ISMS Procedure for the Management of Nonconformity
In the ever-evolving landscape of information security, where threats loom large and the stakes are higher than ever, organizations must navigate a complex web of standards and protocols to safeguard their data. At the heart of this intricate dance lies the ISMS Procedure for the Management of Nonconformity, a beacon of assurance for those striving to meet the rigorous demands of ISO 27001.
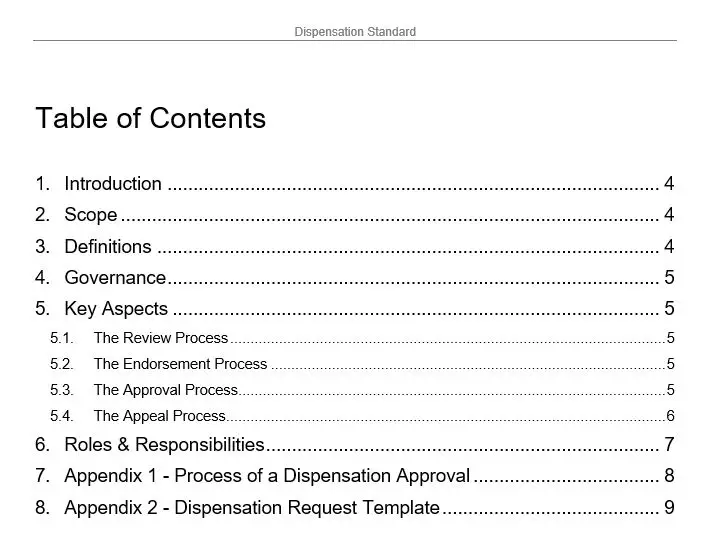
This procedure, identified by the number 8022, is not just a document; it is a lifeline for organizations committed to maintaining the integrity of their Information Security Management System (ISMS). It meticulously outlines a process to identify and manage nonconformities, ensuring that any deviation from the established standards is swiftly addressed. This is not merely about compliance; it is about fortifying the very foundation of an organization’s information security framework.
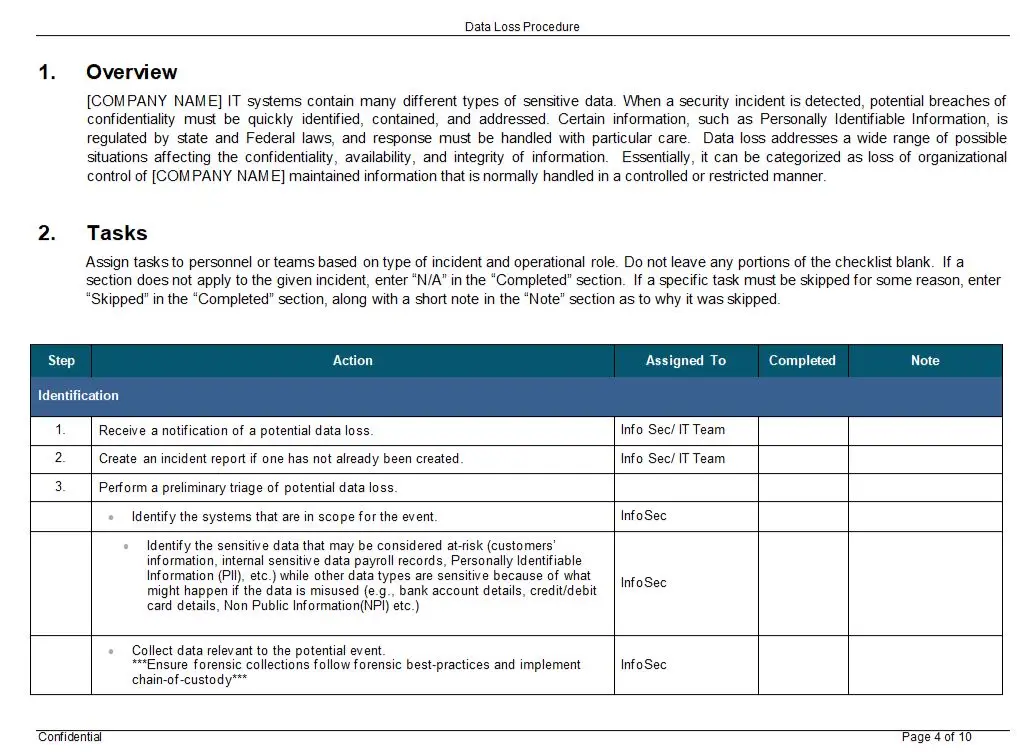
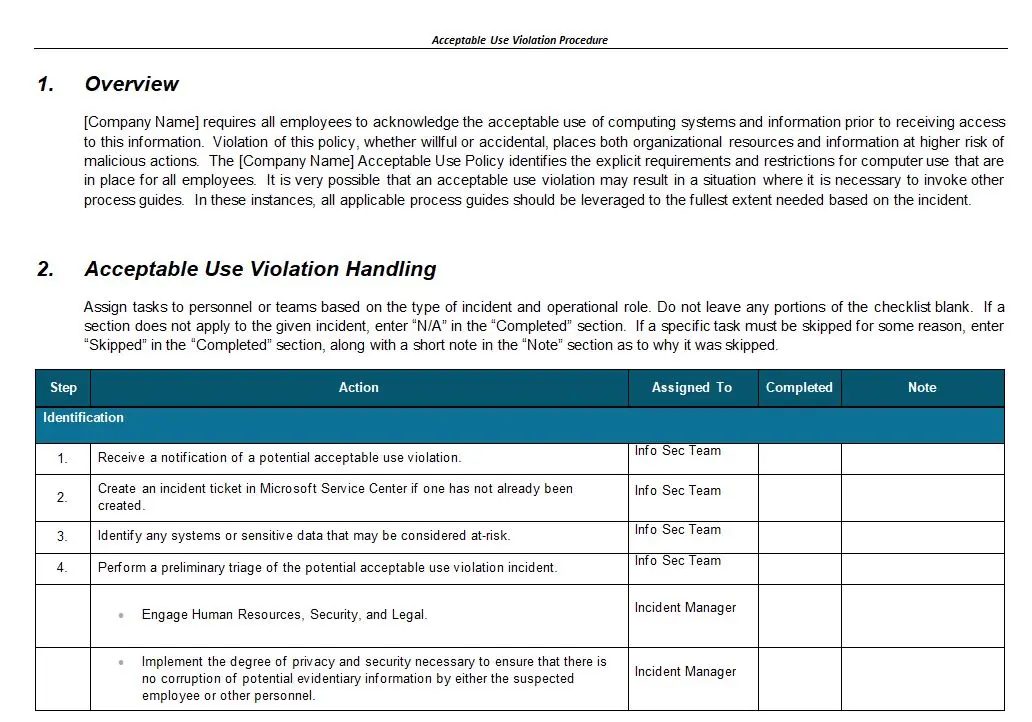
The key features of this procedure are its precision and comprehensiveness. It provides a clear roadmap for identifying nonconformities, whether they arise from internal audits, external assessments, or day-to-day operations. Once identified, the procedure ensures that these nonconformities are not just logged and forgotten but are actively managed through a structured process of corrective actions. This proactive approach is crucial in preventing minor issues from snowballing into significant security breaches.
The benefits of implementing the ISMS Procedure for the Management of Nonconformity are manifold. Firstly, it instills a culture of continuous improvement within the organization. By regularly identifying and addressing nonconformities, organizations can refine their processes, enhance their security posture, and stay ahead of potential threats. Secondly, it provides peace of mind to stakeholders, demonstrating a commitment to maintaining the highest standards of information security. This can be a significant differentiator in a competitive market where trust and reliability are paramount.
Moreover, the value proposition of this procedure extends beyond mere compliance. It is a strategic tool that empowers organizations to not only meet but exceed the requirements of ISO 27001. By embedding this procedure into their ISMS, organizations can transform nonconformity management from a reactive task into a proactive strategy, turning potential vulnerabilities into opportunities for growth and innovation.
In the realm of Information Security and ISO 27001, the ISMS Procedure for the Management of Nonconformity stands as a testament to an organization’s dedication to excellence. It is a vital component of the broader category of All Products, serving as a cornerstone for those who understand that true security is not a destination but a journey. With this procedure in place, organizations can confidently navigate the complexities of information security, secure in the knowledge that they are equipped to handle whatever challenges may arise.
All GovernanaceDocs documents are developed based on well-known standards such as NIST CSF, ISO 27001, ISO 22301, PCI-DSS and HIPAA.
Hence, You just need to download and selected document and add your company name and logo.







Reviews
There are no reviews yet