Data Protection Policy
The documents are created in Microsoft Office format and are ready to be customized to your organization’s applicable law. The Data Protection Policy template documents help you comply with the applicable local Data Protection Laws and/or GDPR. You just need to fill the marked fields with the appropriate information.
This document is written by a CISSP-qualified auditor with over 30 years of experience in Information Security, our template provides a wealth of expertise and knowledge in an easy-to-use format.
With an emphasis on quality and details, this template covers everything an organization needs to establish a robust Data Protection Policy. It serves as a critical tool for ensuring compliance with data protection regulations and fostering continuous improvement in your data management practices.
This pack has been created by GovernanceDocs to align with the highest standards in Data Protection.
Number of Pages: 28
Table of Content:
1. Introduction
2. Scope of the Policy
3. Legal framework
4. Definitions
5. Principles of Data Protection
6. Data Inventory
7. Handling Special Categories of Personal Data
8. Consent
9. Roles and responsibilities
10. Transfer of Personal Data
11. International transfer of Personal Data
12. Reporting Security Incidents
13. Data Sharing to Public Authorities
14. Disclosures to Data Subject
15. Data Retention and Erasure
16. Personal Data Breach
17. Cookies
18. Data Subject Rights
19. Data Subject Personal Data Access Request
20. Disciplinary Action
16. Key Contacts
17. Enforcement
Schedule A – Data Retention and Erasure Schedule
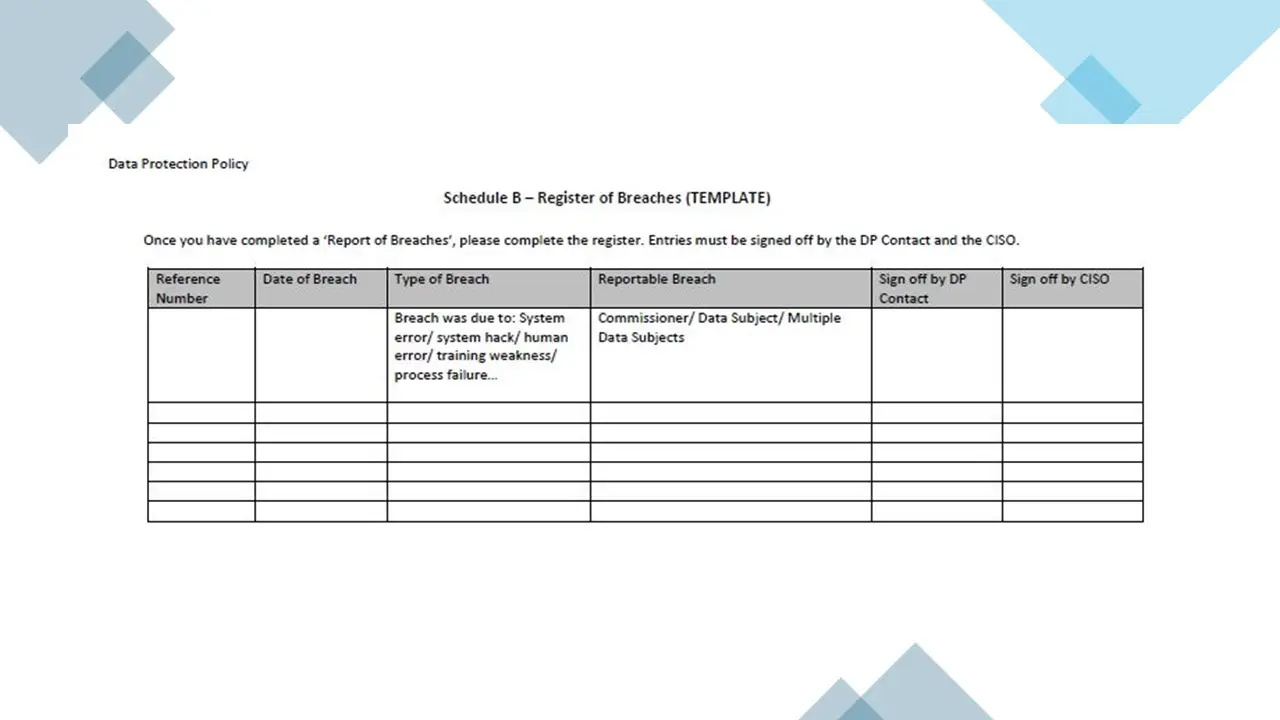
Schedule B – Register of Breaches (TEMPLATE)
Schedule C – Breach Report Template
All GovernanaceDocs documents are developed based on well-known standards such as NIST CSF, ISO 27001, ISO 22301, PCI-DSS and HIPAA.
Hence, You just need to download and selected document and add your company name and logo.




















Reviews
There are no reviews yet