Malware Attack Procedure Template
Introducing our Malware Attack Procedure Template, a comprehensive resource designed to assist organizations in effectively responding to and mitigating malware attacks.
In today’s digital landscape, malware poses a significant threat to businesses of all sizes, compromising sensitive data, disrupting operations, and causing financial losses.
Our template provides a step-by-step guide to help your organization navigate through the complexities of a malware attack, enabling a swift and efficient response. Key features of our Malware Attack Procedure Template include:
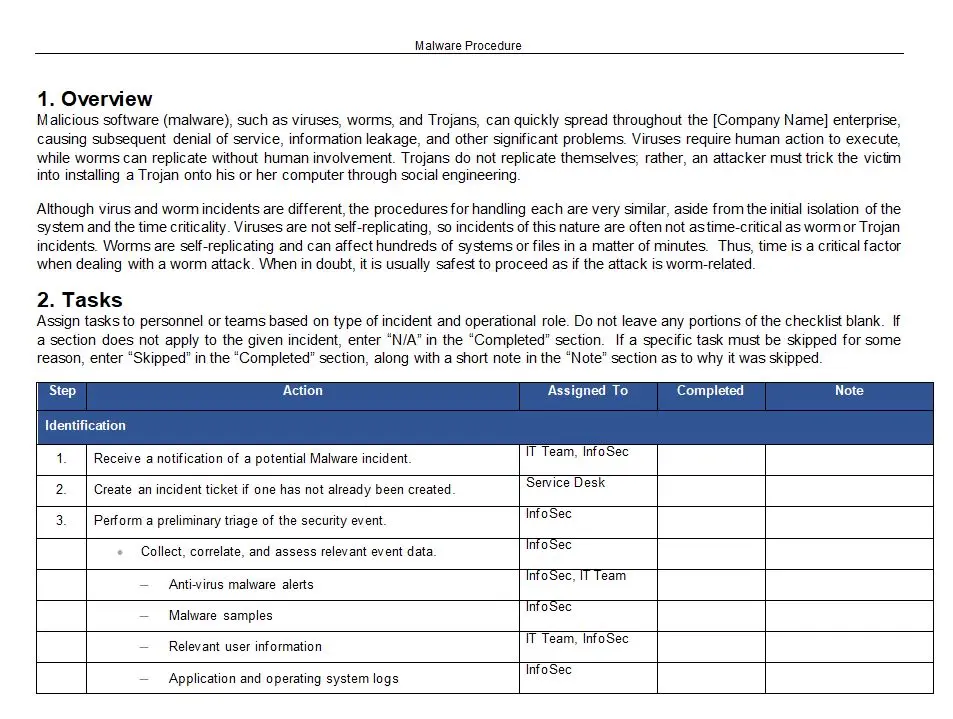
1. Incident Detection and Reporting: Clear guidelines on how to identify the signs of a malware attack and report it to the appropriate channels within your organization promptly.
2. Incident Assessment and Triage: Establishing a structured approach to assess the severity and impact of the malware attack, enabling your team to prioritize response efforts effectively.
3. Containment and Isolation: Providing instructions on how to isolate affected systems, contain the spread of malware, and prevent further damage to your network and data.
4. Incident Response Team Roles and Responsibilities: Defining the roles and responsibilities of key personnel involved in the incident response, ensuring a coordinated and effective effort.
5. Malware Analysis and Identification: Offering guidance on conducting a thorough analysis of the malware to understand its characteristics, behavior, and potential vulnerabilities it exploits.
6. Remediation and Recovery: Outlining a systematic process for removing malware, restoring affected systems, and implementing measures to prevent future attacks.
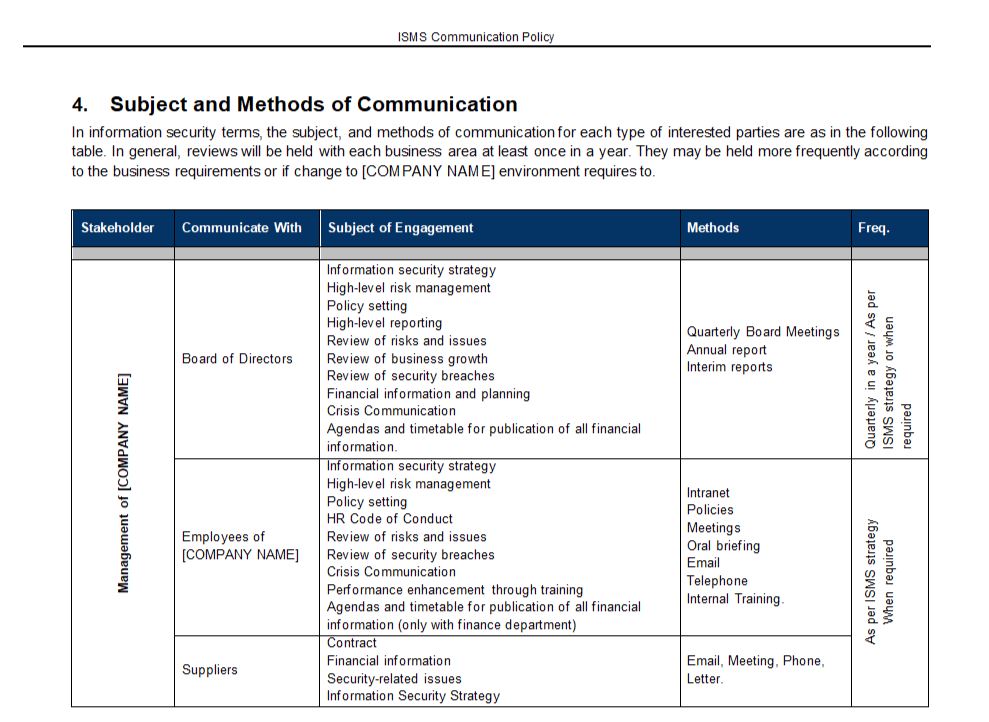
7. Communication and Notification: Providing a framework for communicating with stakeholders, including employees, customers, and regulatory bodies, about the incident and the steps taken to address it.
8. Lessons Learned and Prevention Measures: Encouraging a proactive approach to learning from the incident by conducting post-incident reviews, documenting lessons learned, and implementing preventive measures to enhance your organization’s security posture.
By utilizing our Malware Attack Procedure Template, you can strengthen your organization’s ability to respond swiftly and effectively to malware attacks, minimizing damage and reducing downtime. With clear instructions and guidelines at your fingertips, you can confidently navigate the complex landscape of malware threats.
Don’t let malware compromise your valuable assets and disrupt your business operations. Invest in our Malware Attack Procedure Template today and ensure that your organization is well-prepared to defend against and recover from any malware attack.
Number of Pages: 10
A step by step procedure document describe the steps required in the case of Malware attack.
All GovernanaceDocs documents are developed based on well-known standards such as NIST CSF, ISO 27001, ISO 22301, PCI-DSS and HIPAA.
Hence, You just need to download and selected document and add your company name and logo.








AvaMiller –
The templates are well worth the investment. They’ve made document creation a breeze, and the end results look fantastic. Great job!
AvaBrown –
I couldn’t be happier with these document templates. They’ve made a significant difference in our efficiency and document quality.
BenjaminSmith –
I’m beyond impressed with the quality of these document templates. They cover all the necessary details and are regularly updated.
LiamMiller –
I couldn’t be happier with these document templates. They’ve made a significant difference in our efficiency and document quality.