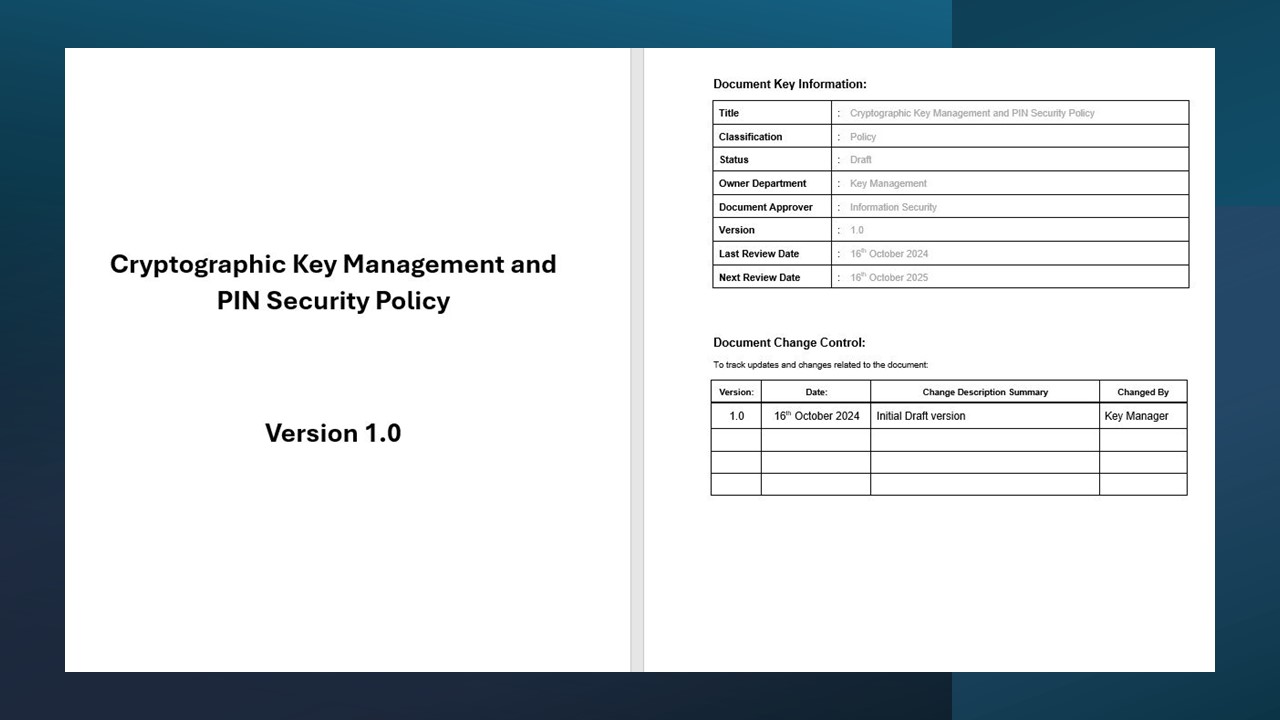
13.2 Document Control and Versioning
13.3 Stakeholders Involved in Policy Updates
13.4 Approval Process for Changes
14. References and Appendices
14.1 PCI-PIN Security Requirements References
14.2 Glossary of Key Terms
14.3 Acronyms
14.4 Appendix A: Key Management System Diagram
14.5 Appendix B: Key Escrow and Compromise Reporting Templates
A. Key Escrow Request Form
B. Key Compromise Reporting Template
All GovernanaceDocs documents are developed based on well-known standards such as NIST CSF, ISO 27001, ISO 22301, PCI-DSS and HIPAA.
Hence, You just need to download and selected document and add your company name and logo.




















Reviews
There are no reviews yet.