Event Logging and Monitoring Policy
In the ever-evolving landscape of information security, where threats loom large and data breaches can spell disaster, the Event Logging and Monitoring Policy emerges as a beacon of vigilance and resilience. This policy is not just a document; it is a comprehensive framework designed to safeguard the digital fortress of any organization. With the product code 8022, it stands as a testament to the commitment to security and compliance, aligning seamlessly with the rigorous standards of ISO 27001.
At its core, the Event Logging and Monitoring Policy establishes robust procedures for logging and monitoring security events. It is a meticulously crafted blueprint that empowers organizations to detect and respond to incidents with precision and agility. In a world where every second counts, this policy ensures that no anomaly goes unnoticed, no threat remains unchallenged.
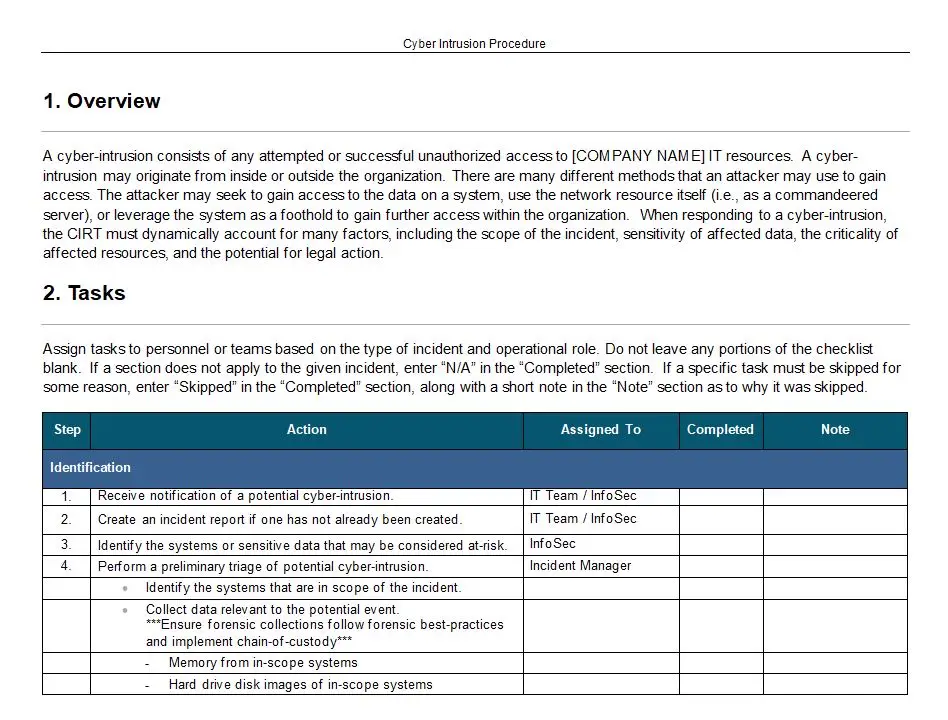
Key features of this policy include a systematic approach to capturing and analyzing security events. It mandates the implementation of advanced logging mechanisms that record every significant action within the IT infrastructure. From user logins to data access attempts, every digital footprint is meticulously documented, creating a comprehensive audit trail that serves as a powerful tool for forensic analysis.
But logging is only the beginning. The true strength of the Event Logging and Monitoring Policy lies in its monitoring capabilities. It employs cutting-edge technologies to continuously scrutinize the logged data, identifying patterns and anomalies that could indicate potential security breaches. This proactive approach allows organizations to stay one step ahead of cyber threats, mitigating risks before they escalate into full-blown incidents.
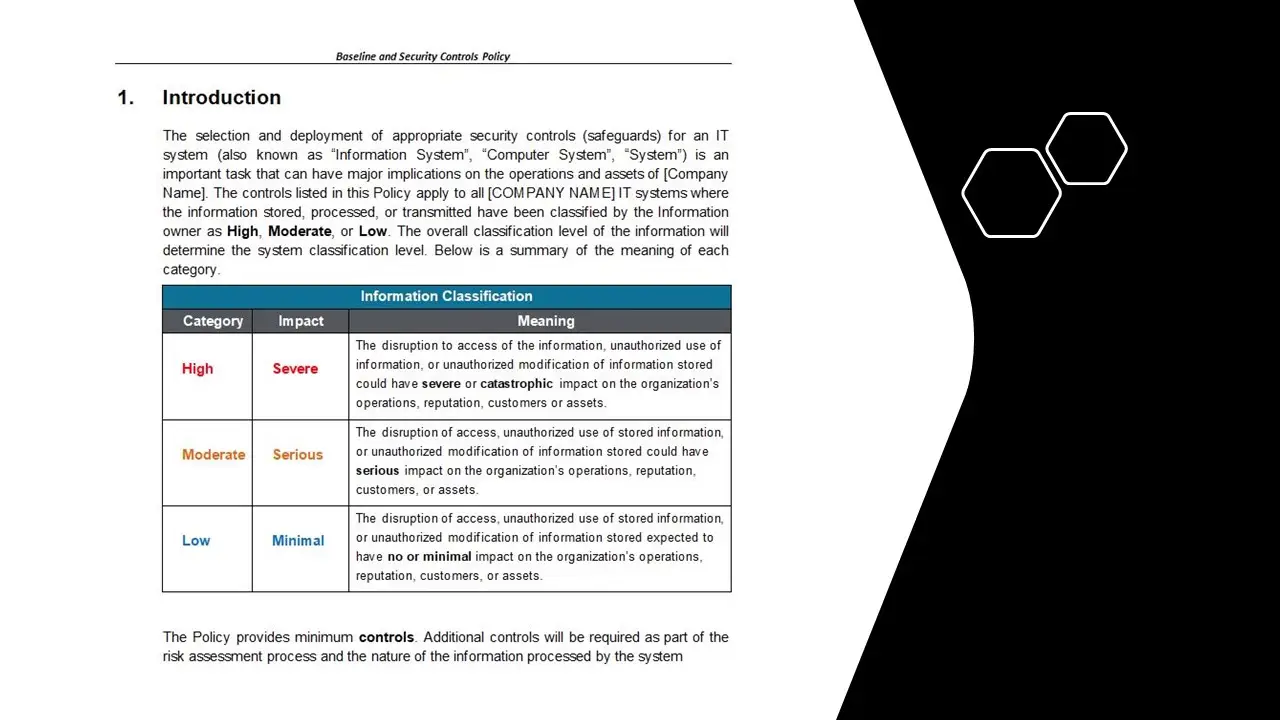
The benefits of implementing this policy are manifold. First and foremost, it enhances the organization’s ability to detect and respond to security incidents in real-time. By providing a clear and structured process for incident management, it minimizes response times and reduces the potential impact of breaches. Moreover, it ensures compliance with ISO 27001, a globally recognized standard for information security management, thereby bolstering the organization’s reputation and credibility.
The value proposition of the Event Logging and Monitoring Policy is undeniable. It offers peace of mind in an uncertain digital world, assuring stakeholders that their data is protected by a vigilant and responsive security framework. It empowers organizations to transform security from a reactive necessity into a proactive strategy, turning potential threats into opportunities for improvement and growth.
In the realm of information security, where the stakes are high and the challenges are ever-present, the Event Logging and Monitoring Policy is an indispensable ally. It is a testament to the power of foresight and preparedness, a vital component of any comprehensive security strategy. As part of the broader categories of All Products, Information Security, and ISO 27001, it stands as a cornerstone of digital resilience, ready to defend against the unseen adversaries of the cyber world.
All GovernanaceDocs documents are developed based on well-known standards such as NIST CSF, ISO 27001, ISO 22301, PCI-DSS and HIPAA.
Hence, You just need to download and selected document and add your company name and logo.








Reviews
There are no reviews yet